Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating ports with nmap – getting 5 open ports. Checking out the webserver on port 80, we are forwarded to /issues.php. From here we are able to login as a guest and obtain usernames and hashed passwords by opening the attachment. Seeing that a user named hazard made a post, and we have passwords (which we cracked), we use lookupsid.py from Impacket to bruteforce SIDs to get other usernames on the box. Using a WinRM exploit, we are able to get a shell on the box as chase where we get user.txt. Enumerating the box, we see Firefox is running. We then dump its memory to get the credentials of administrator. Using these credentials, we log back in through WinRM to get root.txt.
Enumeration
Like all machines, we begin by enumerating open ports with nmap. Doing so, we see there are 5 ports open.
# Nmap 7.80 scan initiated Fri Sep 20 09:13:31 2019 as: nmap -p 80,135,445,5985,49668 -A -oA scans/nmap-tcp-scripts 10.10.10.149
Nmap scan report for 10.10.10.149
Host is up (0.055s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49668/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -13m46s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-09-20T14:00:46
|_ start_date: N/A
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 54.78 ms 10.10.14.1
2 55.19 ms 10.10.10.149
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 20 09:15:12 2019 -- 1 IP address (1 host up) scanned in 100.81 seconds
Getting User
Going to the webserver on port 80, we are redirected to http://10.10.10.149/login.php. Here we are presented with a login interface where we have an option to login as guest.

Presented with a login interface where we can login as guest
Clicking the option to login as guest, we are redirected to http://10.10.10.149/issues.php, where we can read a chat thread between Hazard and Support Admin. We also see Hazard uploaded an attachment for what we assume is a Cisco router configuration. Opening the attachment, we can see the router configuration, as well as potential usernames, and hashed passwords. Using hashcat and the web, we are able to crack these.
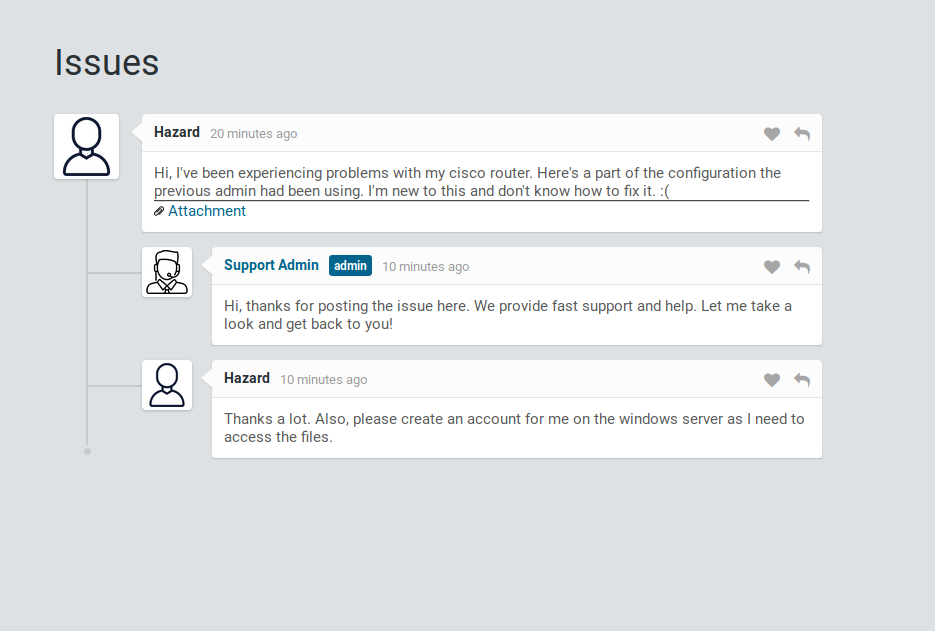
Logging in as guest forwards us to the issues page 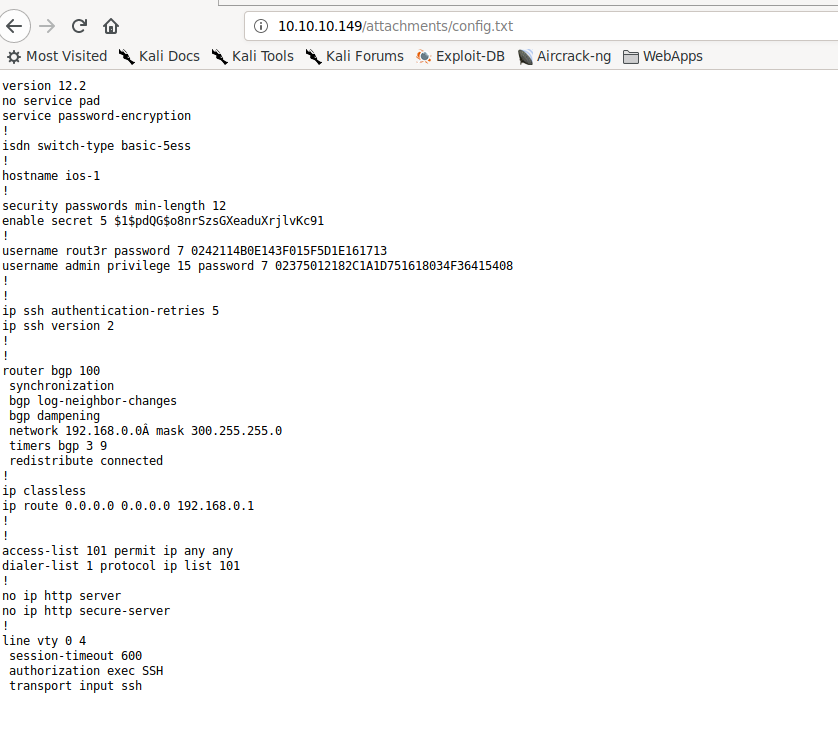
Opening the attachment returns a router config with credentials
Because we now have potential usernames and passwords, we can attempt to bruteforce further usernames from the system. To accomplish this, we can use Impacket’s lookupsid.py. This tells us there are 3 other users on the machine – support, Chase, and Jason.
lookupsid.py hazard@10.10.10.149
#password plaintext of $1$pdQG$o8nrSzsGXeaduXrjlvKc91
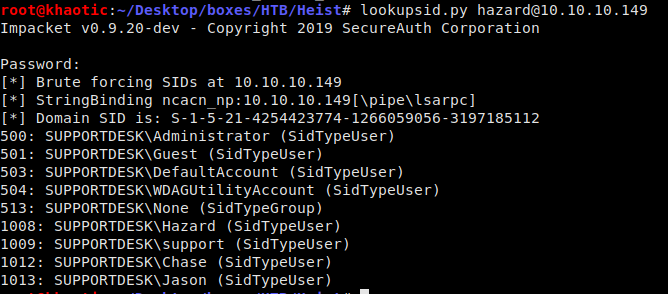
Bruteforce enumerating user accounts
Now that we have found additional usernames for the system, we are able to use WinRM on port 5985 to get a shell on the box as Chase. After doing so, we are able to read the contents of user.txt.

Got a WinRM shell and can read user.txt
Getting Root
Looking at the running processes on the machine, we see that Firefox is running. By uploading procdump (SysInternals) to the machine, we can dump the memory of the process to potentially get more information. Because we aren’t sure which process would have what we need, we can start by dumping the one with the highest CPU usage.

List running processes 
Dumping the process memory
Remembering the request parameters to the login interface from the webserver, we can grep the memory dump for login_username= to try to gain additional credentials.
cat dump.dmp | select-string login_username=
Doing so, we have retrieved the credentials for an admin user.

Retrieved the admin creds from the memory dump
Trying the password for the administrator user, we are able to get another WinRM shell and get root.txt.

Got a root shell and can read root.txt
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!